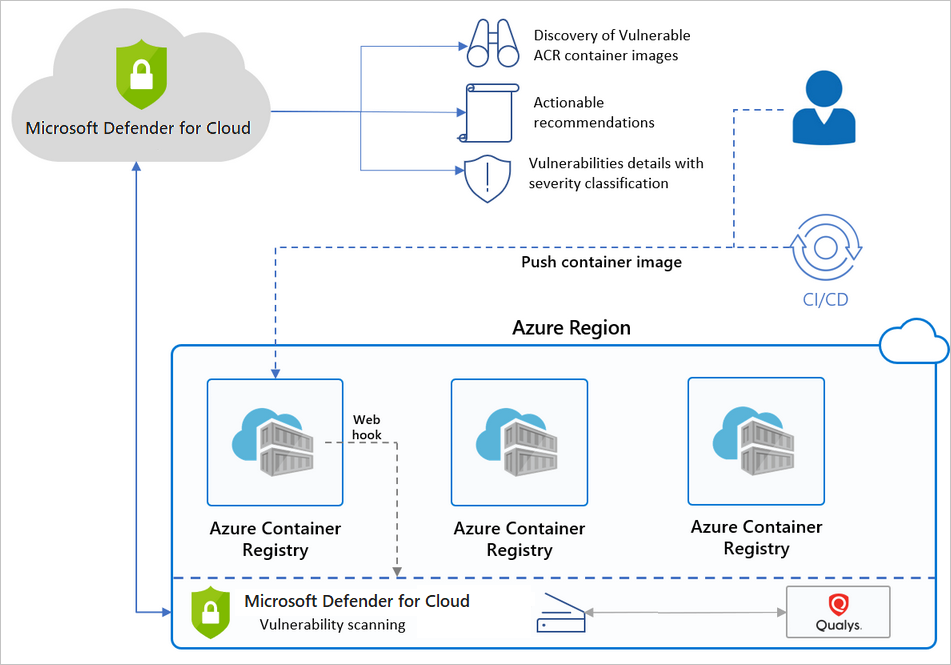
Azure Container Registry is Microsoft's private Docker registry. Think Docker Hub, but it costs money and doesn't go down randomly. If you're already on Azure and tired of hitting Docker Hub's rate limits, ACR might save your sanity.
The Three Tiers (And When to Use Them)
ACR has three tiers that'll confuse you at first:
Basic ($5/month) gets you 10GB storage and handles 1,000 pulls per minute. Perfect for side projects and learning. I used this for 6 months before hitting the storage limit.
Standard ($20/month) bumps you to 100GB and 3,000 pulls/minute. This is where most production apps land. The pricing jump hurts but the performance difference is real.
Premium ($30+/month) gives you 500GB, 10,000 pulls/minute, and fancy features like geo-replication. Only worth it if you're deploying globally or have strict compliance requirements.
Storage beyond the included amounts costs $0.10/GB per month - that adds up fast with large images.
Why ACR Actually Works (Most of the Time)
The only reason to use ACR is if you're already balls-deep in Azure. Your AKS clusters can pull images without credential juggling thanks to managed identity. It just works, which is rare enough in the container world to matter.
ACR Tasks builds your images in the cloud, triggered by Git commits or base image updates. Costs $0.000167 per CPU-second, which sounds cheap until you're building massive Node.js projects with 500MB node_modules folders. I've seen builds that cost $2 each.
The vulnerability scanning found 200+ issues in our production images. Turns out using node:latest was a terrible idea. The scanner integrates with Microsoft Defender and actually provides useful remediation steps.

Authentication: Where Things Get Complicated
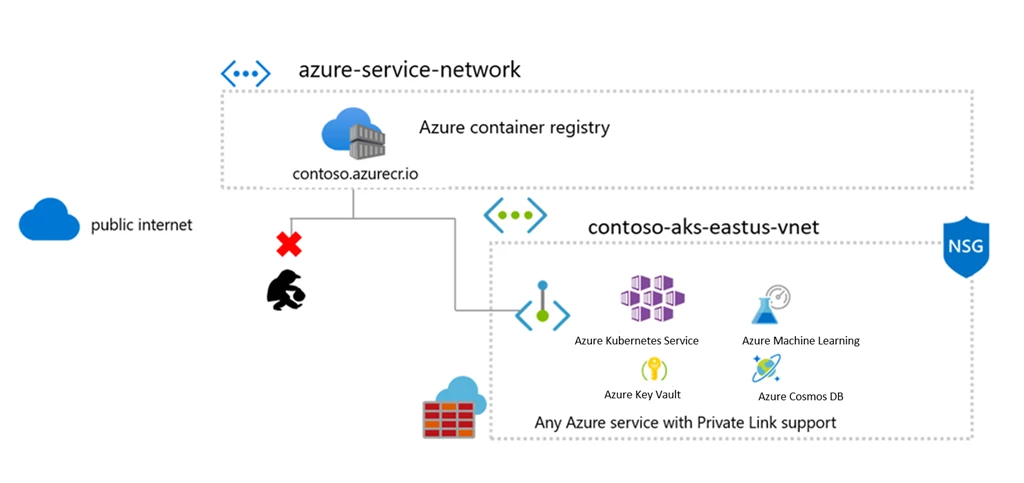
Authentication works fine if you're all-Azure. For everything else, it's a nightmare:
az acr login --name myregistryworks until it doesn't- Service principals expire and break your CI/CD
- Non-Azure systems need token juggling that'll make you question your life choices
I spent 3 hours debugging why our Jenkins couldn't push images. The answer? The service principal credentials expired. ACR gives you zero warning about this - just a useless "authentication failed" error message. This Stack Overflow thread covers the most common auth issues you'll hit.
For non-Azure CI/CD systems, check the Azure/acr GitHub repo for troubleshooting tips and known issues. The community there has documented most of the edge cases you'll encounter.
What You'll Actually Use ACR For
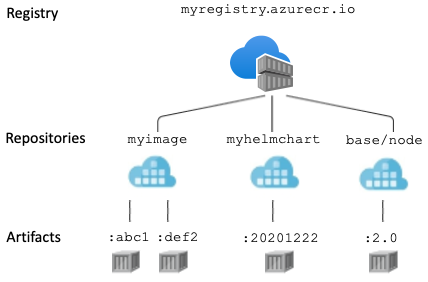
- Private base images: Custom Ubuntu/Alpine images with your company's tooling
- Microservice storage: Dozens of small services that change constantly
- ML model artifacts: Storing trained models alongside your inference containers
- Helm charts: OCI artifact support means you can store Helm charts too
The geo-replication feature saved us when East US went down for 6 hours. Images pulled from West US automatically. But it doubles your storage costs, so budget accordingly.
If you're coming from Docker Hub, the official migration guide walks through importing existing images. The Docker Hub rate limiting changes in 2020 drove a lot of teams to ACR - and for good reason.