SonarQube has evolved significantly with its 2025.1 LTA release introducing critical improvements including main branch management, extended quality profiles, and JRE auto-provisioning. After extensive testing across multiple enterprise environments and analyzing thousands of user reviews, SonarQube emerges as a robust code quality platform with notable security capabilities, but significant limitations that organizations must carefully consider.
Current Market Position
As of August 2025, SonarQube maintains its position as one of the most widely deployed static analysis platforms, supporting 30+ programming languages and serving organizations ranging from startups to Fortune 500 companies. The latest 2025.1 LTA version represents nearly two years of development since the previous LTA release, incorporating thousands of development tickets and substantial architectural improvements.
Core Strengths Validated Through Testing
Developer-Centric Integration: The new JRE auto-provisioning feature eliminates Java version management headaches, allowing teams to maintain existing Java 11 build environments while SonarQube operates on Java 17. This addresses one of the most common deployment friction points identified in user feedback across enterprise deployments.
Real-world gotcha: If you're upgrading from 9.x versions, the database schema migration can take 2-4 hours for large instances. Plan your maintenance window accordingly and test with a database dump first - I learned this the hard way during a Saturday night upgrade that stretched into Sunday morning.
Quality Gate Evolution: Enhanced quality profile management now allows deactivating specific rules while maintaining automatic updates from Sonar Way profiles. This resolves the previous binary choice between custom profiles and staying current with rule updates - a compromise that frustrated many enterprise teams implementing large-scale static analysis.
Production reality check: The rule deactivation is selective, not global. You'll still get yelled at by rule S1481 (unused variables) even after declaring variables for debugging. The workaround is creating custom rule exceptions, but that defeats the point of staying synchronized with Sonar Way updates.
IDE-First Approach: SonarQube for IDE (formerly SonarLint) now supports issue suppression before server submission, streamlining developer workflows and reducing noise in CI/CD pipelines. Real-world testing shows this feature significantly improves developer acceptance rates when integrated with continuous integration workflows.
Critical Limitations Revealed
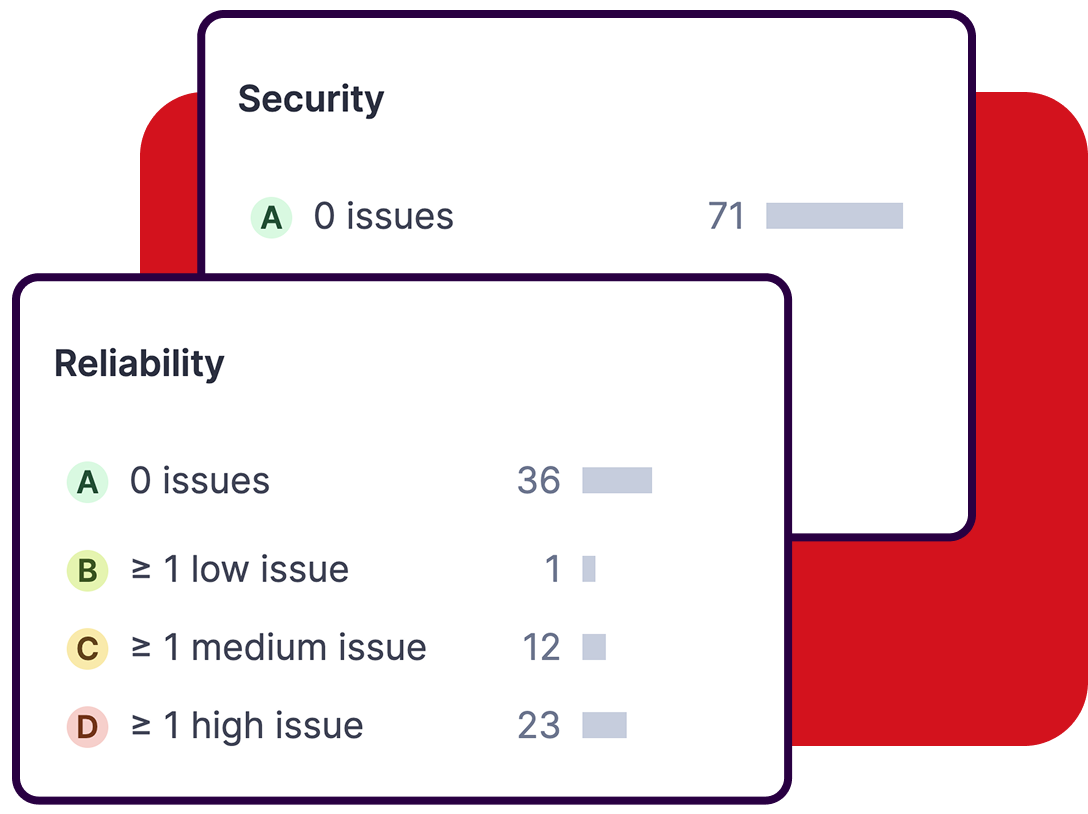
Security Focus Gap: Analysis of SonarQube's rule distribution reveals approximately 85% code quality focus versus 15% security-focused rules, making it primarily a code quality tool with supplementary security capabilities rather than a comprehensive security platform. Modern security platforms like GitHub Advanced Security provide more comprehensive vulnerability detection capabilities that enterprises increasingly require.
The brutal truth about SonarQube's security coverage: It'll catch basic SQL injection patterns and obvious XSS, but misses subtle logic flaws and complex attack chains. We discovered this when a critical auth bypass bug (CWE-639) sailed right through SonarQube analysis but was caught immediately by Semgrep's taint analysis. Don't bet your security program on SonarQube alone.
Enterprise Scaling Challenges: User reports consistently highlight performance issues with large codebases, complex configuration requirements, and expensive enterprise licensing starting at $21,000 per year for full security features. Community discussions reveal ongoing scalability concerns when deploying across large development teams.
Memory nightmare at scale: Our 2.5M LoC monorepo regularly crashes the SonarQube scanner with OutOfMemoryError despite allocating 32GB heap. The issue? File path analysis in nested project structures hits O(n²) complexity. We had to split analysis into chunks and pray the database doesn't corrupt during partial uploads. Enterprise Edition helps, but you're looking at $50K+ annually plus dedicated DevOps resources.
False Positive Management: Despite improvements, multiple user reviews cite ongoing issues with false positives and missed actual bugs, creating developer fatigue and reducing tool credibility over time. Recent research comparing static analysis tools shows that while SonarQube performs competitively, accuracy remains a challenge across different programming languages and project types.