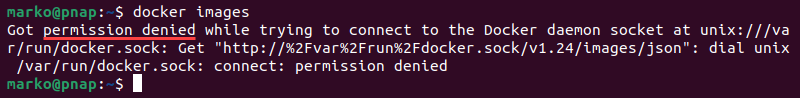
Docker's error messages are about as helpful as a chocolate teapot. When you get "permission denied while trying to connect to the Docker daemon socket at unix:///var/run/docker.sock" - that's Docker's way of saying "you're not special enough to run containers."
Here's the deal: Docker uses a Unix socket at /var/run/docker.sock for everything. This socket is owned by root and the docker group, with 660 permissions. If you're not in the docker group, you're screwed.


$ ls -la /var/run/docker.sock
srw-rw---- 1 root docker 0 Aug 25 10:15 /var/run/docker.sock
That socket belongs to root:docker with 660 perms. Translation:
- Root can do whatever
- docker group members can do whatever
- Everyone else: go cry
The Security Theater
Docker will lecture you about security while making you choose between convenience and safety. The Docker daemon runs as root and can mount your entire filesystem. Anyone with Docker access basically has root access anyway.
This isn't theoretical - here's how trivial it is to get root from Docker socket access:
docker run -v /:/host -it ubuntu chroot /host bash
## Congratulations, you're root on the host system
Don't just chmod 666 /var/run/docker.sock - you'll basically give everyone root access. Bad idea, even though half the tutorials on Stack Overflow suggest it. The official Docker docs tell you the right way, but they bury the important gotchas in technical details that nobody reads.
Platform-Specific Headaches
This permission bullshit shows up differently everywhere:
Linux: Direct socket permission drama with /var/run/docker.sock - different distros handle it differently
Docker Desktop (Mac/Windows): The app usually handles this automatically, but when it doesn't, you're debugging VM networking
WSL2: Permission mapping between Windows and Linux is a nightmare
CI/CD: Most just run everything as root because life's too short
I've hit this on Ubuntu 20.04, 22.04, and Arch - same fix every time. WSL2 permissions are even worse than regular Linux. Lost a weekend to this when Docker Desktop randomly stopped working on Windows 11.