Packer builds machine images so you don't have to spend your weekends manually configuring servers. Latest version Packer 1.11.0 dropped July 2024, but honestly, the plugin bugs still make you want to throw your keyboard through a window half the time.
If you're tired of deployment surprises and "works on my machine" disasters, Packer might save your sanity. Here's the problem it actually solves.
The "Works On My Machine" Problem
Ever spent 3 hours debugging why your app works perfectly on your MacBook but dies instantly in production? Yeah, that's the "works on my machine" curse. Traditional deployments involve spinning up a fresh server and installing everything from scratch, hoping nothing breaks. Spoiler alert: something always breaks.
Packer solves this by baking everything into the golden image beforehand. Your app, dependencies, configs, security patches - all pre-installed and tested. When you deploy, you're just booting an image that already works.
How Packer Actually Works
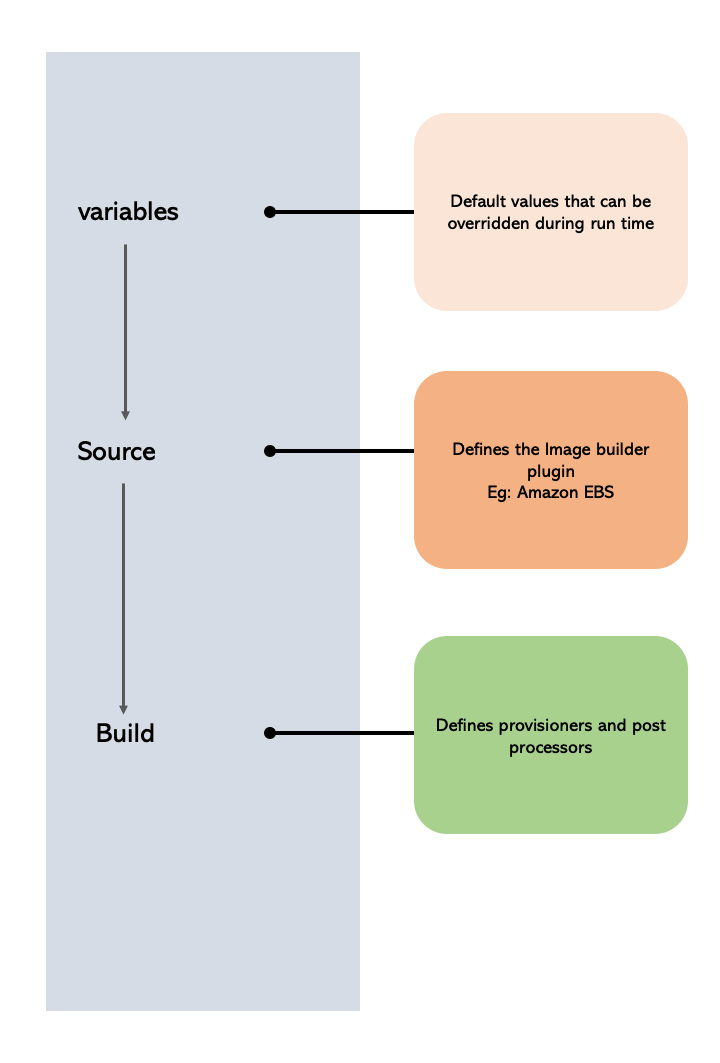
Packer has three parts that actually do stuff:
- Builders: Where to build your images (AWS, Azure, Docker, VMware)
- Provisioners: Scripts that install your app (shell scripts work fine, Ansible if you're feeling fancy, Chef if you hate yourself)
- Post-processors: What happens after - usually uploading to a registry or compressing the result
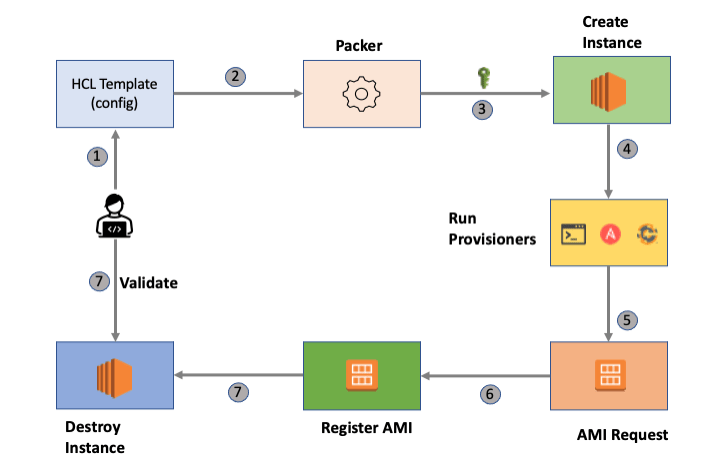
The process looks simple on paper: write a template in HCL2 (HashiCorp's answer to "YAML isn't complicated enough"), run packer build, and sacrifice a goat. Packer spins up a VM, runs your provisioning scripts, shuts it down, and saves the image. Sounds easy until your scripts fail because they expect your laptop's specific PATH or that random symlink you created months ago.
The Good and Bad News
Good news: Packer can build images for multiple platforms simultaneously. I cut our deployment time from 2 hours of manual server setup to 5-minute image boots. Worth the initial pain of getting Packer templates working.
Bad news: Build times vary wildly. Basic Linux AMIs take 5-10 minutes. Windows images with Visual Studio? Plan for 45 minutes and pray nothing times out. Docker builds are fast (2-5 minutes) unless you're installing every npm package known to humanity.
Packer runs on Linux, macOS, and Windows, though Windows support feels like they only tested it once. The binary is tiny (~100MB) but builds will max out your CPU and network like it's 1999.