SentinelOne Singularity wants to be your only security tool. Most companies juggle 5-10 different security products that don't talk to each other - endpoint protection here, cloud monitoring there, identity watching over there. You spend half your time just figuring out which tool is alerting about what. SentinelOne says "fuck that complexity" and puts everything in one dashboard.
I learned this the hard way when our old setup had CrowdStrike for endpoints, Trend Micro for servers, and some janky third-party tool for cloud monitoring that crashed every Tuesday. Took us 3 hours to trace a single incident across all three platforms.
Core Platform Architecture
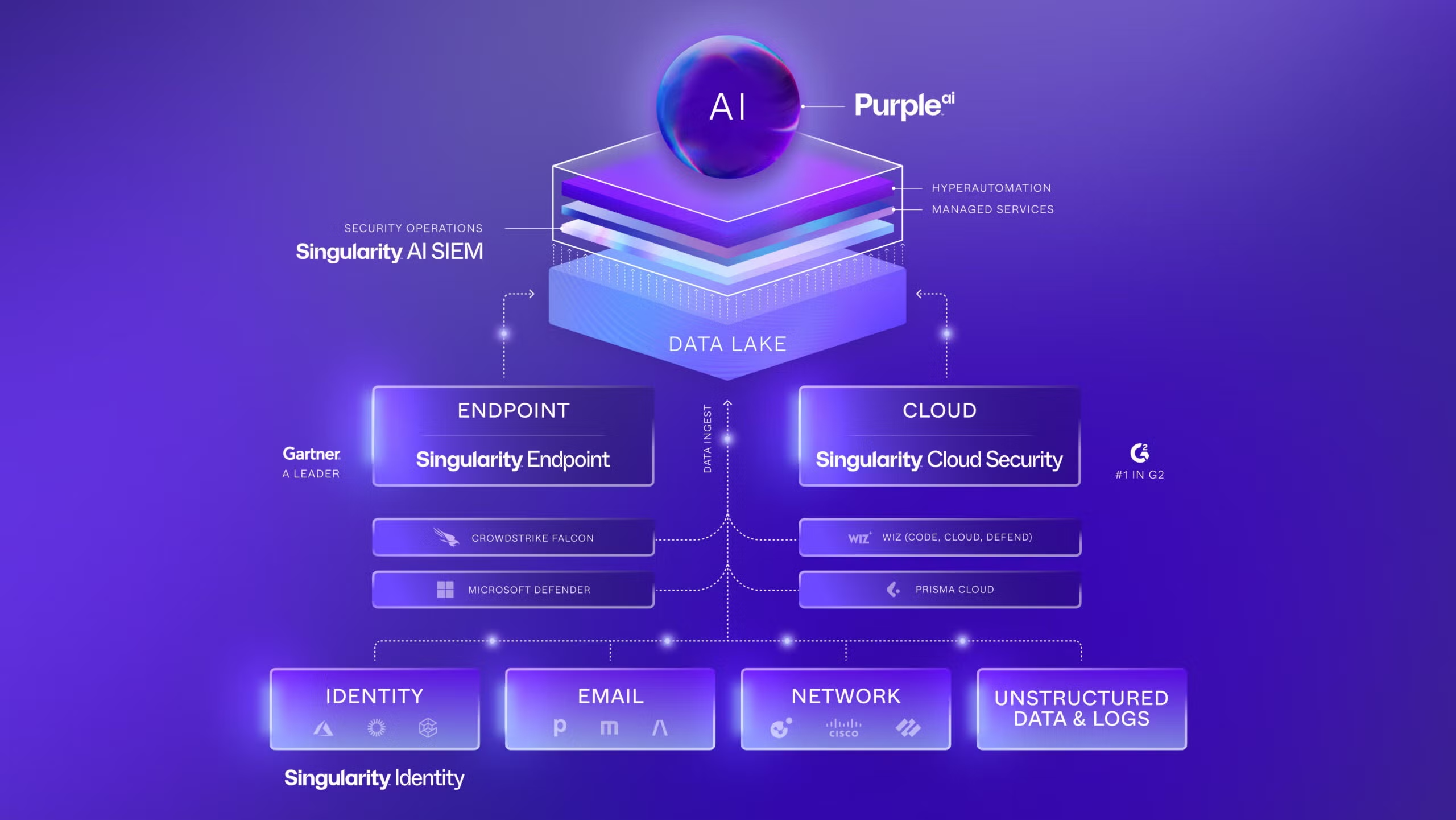
The Singularity platform can handle up to 500,000 endpoints per cluster without shitting the bed. That's massive - most companies never hit those numbers, but if you're a Fortune 500 with offices everywhere, it'll scale. You can run it in SentinelOne's cloud (they have servers in North America, Europe, and Asia) or on your own hardware if compliance requires it.
Pro tip: If your compliance team insists on on-premises, budget an extra month for hardware ordering and setup. Cloud deployment took us 2 hours; on-prem took 3 weeks because the vendor shipped the wrong server specs twice.
Here's the key difference: traditional antivirus looks for known bad stuff using signatures. It's basically playing whack-a-mole with malware samples. SentinelOne watches behavioral patterns instead. When a process starts doing sketchy shit - like trying to encrypt every file on the system - it gets killed immediately, even if it's never been seen before. Works against zero-day exploits and nation-state actors who bring custom tools.
Unified Security Capabilities
Endpoint Protection and Response
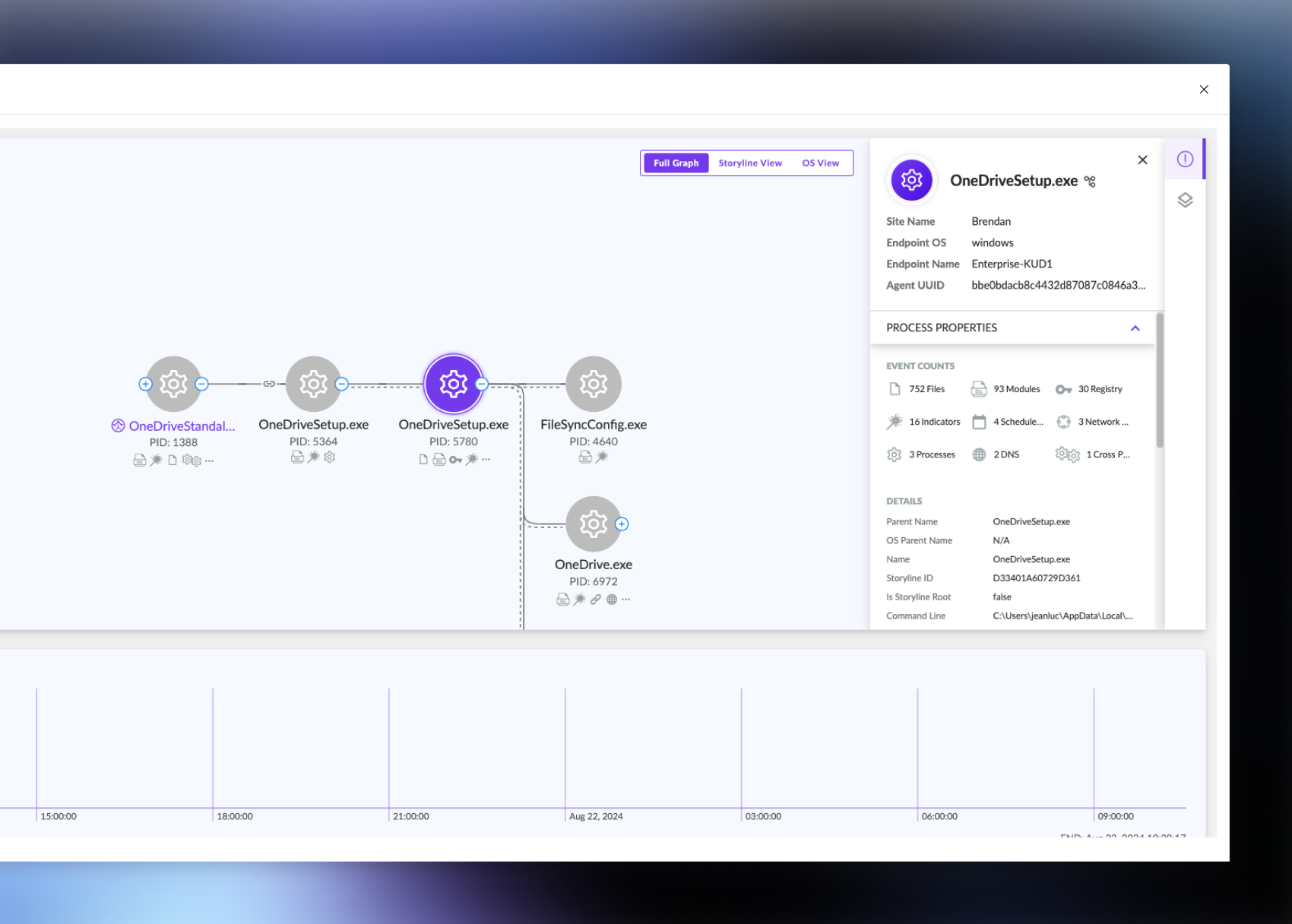
Singularity Endpoint actually works on ancient Windows boxes that you're too scared to update. I'm talking Windows Server 2008 R2 that's been running your ERP system for 15 years and nobody knows the admin password. It supports Windows (XP through 11), macOS (10.12+), and Linux without needing different agents. Just watch out for CentOS 6 - the kernel module occasionally panics on 2.6.32 kernels. The magic happens automatically - when malware hits, it gets quarantined and the system gets rolled back to the exact state before the attack started.
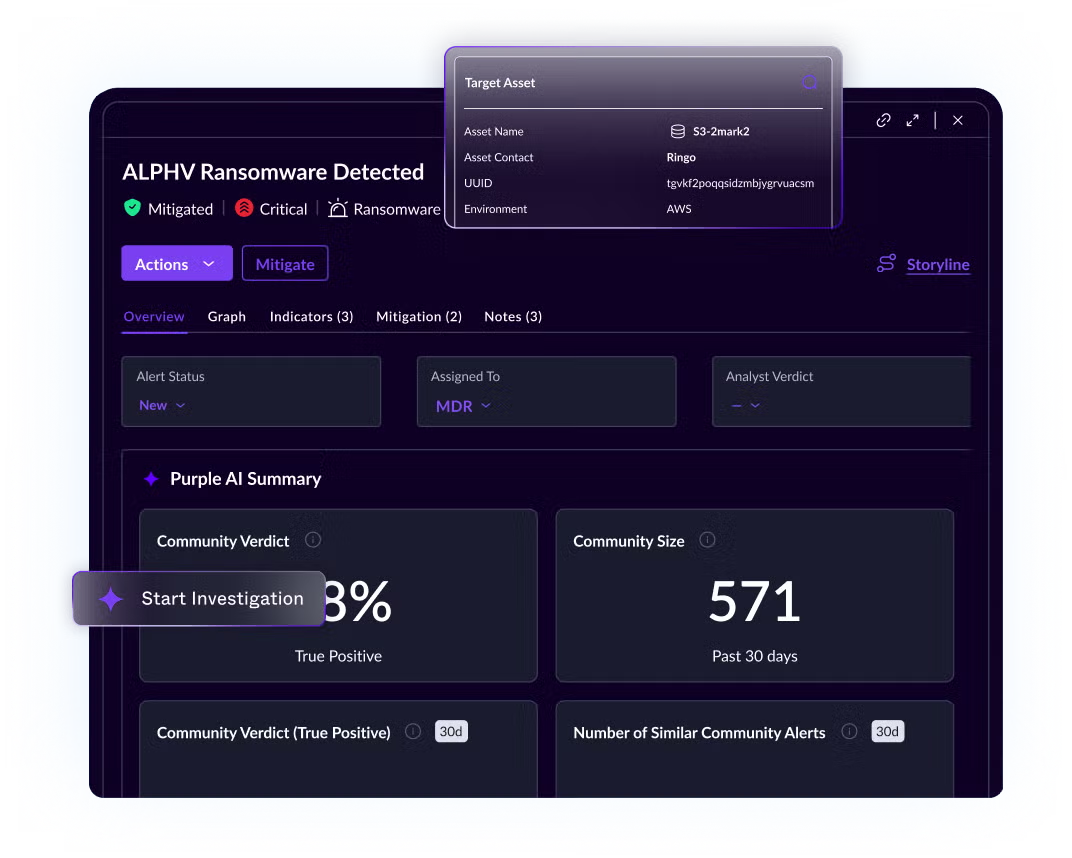
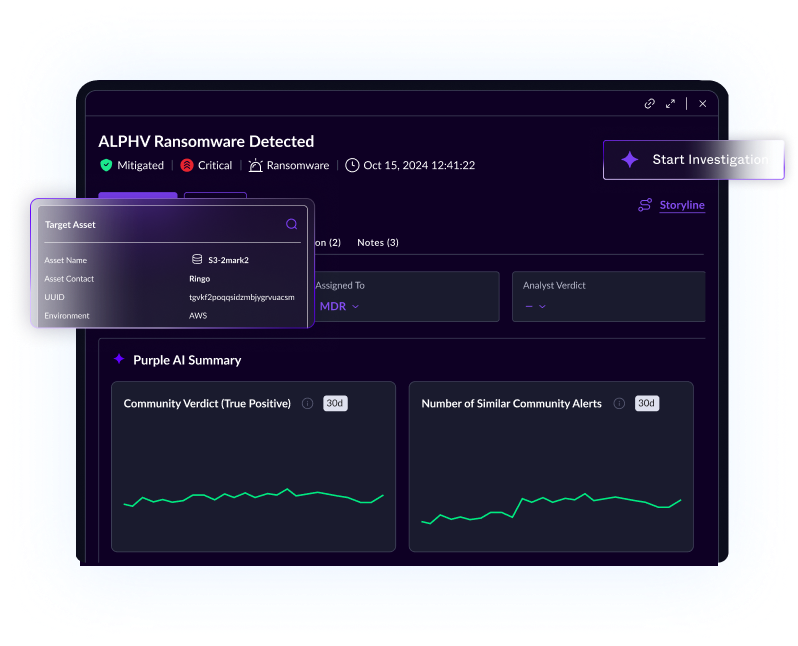
I watched it save our ass during a WannaCry variant attack in 2023. The thing started encrypting files on a file server, SentinelOne killed it and rolled everything back in under 30 seconds. Users didn't even know anything happened.
You can also remote into machines directly from the console - no more "please reboot and call me back" tickets. Device control lets you block USB drives, which actually stops the classic "oops I plugged in a random USB drive from the parking lot" attack. All from one interface instead of juggling separate tools for each function.
Cloud Workload Security
![]()
Singularity Cloud monitors your AWS, Azure, and GCP workloads without slowing them down. It doesn't require you to rebuild your Docker containers or reconfigure your Kubernetes clusters. Fair warning: Docker Desktop on Windows randomly stops working after agent installation - Microsoft Defender and SentinelOne sometimes fight over container monitoring. The agent just watches for malicious behavior and stops it - whether that's cryptominers hiding in containers or someone trying to escalate privileges in production.
It scans your container images for vulnerabilities before deployment and watches for runtime attacks after deployment. Hooks into your CI/CD pipeline so you catch problems early instead of finding them in prod at 2am. Works across all major clouds with the same policies - no more "it works in AWS but breaks in Azure" headaches.
Identity Threat Detection
Singularity Identity watches your Active Directory and Azure AD for sketchy login patterns. You know that thing where attackers steal credentials and then hop between servers using legitimate tools? This catches that. Spots credential stuffing attacks, privilege escalation attempts, and when someone's moving through your network in ways that don't make sense for their job role.
When it detects compromise, it can automatically disable accounts before the attacker does real damage. Critical because 80% of breaches involve stolen credentials - malware is flashy, but most attackers just steal passwords and walk in the front door.
Purple AI Integration
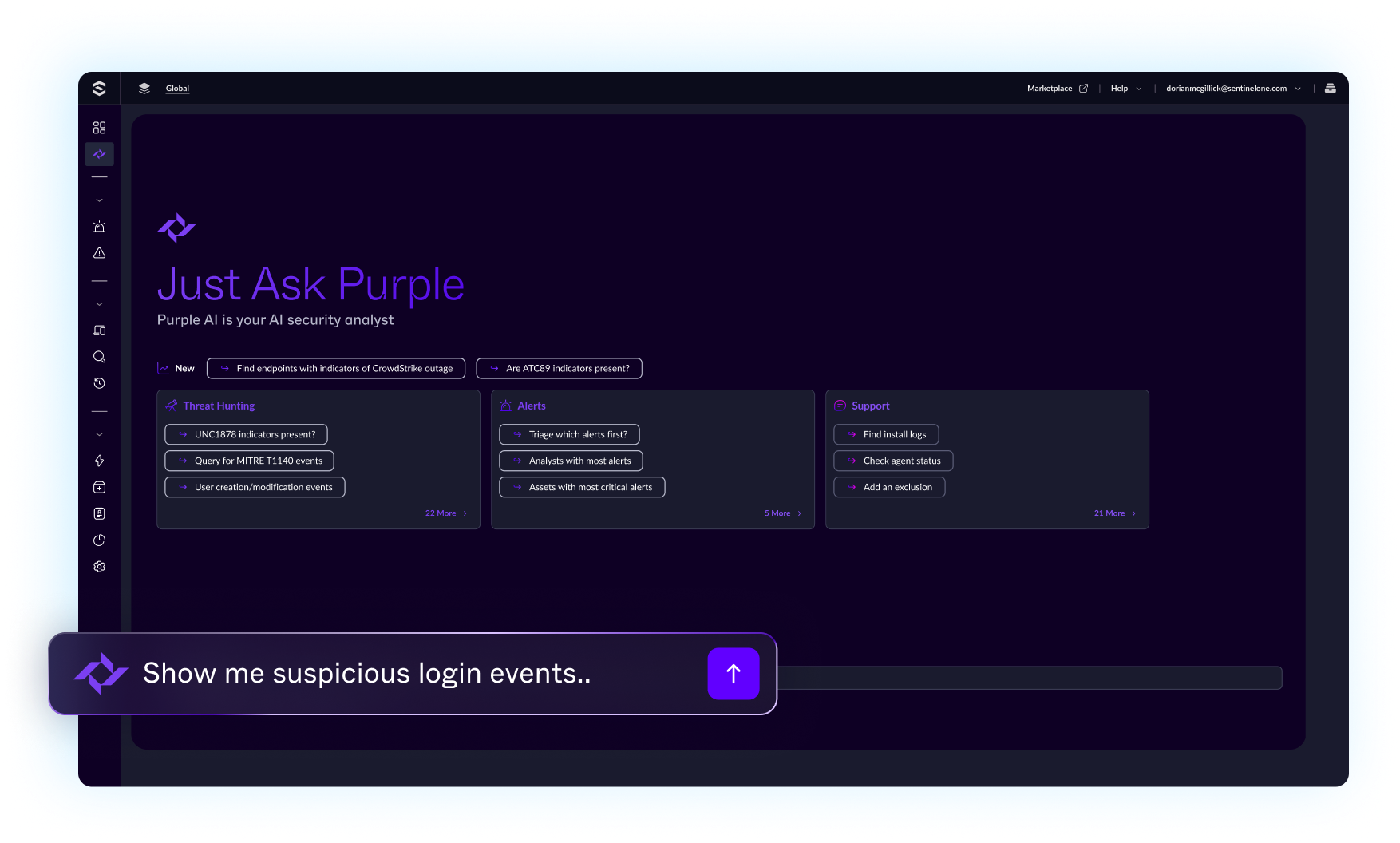
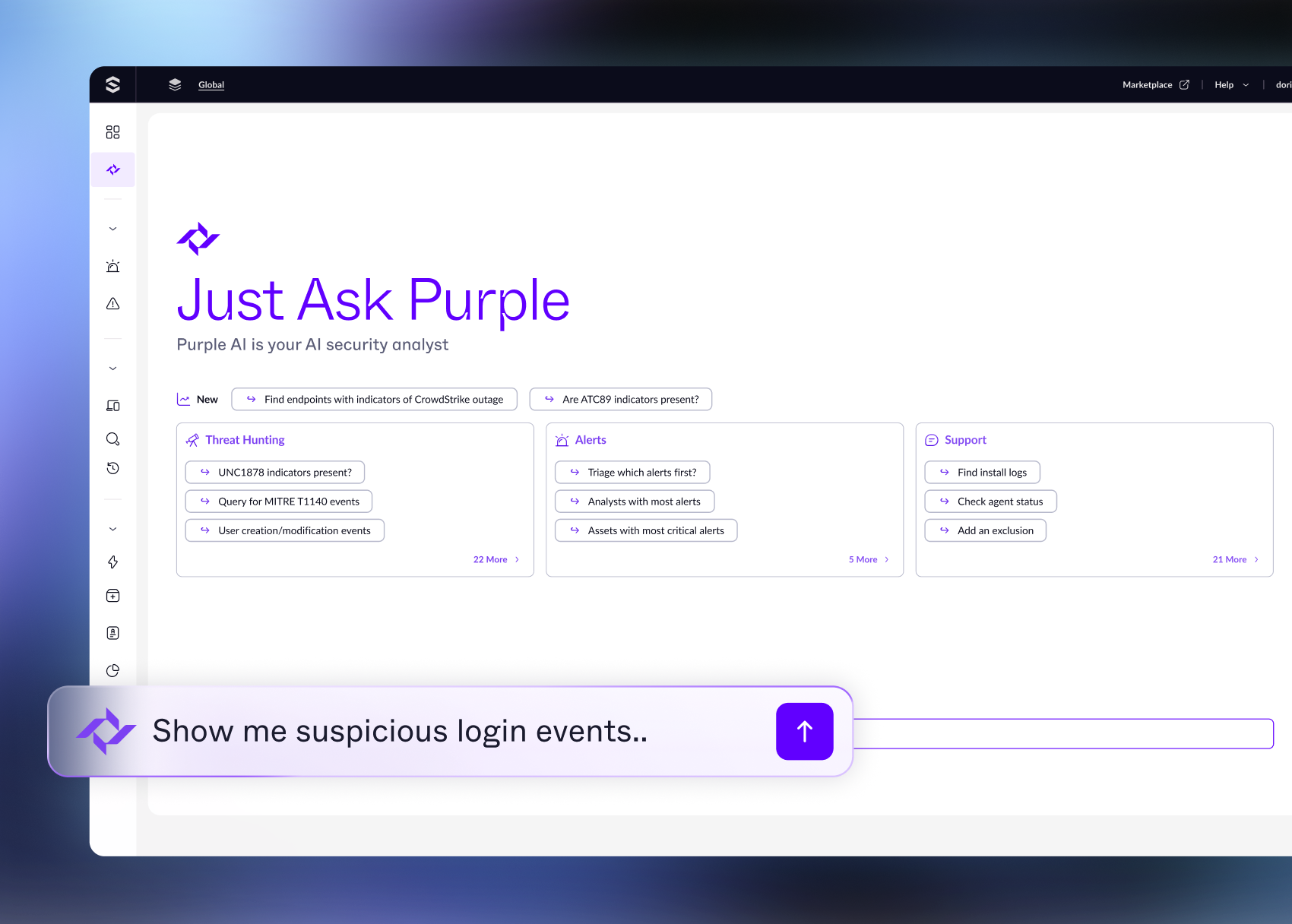
Purple AI is actually useful, unlike most "AI" marketing bullshit. You can ask it questions in plain English like "show me suspicious PowerShell execution from the last week" and it translates that into proper hunt queries. No more trying to remember the exact syntax for complex searches.
It's particularly helpful when you have junior analysts who know what to look for but don't know how to write the queries yet. Purple AI can guide them through investigations and suggest follow-up questions. Actually saves time instead of just creating more work like most AI tools.