CodeBuild is AWS's managed build service that runs your CI/CD pipelines without you having to maintain Jenkins servers. Sounds great in theory, but there's a bunch of shit they don't tell you about in the marketing.
The Real Deal on Startup Times
Here's what they don't emphasize in the marketing: every build takes 2-3 minutes just to spin up the environment. Your 30-second unit tests? They now take 3.5 minutes total. This kills fast feedback loops that developers rely on.
The buildspec.yml syntax is pickier than a toddler with vegetables. One wrong indentation and your build fails with a cryptic error message. I've seen teams spend hours debugging YAML syntax when the actual code was fine.
When CodeBuild Actually Makes Sense
Sweet spot: Medium-complexity builds that run 5+ minutes. The startup overhead becomes negligible, and you avoid the Jenkins maintenance headache. Perfect for:
- Docker image builds (these take forever anyway)
- Full test suites that run for 10+ minutes
- Builds that need specific AWS integrations like ECR pushes
Don't use it for: Quick feedback loops (you'll lose your mind), simple static site builds (Netlify deploys in 30 seconds), or anything where you need sub-minute build times.
The Platform Gotchas
Linux environments work well with decent Docker support. Windows builds are basically a joke - half the Windows Docker images fail with cryptic registry errors, and debugging is painful because logs get truncated right where errors happen.
VPC builds need a NAT gateway ($45/month) or VPC endpoints for internet access. Don't forget this or builds fail with timeout errors. Stack Overflow is full of posts about this exact issue - source download timeouts that make no sense until you realize your subnet config is wrong. I learned this during a 2am production deployment when npm install kept timing out after exactly 5 minutes.
Cost Reality Check
Pricing starts at $0.005 per build minute which sounds cheap. But builds can run longer than expected, and the costs add up fast if you're not careful. The 100 free minutes/month disappear quickly with a few failed builds.
Pro tip: Use the general1.small instances for most builds. The larger instances cost 4x more and often aren't necessary unless you're doing heavy compilation.
Integration with AWS Ecosystem
CodeBuild shines when you're already deep in AWS. Native IAM roles, ECR integration, and CodePipeline orchestration work seamlessly.
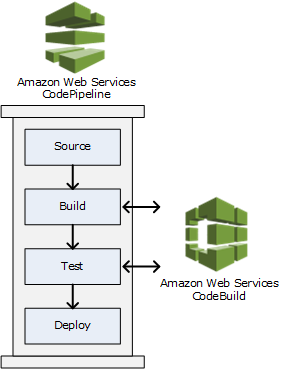
Build logs flow to CloudWatch automatically, which is nice for debugging (when they don't get truncated). Secrets management via AWS Secrets Manager beats dealing with Jenkins credentials.
Bottom line: If you're building AWS-centric applications and don't mind the startup time trade-off, CodeBuild eliminates a lot of infrastructure headaches. Just don't expect fast feedback loops.
For more detailed guidance, check out the AWS CodeBuild best practices guide, common troubleshooting scenarios, and the CodeBuild samples repository for real-world examples.




