Vault is HashiCorp's secrets management tool that your security team probably forced on you after finding API keys in your Git history for the third time. I've been through this exact scenario - it's designed to solve the problem of "where the fuck do we store all these passwords and tokens?" in a way that makes auditors happy and developers miserable.
The basic idea sounds reasonable: instead of hardcoding database passwords in your YAML files or passing AWS keys around in Slack, you store everything in Vault and applications ask for secrets when they need them. What they don't tell you upfront is that this "simple" concept turns into learning a whole new ecosystem of policies, auth methods, and operational complexity that'll have you debugging authentication failures at 3am.
The Reality of Vault's Architecture

I've deployed Vault's security-first architecture where everything is encrypted at rest, which sounds great until you realize that means when Vault is down, your entire application stack becomes read-only. The "cryptographic barrier" is fancy marketing speak for "if you lose your unseal keys, you're absolutely fucked." I learned this the hard way during a cluster failure.
The architecture has these components: a **Storage Backend** (I usually go with integrated Raft over Consul these days), a Barrier that encrypts everything, **Secrets Engines** that manage different types of secrets, and **Auth Methods** for authentication. Each piece adds complexity, and debugging issues requires understanding all of them. The modular design sounds flexible until you spend weeks figuring out why your Kubernetes auth isn't working with your LDAP integration - trust me, I've been there.
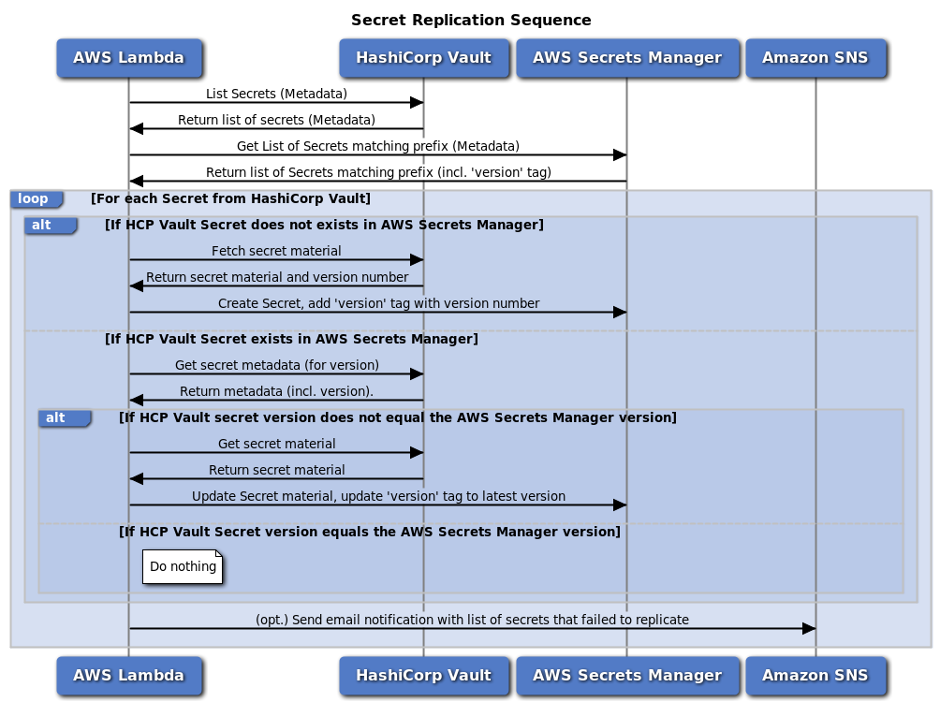
Dynamic Secrets: Great in Theory, Painful in Practice
Dynamic secret generation is Vault's killer feature - instead of static passwords, it creates temporary credentials on-demand. For databases, Vault spins up a user with specific permissions that expires in X hours. This is brilliant for security but a nightmare for debugging.
When your app can't connect to the database at 3am, and the credentials expired 10 minutes ago, and the renewal process failed because of a network hiccup, you'll question every life choice that led you to this moment. I've been there - staring at error logs while production is down and trying to figure out why Vault decided NOW was the time to be picky about token renewals. The automated lifecycle management works great until it doesn't, and troubleshooting dynamic credential failures requires deep knowledge of both Vault and your target system.
The audit trails are comprehensive, but good luck correlating "user vault-db-user-abc123 connected to postgres" with "which microservice was trying to do what" when you're debugging a production incident. I've spent hours cross-referencing Vault logs with application logs trying to piece together what went wrong.
Enterprise Reality Check
Adobe uses Vault at scale, which is great, but Adobe also has a dedicated team of engineers whose full-time job is managing Vault. They initially considered forking it, which should tell you something about the operational complexity.
Most organizations deploy Vault for the big four: database credentials, cloud provider keys, TLS certificates, and general secret storage. The integration story sounds good on paper, but each integration is its own special snowflake with unique failure modes. LDAP auth breaks differently than Kubernetes auth, which breaks differently than AWS IAM auth.
Current Status: As of September 2025, Vault 1.20.1 is current, with the latest release focused on post-quantum cryptography support in the Transit Engine - because preparing for quantum computers cracking your encryption is apparently more urgent than making Vault easier to deploy. HashiCorp maintains active development, mostly adding enterprise features that make the pricing even more painful.