You know what wakes you up in the middle of the night? A Slack alert at 2:47 AM saying "CRITICAL: API gateway returning 500s, customers can't login" and it was our fault. That was my introduction to container security - watching our staging environment get owned because we were running some PHP 7.4 container with CVE-2021-21704 that had been public for months.
Every Docker image is a house of cards built on someone else's software. Your innocent FROM node:16 brings 847 dependencies you've never heard of. That Ubuntu base image? It ships with systemd, a full SSH server, and about 200 packages you'll never use but attackers definitely will. I've seen production systems taken down by vulnerabilities in libssl that nobody even knew was installed.
Here's what actually happens when you don't scan containers: You inherit every security hole from every layer of your image. The Log4Shell vulnerability took down half the internet because everyone was running Java containers with vulnerable logging libraries they didn't even know they had. One company I worked with had 1,247 containers in production - every single one vulnerable to remote code execution through a logging library we didn't even know existed. The 2025 container scanning landscape shows we still haven't learned from these mistakes.
How We Got Here (And Why It Took So Long)
Container security went from "we'll deal with it later" to "holy shit, we're getting pwned" real fast between 2020-2025. Early on, everyone was so excited about being able to deploy stuff quickly that security was "someone else's problem." Then the breaches started.
First, someone compromised a bunch of popular Docker Hub images and injected crypto miners. Then SolarWinds happened and suddenly everyone realized their supply chain was completely compromised. More recently, over 70 malicious npm packages were discovered in May 2025, and the popular nx package was compromised just days ago. Turns out when you pull random packages from the internet and run them in production, bad things happen.
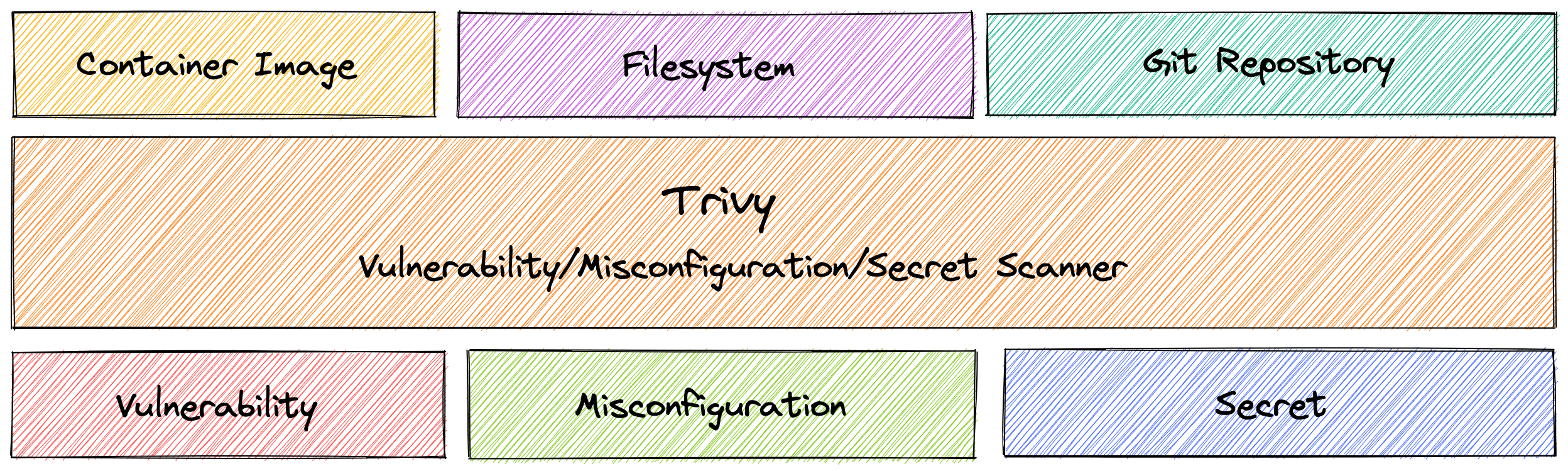
The tools got better because they had to - companies were getting owned left and right. Trivy became the go-to scanner because it actually works and doesn't require you to sell your firstborn to Aqua Security for a license. Docker Scout showed up and made scanning so easy that even product managers could understand it. Enterprise platforms like Snyk started charging per-developer because that's how SaaS companies work now. Current benchmarks show Trivy still leads in accuracy while Snyk wins on developer experience - for a price.
"Shift-left security" is just fancy talk for "catch this before it breaks production." Because fixing vulnerabilities after you've deployed them sucks and you'll be doing it at 3 AM when everything's on fire.
What These Things Actually Do
Finding Vulnerabilities (The Obvious Part)
Scanners look at every package in your container and check if it's vulnerable. That Node.js base image you're using? It's got dozens of npm packages with known CVEs. Your Ubuntu container? The apt package manager has a vulnerability that lets attackers execute arbitrary commands. Scanners cross-reference everything against the National Vulnerability Database and scream at you when they find problems. Modern tools like Trivy combine multiple data sources including Alpine SecDB, GitHub advisories, and distro-specific trackers for more complete coverage.
Catching Your Terrible Configuration Choices
Ever run a container as root because it was easier? Scanners will find that. Left port 22 open for "debugging"? They'll catch that too. The CIS Docker Benchmark has over 100 ways to screw up container security, and scanners check for most of them. Resource limits? They'll tell you when you forgot those and someone can DOS your entire cluster.
Supply Chain Paranoia (Justified)
Modern scanners generate Software Bill of Materials (SBOM) because compliance people demand it and because your dependencies are sus. That random npm package with 12 weekly downloads? It might be malware. Scanners track every library, every version, every transitive dependency, and flag anything that looks sketchy.
Secret Detection (Because Developers Are Terrible)
You hardcoded your AWS keys in the Dockerfile again, didn't you? Scanners find API keys, database passwords, certificates, and other secrets you accidentally baked into your images. They use pattern matching because developers have zero creativity when it comes to hiding secrets.
Where to Stick These Scanners
In Your IDE (If You're Feeling Ambitious)
Docker Desktop has scanning built in now, which is nice until you realize it only scans 3 images for free. VS Code has Trivy and Snyk extensions that will yell at you in real-time. Most developers ignore these because they're trying to ship code, not debug dependency trees.
CI/CD Pipeline (Where It Actually Matters)
This is where the magic happens. GitHub Actions can fail your build when it finds critical vulnerabilities. GitLab will block your merge request. Jenkins will make your build red and everyone will blame you. Set your CVSS threshold too low and nothing will ever deploy. Set it too high and you'll ship containers with remote code execution vulnerabilities. Run scans early and often, or you'll be fixing vulnerabilities at 3am when production is on fire.
Registry Scanning (The Safety Net)
Every major registry scans images now. Docker Hub scans for free (limited), Amazon ECR uses Inspector, Google Artifact Registry has Binary Authorization. This catches images you didn't build yourself, like that sketchy Python image your intern pulled from Docker Hub.
Kubernetes Admission Controllers (For the Paranoid)
OPA Gatekeeper and Falco can block vulnerable containers before they run. Great in theory, until you realize your legacy applications fail every security policy and you end up allowlisting everything to keep the lights on.
The Scanner Landscape (Who to Trust)
By 2025, container scanners fell into the usual buckets: free shit that works great, expensive tools that work slightly better but make your CFO cry, and cloud provider tools that work fine if you don't mind vendor lock-in.
Open Source (Start Here)

- Trivy: The gold standard. Fast, accurate, supports everything. If you use one scanner, use this one.
- Grype: Good at SBOM generation, which compliance people love. Slower than Trivy but more thorough.
- Clair: Red Hat's scanner. Works well if you're already drinking the OpenShift Kool-Aid.
Commercial (For When You Have Budget)

- Snyk: Developer-friendly until you see the bill. Integrates with everything, charges per developer.
- Aqua Security: Enterprise-grade, enterprise-complex. Setup will make you question your life choices.
- Prisma Cloud: Palo Alto's attempt to own all of cloud security. Expensive and heavyweight.
- Sysdig: Good at runtime security, which is nice until you realize how resource-intensive it is.
Cloud Provider (Vendor Lock-In Edition)
- AWS ECR Enhanced Scanning: Uses Inspector, works well within AWS, costs add up quickly.
- Google Binary Authorization: Policy-based deployment controls that work great until you need to deploy something quickly.
- Azure Defender: Microsoft's security solution. It exists.
Start with Trivy. If you need enterprise features, evaluate Snyk. If you have compliance requirements, look at Aqua. If you're already all-in on a cloud provider, use their scanner. Don't overthink it. The 2025 container security tooling landscape confirms Trivy's dominance in the open-source space, with enterprise adoption trends favoring developer-first solutions like Snyk for teams with budget.
But knowing which tools exist is just the first step. The real pain in the ass is figuring out which one to actually use when they all claim to do the same thing (spoiler: they don't).

