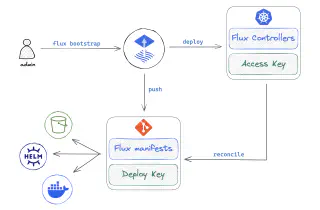
The traditional deployment model is a security nightmare. Your CI/CD pipeline pushes to Kubernetes, which means it needs cluster credentials. This means everyone who can trigger deployments basically has cluster admin. This means when someone fucks up (and they will), they can take down your entire cluster.
Flux flips this security model upside down with GitOps - controllers run inside the cluster and pull changes from Git. No external systems need cluster credentials. When deployments break, they break in a controlled way because Flux runs with minimal RBAC permissions inside the cluster. It's the difference between handing your house keys to every delivery driver versus having them leave packages on your porch.
Version-specific gotcha: Flux v2.3.0 had a reconciliation bug that would hang on large Git repos. If you're still on that version, you'll see controllers just stop syncing after a while. Upgrade to v2.6.4 (latest as of August 2025) - it fixed the memory leaks and added OCI artifact support so you can store manifests in container registries instead of Git (useful for air-gapped environments where Git is a pain).
Recent security wins: Flux completed its second CNCF security audit in 2023 with zero CVEs found. The audit by Trail of Bits validated Flux's architecture as inherently more secure than push-based CI/CD systems. This is why companies like Deutsche Telekom trust it with critical 5G infrastructure.
Flux CD graduated from the CNCF in 2022 and passed comprehensive security audits without any critical vulnerabilities.
How the Controllers Work (And Which Ones Break)
Flux splits into separate controllers - Source, Kustomize, Helm, and Notification. This is great for modularity but a pain in the ass when debugging because you never know which controller is having the bad day.
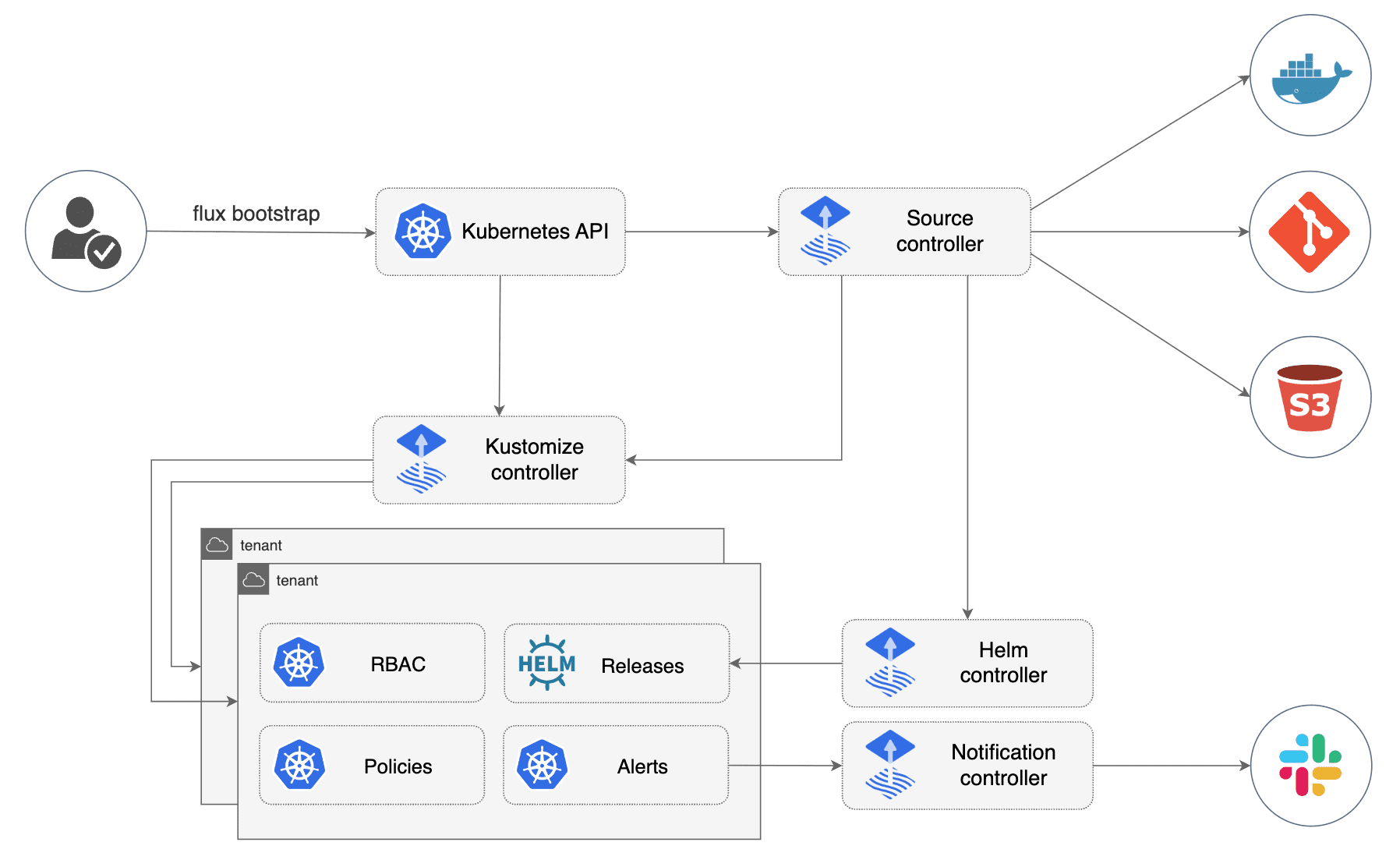
The GitOps Toolkit forms the foundation of Flux's modular architecture, enabling specialized controllers to handle different aspects of continuous delivery.
Source Controller watches Git repos and OCI artifacts. It'll eat your Git API rate limits if you set sync intervals too low. I learned this the hard way when GitHub started rejecting requests after we had 50 repos syncing every 30 seconds.
Kustomize Controller applies your YAML. When it breaks, you get cryptic errors like "failed to apply manifests" with no context. Use kubectl describe kustomization your-app to see what actually went wrong. Pro tip: if you see source not ready, the Source controller is choking on your Git repo.
Helm Controller handles charts. It's better than manually running helm upgrade because it won't leave half-deployed releases when things go sideways. But it will get stuck if you have RBAC issues - the "reconciliation failed" error tells you nothing useful.
Notification Controller sends alerts to Slack/Discord/whatever. It works, but setting up the webhooks is annoying if you're behind corporate firewalls.
Why Flux is More Secure Than ArgoCD
Flux controllers run inside your cluster with minimal RBAC permissions. ArgoCD requires you to give it cluster-admin or create a mess of service accounts. When security audits were done by Trail of Bits in 2023, they found Flux's architecture inherently more secure.
Here's what actually matters for security:
SOPS integration - Flux has built-in SOPS support for encrypting secrets in Git. No more "oops I committed my database password" moments. The controller decrypts secrets at runtime using your KMS keys.
Image verification - You can configure Flux to verify container signatures with Cosign. This catches when someone pushes malicious images to your registry. It's not enabled by default though - you have to configure it.
Multi-tenancy RBAC - Flux can isolate tenants using namespace-scoped permissions. Setting this up is a nightmare the first time, but it works. Each team gets their own GitRepository and Kustomization resources, and they can only mess with their own stuff.
Production reality check: Deutsche Telekom runs 200+ clusters with 10 engineers because Flux doesn't require babysitting. But don't think it's maintenance-free - you'll still need to monitor reconciliation failures and update controllers regularly. Each controller needs about 50MB RAM minimum, more if you're syncing hundreds of manifests.