The Reality: You're Probably Here Because Migration Failed
Look, you're probably stuck with Jenkins because ops built everything around it in 2016 and nobody wants to touch that infrastructure. Meanwhile, security discovered GitHub Actions can do vulnerability scanning without setting up another SonarQube server that crashes every Tuesday.

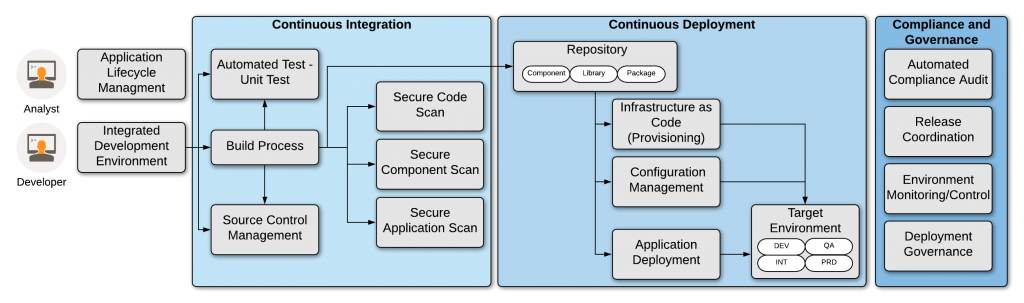
So you end up with this hybrid monster: GitHub Actions does the security theater scanning that makes compliance happy, and Jenkins handles the actual deployment pipeline that somehow still works despite running on Java 8.
The typical pattern is GitHub webhooks trigger Jenkins builds, which then maybe trigger more GitHub Actions, creating a delightful debug nightmare when something breaks at 2 AM. But it works 80% of the time, and that's better than the previous system that worked 60% of the time.
Why This Actually Works (Sometimes)
Security Coverage That Doesn't Suck: GitHub Actions CodeQL runs fast and catches actual vulnerabilities, unlike that abandoned SonarQube instance that flags every eval() as critical. Secret scanning prevents your developers from committing AWS keys to public repos (again). Jenkins handles the heavy lifting with tools like OWASP ZAP, which takes 3 hours to scan a simple React app but finds XSS vulnerabilities your manual testing missed.
Fast Feedback vs. Compliance Bullshit: GitHub Actions gives developers immediate feedback on pull requests before the security team can complain. Jenkins runs the scans that take forever but satisfy audit requirements. Developers get unblocked quickly, security gets their reports, everyone pretends the system works perfectly.
Political Reality: Your ops team has 5 years of Jenkins expertise and Groovy pipelines they barely understand. Security wants modern tooling that actually works. GitHub Actions lets you adopt decent security scanning without starting a infrastructure war or migrating 200 deployment pipelines that sort of work.
Where The Scans Actually Happen
Pull Request Level: GitHub Actions runs CodeQL and Dependabot on every PR because it's free and fast. Dependabot creates approximately 47 dependency update PRs per week that your team ignores until a critical vulnerability forces you to upgrade React from version 16. Secret scanning catches the database passwords your contractors keep committing.
Jenkins Heavy Artillery: Once code gets past PR review, Jenkins unleashes the full security circus. SonarQube runs for 20 minutes analyzing code complexity metrics nobody understands. OWASP ZAP launches a browser, clicks every button, and declares your login form vulnerable to SQL injection (it's not). Trivy scans container images and panics about Alpine Linux CVEs from 2019 that don't actually matter.
Deployment Reality Check: OIDC authentication works great until AWS changes their API again. Artifact signing happens when someone remembers to configure GPG keys. Continuous monitoring means Datadog alerts you 30 seconds after production explodes, which is still faster than your users posting angry tweets.


