Snyk Container scans your Docker images to find the security holes that'll get you paged at 3am. Part of the Snyk platform, it crawls through your container layers looking for vulnerable packages and dependencies.
Containers are mystery boxes full of vulnerabilities that'll bite you in production. You inherit whatever Alpine or Ubuntu base image you chose, plus every dependency your app pulls in, plus whatever crusty old packages came with that "latest" tag. Snyk Container rips apart these layers to show you exactly what's broken.
What It Actually Does
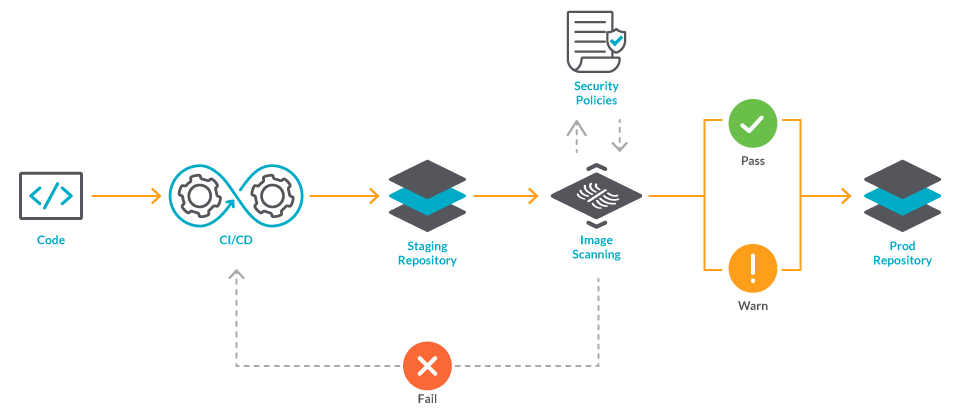
Layer-by-Layer Scanning: Snyk tears apart your Docker images to find vulnerabilities in your base OS, system packages, and application dependencies. Works with the usual suspects: Alpine, Ubuntu, Debian, CentOS, RHEL, and whatever other Linux distros you're running. Uses the CVE database plus Snyk's own vulnerability research.
Base Image Suggestions: When it finds vulnerable shit in your base image, Snyk suggests alternatives that won't get you pwned. Handy when you discover your node:16-alpine image has 47 critical CVEs and you need to switch to something that won't make your security team cry. Snyk maintains a curated list of secure base images that actually get security updates.
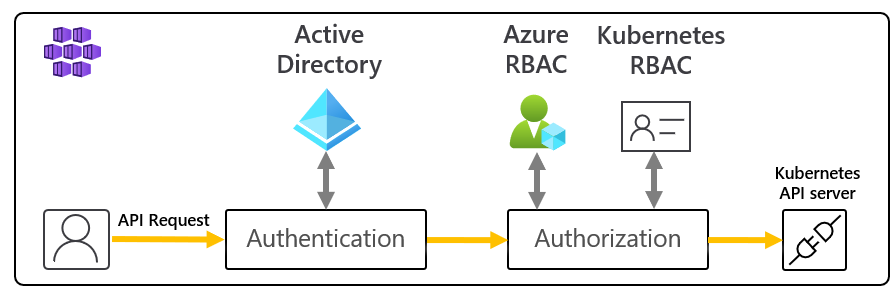
Kubernetes Scanning: Monitors your K8s clusters for containers running with known vulnerabilities. Because finding out your production pods are vulnerable after they're deployed is not a fun way to start your Monday. The Kubernetes integration uses agents to watch what's actually running, not just what you think is running.

CI/CD Integration: Plugs into your build pipeline through IDE extensions, Git hooks, and CI runners. Works with Jenkins, GitHub Actions, GitLab CI, and whatever other pipeline tool you're stuck with. Catches vulnerable images before they make it to production.
The pricing starts free with 100 container scans per month - sounds generous until your CI/CD pipeline burns through that in a week. Team plans run $25 per developer with unlimited scanning - so $250/month for a 10-person team because apparently finding vulnerabilities costs money. Enterprise pricing requires talking to sales, which nobody enjoys.
But pricing is just the start. Before you decide if Snyk Container is worth the cost, you need to understand how it stacks up against the competition - and there's some solid free alternatives that might save your budget.