
If you've ever manually created AWS accounts in an enterprise environment, you know the pain: 47 different console screens, endless IAM configuration, networking setup that breaks mysteriously, and 2-3 days of your life you'll never get back. AFT exists to solve this nightmare.
AFT combines AWS Control Tower with Terraform to automate the mind-numbing process of manually setting up AWS accounts. Takes about 20-30 minutes to provision an account versus the 1-2 day nightmare of doing it manually through the console. That's assuming your Control Tower setup isn't fucked and your IAM roles actually work on the first try (they won't).
How AFT Actually Works (When It's Not Broken)
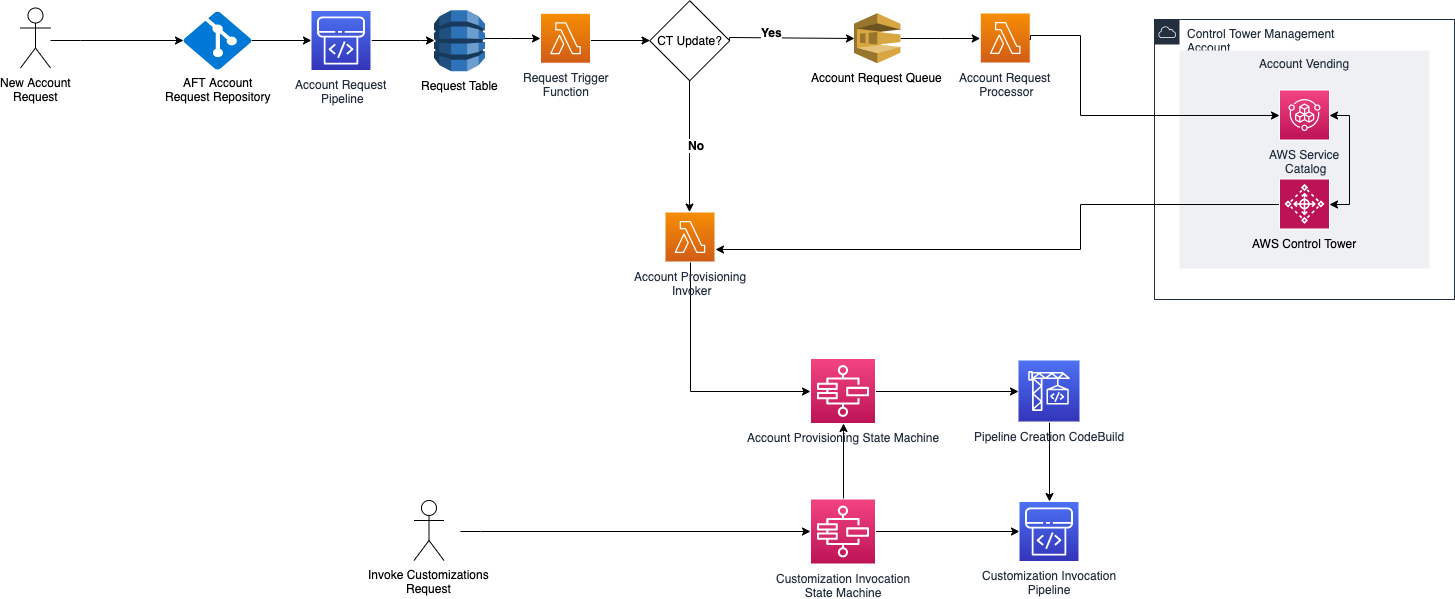
AFT runs in a dedicated management account separate from your Control Tower management account. This is critical because mixing them will cause permissions nightmares that'll make you question your career choices. The separation means you need to manage IAM trust relationships between multiple accounts, which is where 80% of your initial setup pain comes from.
The AFT framework uses CodePipeline, Step Functions, and DynamoDB under the hood. Every account request starts with a Terraform file in Git that triggers the pipeline. When it works, it's beautiful. When it breaks, you'll spend hours digging through CloudFormation stack failures wondering why AWSAFTExecution role can't assume AWSControlTowerExecution role even though the trust policy looks correct.
The AFT architecture follows a strict workflow: account request submission, validation, provisioning, global customizations, and targeted customizations. Each stage has its own failure modes that the troubleshooting guide barely covers.
ITSM Integration - Making ServiceNow Suck Less
Most enterprises want AFT to play nice with their ticketing systems. You can build wrapper APIs around the aft-account-request module to translate ServiceNow requests into Terraform JSON without some poor DevOps engineer copy-pasting ticket details into HCL files at 2am. The AFT account customization examples repo shows how to build these integrations properly.
The AFT Blueprints project has pre-built templates for common setups - networking, DNS, backups, the usual shit. The blueprints are actually pretty decent and will save you from reinventing VPC patterns for the 47th time. The AFT Blueprints documentation explains how to implement these patterns, but don't expect them to work perfectly in your environment without customization. The getting started guide covers the basics, though you'll need to adapt everything for your specific requirements.
Version Control Integration - What Actually Works
AFT works with CodeCommit (boring but reliable), GitHub (everyone uses it), Bitbucket (if you're stuck in Atlassian hell), and GitHub Enterprise through CodeConnections.
CodeCommit integration is rock solid because it's AWS-native. GitHub works great until their webhooks randomly decide to take a vacation - usually shows up as CodePipeline execution failed: Unable to access the repository. Please verify the source location and try again even though the repo is fine and webhook events are being delivered. The webhook troubleshooting guide explains why they fail so often but doesn't mention that GitHub's webhook delivery attempts timeout after 10 seconds, which isn't enough if your AFT pipeline is busy.
Bitbucket... well, it's Bitbucket. Works fine if you're already paying Atlassian's enterprise tax for everything else.
If you're using Terraform Cloud or Enterprise, AFT plays nice with managed state through their APIs. Just be ready to pay HashiCorp's licensing fees, which will make your CFO cry. The Terraform Cloud integration guide covers the technical details.
Customizations That Actually Matter
AFT has two types of customizations: global (applies to every account, can't be bypassed) and account-specific (optional per account). Global customizations are perfect for security policies that developers will try to disable if you let them. Account-specific customizations handle things like prod accounts needing hardened networking while dev accounts just need basic connectivity.
The customizations deploy during account creation, which is nice until one fails and leaves you with a half-configured account that's annoying to fix. The account customization options explain the different types available.
The aft_enable_vpc Parameter - AKA The Money Pit
Setting aft_enable_vpc to true puts AFT resources in a VPC with NAT Gateways, VPC endpoints, and all the expensive networking shit. Costs about $200-300/month for basic setups, but scales fast. For 100+ accounts, you're looking at $1000+/month just for the AFT pipeline infrastructure.
The VPC mode adds security by keeping AFT traffic internal to AWS, but most organizations can live without it initially. NAT Gateway charges alone run $45/month per AZ, plus data processing fees. VPC endpoints for S3, CodeCommit, and other services add another $100-200/month. The math gets ugly fast.
If you're on a budget, set it to false and accept the slightly reduced security posture. Your accountants will thank you when the AWS bill doesn't bankrupt the company. You can always enable VPC mode later when the CFO stops asking why the account creation tool costs more than some developer salaries.






