Let's start with the elephant in the room: Weaveworks went belly-up in February 2024. Classic startup death spiral - burned through their cash and couldn't find more investors willing to throw money at a GitOps tool company. The TechCrunch obituary and CEO's LinkedIn farewell tell the full story. If you were paying for Weave GitOps Enterprise, that was a fun Monday morning email to receive.
The Good News: All the Expensive Shit is Now Free
Here's the silver lining to this corporate graveyard - all those enterprise features that cost thousands per month are now open source. Cluster fleet management, progressive delivery, policy enforcement - all of it. Dead companies can't charge licensing fees, and the CNCF community picked up the pieces.
The latest release v0.39.0-rc.2 shows the community isn't letting this die, but let's be honest about what community maintenance means: slower bug fixes, no guaranteed SLA, and you're dependent on volunteers who fix things when they feel like it.
What Weave GitOps Actually Is (No Marketing Bullshit)
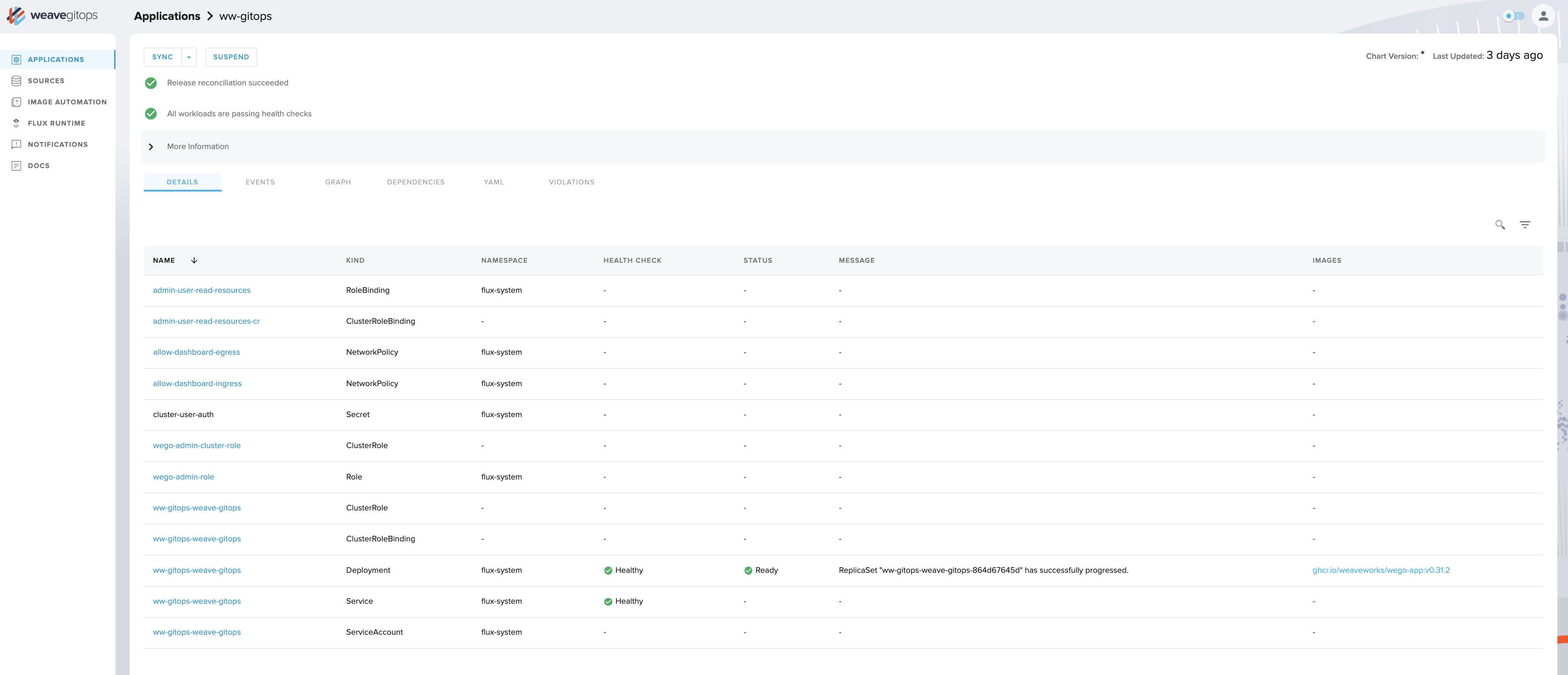
Weave GitOps is Flux with a web UI bolted on top. That's it. If you're comfortable living in kubectl and flux get all, you don't need this. But if your team includes people who break out in hives when they see a terminal, the web interface is actually useful.
It shows you what Flux is doing behind the scenes - which HelmReleases are stuck, which Kustomizations are failing, and why your deployment has been "Progressing" for the last 45 minutes. The UI also lets you trigger reconciliation manually, which beats the hell out of running flux reconcile commands all day.
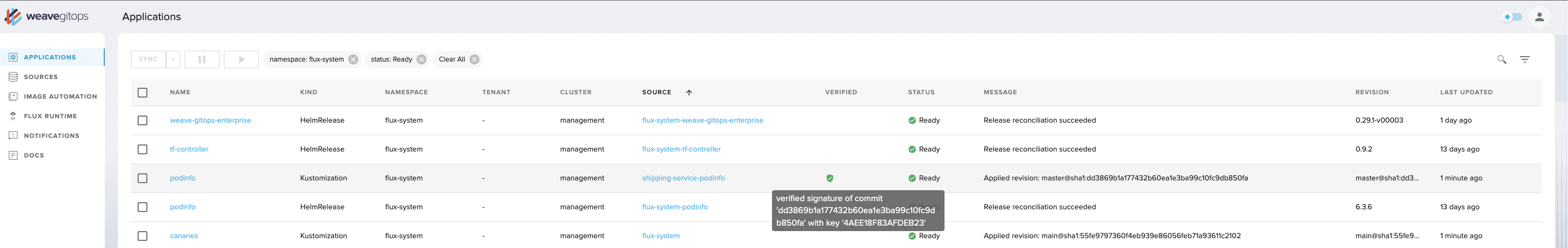
The Architecture Reality Check
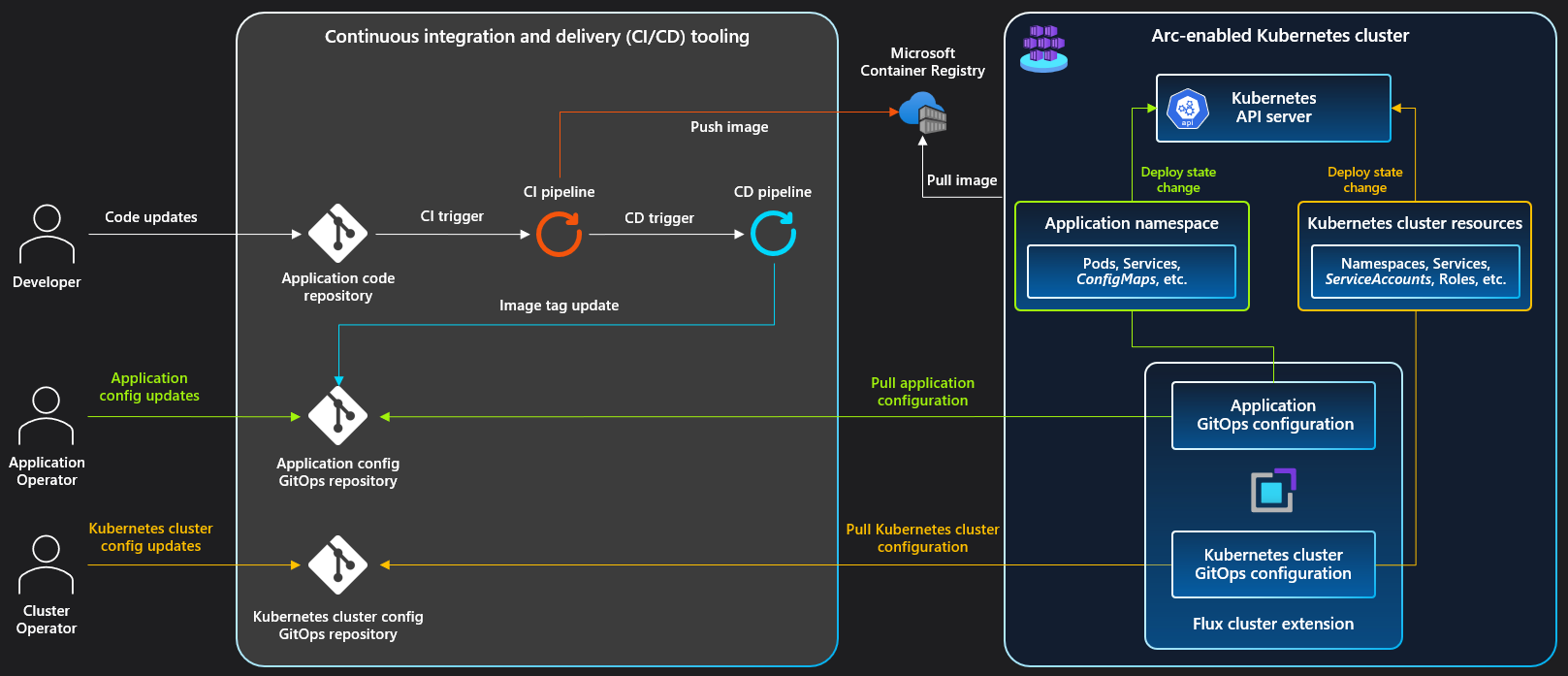
Under the hood, you're getting standard Flux v2 controllers: Source Controller, Kustomize Controller, Helm Controller, and Notification Controller. Weave GitOps adds a web dashboard and some CRDs for multi-cluster management.
The "simple three-component architecture" they love to tout breaks down to:
- Flux controllers doing the actual work (this is the important part)
- Weave GitOps dashboard showing you pretty pictures of what's happening
- CLI tool that's basically a wrapper around
fluxandkubectl
Don't let anyone tell you this is revolutionary. It's a decent UI for an existing tool.
Why It Still Matters (Despite the Company Dying)
The Flux integration is solid because it's literally just Flux. You're not betting on some proprietary GitOps engine - you're using the CNCF graduated project that's not going anywhere. If Weave GitOps completely dies tomorrow, you can rip out the UI and keep using Flux directly.
The real value is for teams who need GitOps but don't want to live in YAML hell. If your developers are more comfortable clicking buttons than debugging flux describe, this makes their lives easier. Just don't expect the polish of a tool backed by a living company.
But how does it stack up against the alternatives? Let's look at the brutal reality of debugging these tools when they break at 3am.