So you've heard containerd is "the boring container runtime that Kubernetes uses" - but what does that actually mean for you? containerd is what happens when you rip out the container runtime from Docker and make it standalone. Docker Inc. extracted it years ago because everyone realized the fat Docker daemon was overkill for production Kubernetes. Now containerd handles the boring shit - starting containers, managing images, cleaning up when things die - while other tools handle the flashy stuff.
Why Kubernetes Ditched Docker (And Why You Should Know)
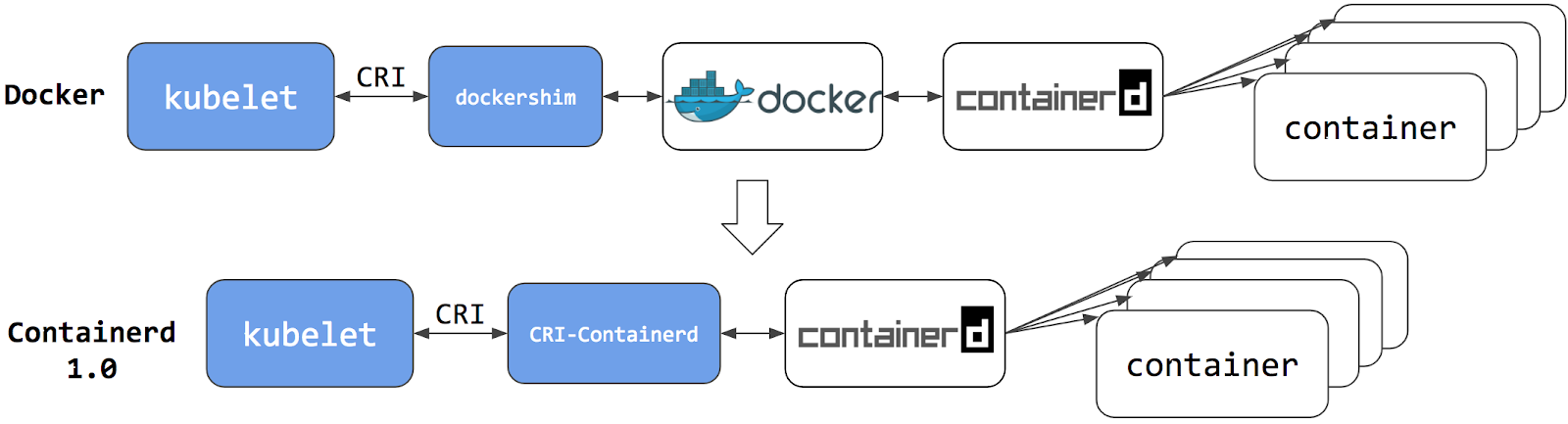
Back in 2020, Kubernetes announced Docker deprecation and everyone panicked. Turns out it was much ado about nothing - Kubernetes wasn't using Docker's fancy features anyway, just containerd underneath. So they cut out the middleman.
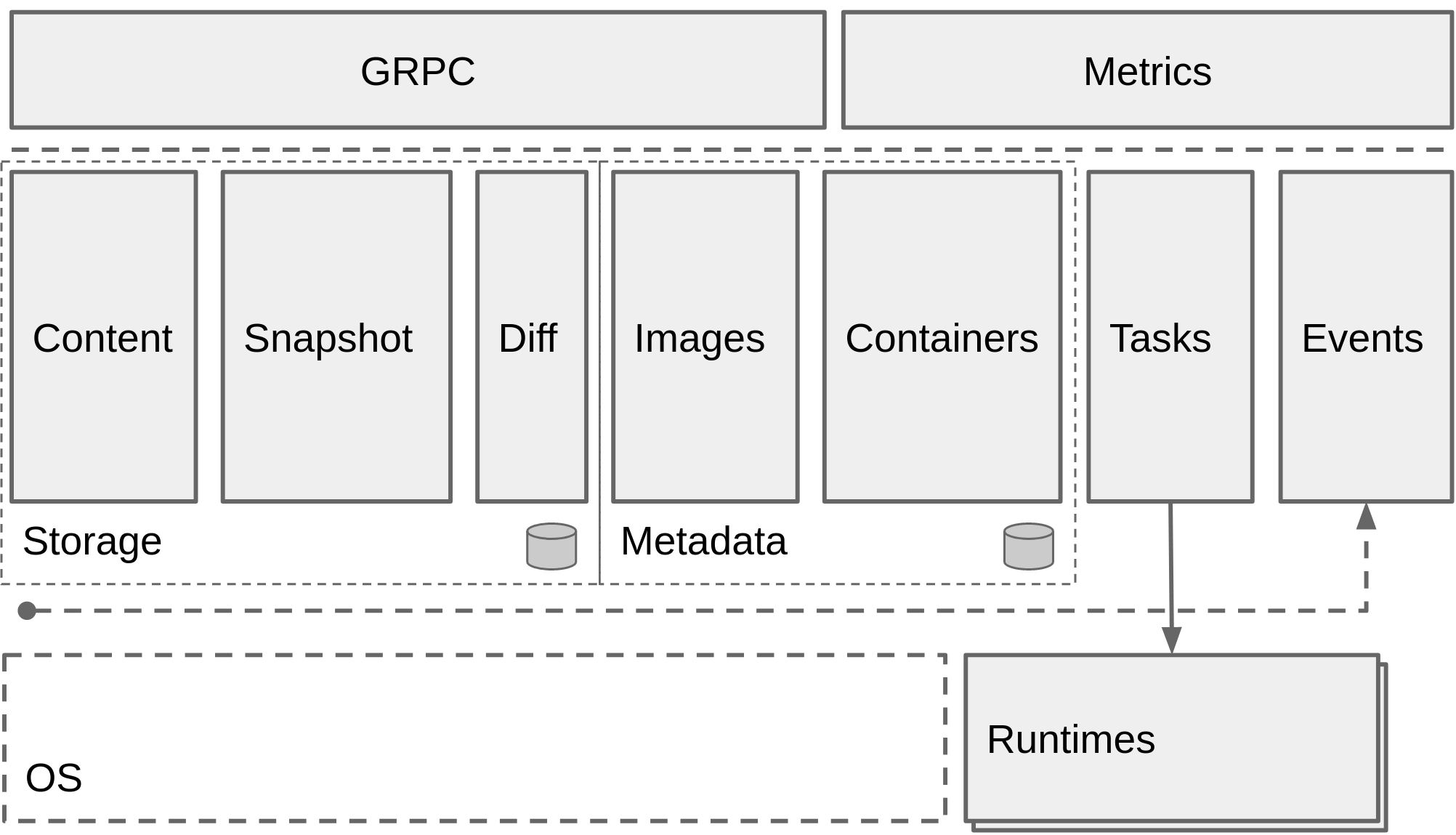
Here's how it actually works: containerd manages container lifecycle through a gRPC API, then hands off the actual container execution to runc. It's like having a manager (containerd) who delegates the real work to someone else (runc). The OCI Runtime Specification defines exactly how this handoff works. Boring but reliable.
What containerd Actually Does
containerd handles the unglamorous but critical parts:
- Image Management: Downloads and stores your bloated container images without bitching about disk space. Uses content-addressable storage to deduplicate layers.
- Container Lifecycle: Starts your containers fast, kills them when asked, cleans up the mess. The container lifecycle API is actually sane.
- Networking: Sets up basic networking then gets out of the way for CNI plugins to do the heavy lifting
- Storage: Copy-on-write filesystem snapshots so you're not copying 500MB base images around like an idiot. Multiple snapshotters available (overlayfs, zfs, btrfs).
- Security: Rootless containers, user namespaces, all the security theater that actually works
Current version is containerd 2.1.4 as of August 2025. The 1.7.x series is LTS until March 2026, so you have time to procrastinate upgrades. Note that the 2.x series introduced breaking changes in the config format and some API endpoints - test thoroughly before upgrading production systems.
Where You'll Actually Encounter This

Kubernetes: Every major cloud provider (AWS EKS, Google GKE, Azure AKS) switched to containerd. If you're deploying to managed k8s, you're using containerd whether you know it or not.
Local Development: Tools like nerdctl give you Docker-like commands (nerdctl run, nerdctl build) but with containerd underneath. It's for people who want Docker functionality without Docker Inc's increasingly hostile licensing.
Why It's Actually Better

containerd starts containers roughly 20-30% faster than Docker because there's less crap in the way. Memory usage is lower because it's not running a kitchen-sink daemon. These gains matter when you're spinning up thousands of containers, not so much for your 3-container development environment.
The CNCF graduated containerd, meaning it passed their bureaucracy test and won't randomly disappear. Big tech companies like Google, AWS, and Microsoft bet their infrastructure on it, so it's probably not going anywhere.
So containerd is clearly important and here to stay - but actually using it? That's where things get interesting. The theory is clean, but the practice has some sharp edges you need to know about.