GitLab tries to be everything to everyone. Sometimes this works great - you get source control, CI/CD, security scanning, and project management in one place. Sometimes you spend your weekend debugging why the exact same pipeline that worked Friday is failing Monday.
What They Don't Tell You in the Sales Demo
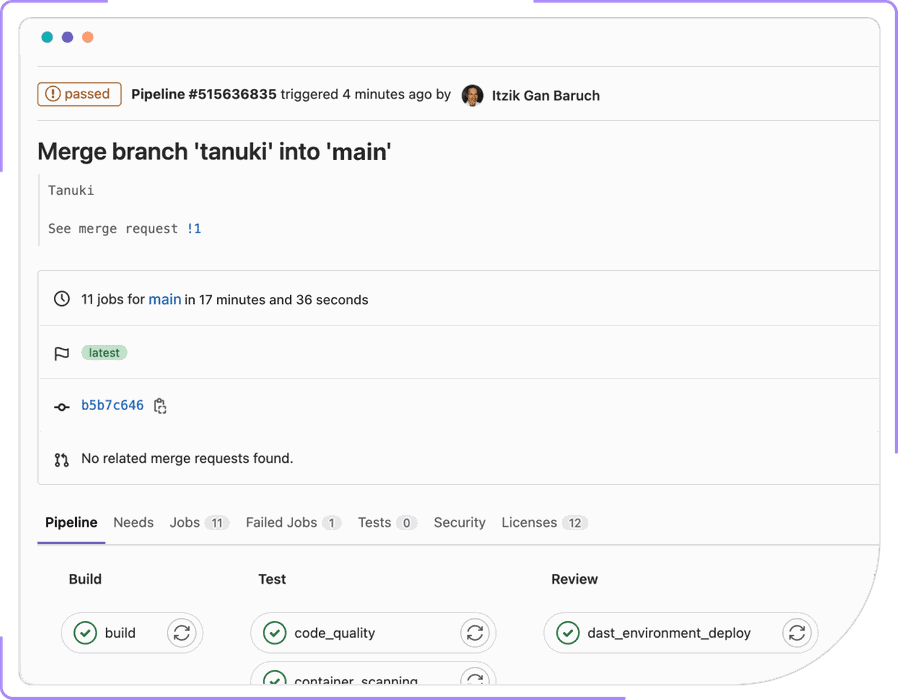
YAML Hell is Real: Your `.gitlab-ci.yml` file will become a 200-line monster that nobody fully understands. Indentation matters. Spaces vs tabs will destroy your soul. And the error messages? "Job failed with exit code 1" tells you exactly nothing.
CI Minutes Burn Fast: Those free 400 minutes? Gone in a week if you're doing Docker builds. Windows builds eat minutes like they're going out of style. macOS builds cost extra and take forever. I learned this the hard way when we added the webpack-bundle-analyzer plugin and suddenly our builds went from 5 minutes to 25 minutes. Took me three hours of debugging to realize it was analyzing every single chunk in parallel, spawning 47 worker processes that each hit GitLab's memory limits.
Shared Runners Are Slow: GitLab's shared runners work, but they're not fast. Your 30-second local build becomes a 5-minute CI build. Want faster builds? Bring your own runners and become a sysadmin.
Things That Will Bite You
- Cache invalidation: GitLab's cache is great until it randomly stops working and you can't figure out why. Cache keys containing forward slashes break silently on Windows runners. Fun fact: this breaks if your branch names have slashes like
feature/user-auth. - Environment variables: Work perfectly in your local Docker container, fail mysteriously in GitLab CI. The
$CI_COMMIT_SHAvariable gets truncated to 8 characters in some contexts but stays full-length in others. - Windows runners: Slower than molasses and eat your CI minutes for breakfast. A 2-minute Linux npm install becomes a 12-minute Windows nightmare because Windows Defender scans every node_modules file.
- Security scanning: Finds 200 vulnerabilities, 180 are false positives you'll spend hours triaging. SAST flags every SQL query as injection risk, even parameterized ones.
- GitLab.com outages: More frequent than you'd expect for a platform charging enterprise prices. Database problems take down the whole platform for hours.
The All-in-One Promise (And Its Problems)
GitLab wants to be your entire DevOps toolchain. They've got source control, CI/CD, security scanning, project management, a container registry, and even monitoring.
This is great when it works. One login, one UI, everything talks to everything else. But when one piece breaks, it can take down your entire workflow. I've seen teams unable to deploy because GitLab's merge request approvals were having a bad day.
Real Talk on GitLab 18.1
GitLab 18.1 dropped in June 2025 with some actually useful stuff:
- Maven virtual registry (beta): Finally, centralized dependency management that doesn't suck. Still beta though, so YMMV.
- Duo Code Review: AI code reviews that are helpful about 60% of the time. Better than nothing.
- Variable precedence controls: Security teams can finally stop developers from overriding critical pipeline settings.
The GitLab Runner 18.1 bug fixes are real and they fixed some annoying edge cases. Still doesn't make Windows runners fast though.
Who Actually Uses This
Over 50% of Fortune 100 companies trust GitLab, including Deutsche Telekom, Goldman Sachs, and Nvidia. These companies have dedicated DevOps teams and enterprise budgets.
For smaller teams, the learning curve is steep. GitHub Actions is simpler if you just need CI/CD. Jenkins gives you more control if you don't mind the plugin hell.
But if you want everything in one place and have the patience for YAML debugging sessions, GitLab can work. Just don't expect it to be painless.