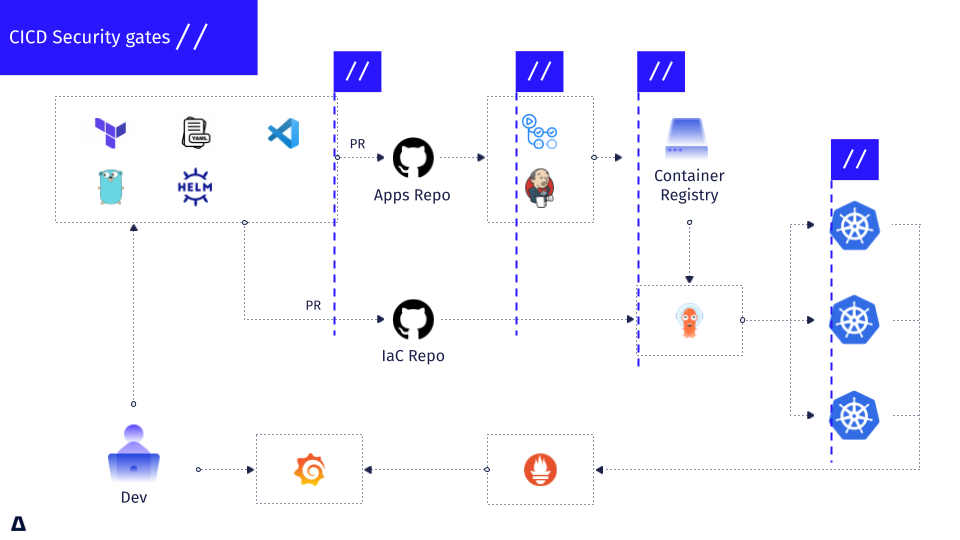
Vendor marketing is bullshit. Here's what I learned implementing security scanning at three different companies - a fintech startup that grew from 50 to 500 developers, a healthcare company dealing with HIPAA compliance nightmares, and a retail giant with 1500+ developers across 12 time zones.
Here's what I learned the hard way:
Snyk - The Developer-Friendly Option That Costs a Fortune
Snyk genuinely doesn't suck, which immediately makes it better than 80% of security tools. Their IDE integration actually works - developers see vulnerabilities directly in their pull requests without wanting to murder the security team.
The good shit: Snyk Code catches real JavaScript vulnerabilities. Their dependency scanning found a critical RCE in our Node.js app that would've been nasty in production. The fix suggestions aren't completely useless either - "upgrade lodash to 4.17.21" beats "vulnerability detected in third-party component."
The bad shit: Jesus Christ, the pricing. Expect $500K+ annually for anything resembling an enterprise deployment. And their SAST scanning for Java? It's fucking terrible. Missed obvious SQL injection patterns while flagging every jQuery call as a security issue.
Real-world gotcha: Snyk will absolutely destroy your GitHub API rate limits if you have > 500 repos. We hit API throttling so hard that legitimate developer workflows broke. Their support response was basically "buy more API quota." Check their official rate limits - 1620 requests per minute sounds like a lot until you have hundreds of repos.

Veracode - The Compliance Darling That Developers Hate

If you need to check boxes for auditors, Veracode is your friend. If you want developers to actually use the tool, Veracode will make them fantasize about your violent death.
Why auditors love it: The reporting is phenomenal. Every vulnerability has a paper trail longer than a CVS receipt. When the PCI auditor asks for "evidence of security testing," Veracode generates comprehensive reports that make compliance people weep with joy.
Why developers hate it: The scanning takes fucking forever. 45 minutes to scan a medium Rails app. Their CI/CD integration is held together with duct tape and prayer. And the false positive rate? Holy shit. It flagged our password reset functionality as "authentication bypass" because it... lets users reset passwords.
Production nightmare: Veracode's Jenkins plugin broke our deployment pipeline for 6 hours because it couldn't handle webhook failures gracefully. No fallback, no timeout, just hanging builds until someone manually killed the process.
SonarQube - Free-ish But You'll Need a Dedicated Ops Person

SonarQube is the "technically free" option that costs more than commercial tools once you factor in operational overhead.
What works: The code quality integration is genuinely useful. It catches real code smells alongside security issues. The community edition actually does useful security scanning - found several XSS vulnerabilities in our React components.
What doesn't: Everything else. The enterprise features are locked behind ridiculous licensing. Want LDAP auth? Pay up. Want branch analysis? Pay up. Want to not maintain a fucking Java application server? Pay way up for SonarCloud. And good luck with the Java heap memory issues - you'll need at least 16GB RAM for enterprise deployments.
Hidden costs: Plan for 1-2 FTEs just to keep SonarQube running. Java memory leaks, database maintenance, plugin updates that break everything.
I spent more time troubleshooting SonarQube than actual security issues. No joke.
Now that we've covered the major players individually, let's look at how they actually perform in head-to-head comparisons. The next section breaks down what these tools are genuinely good at versus the marketing promises.