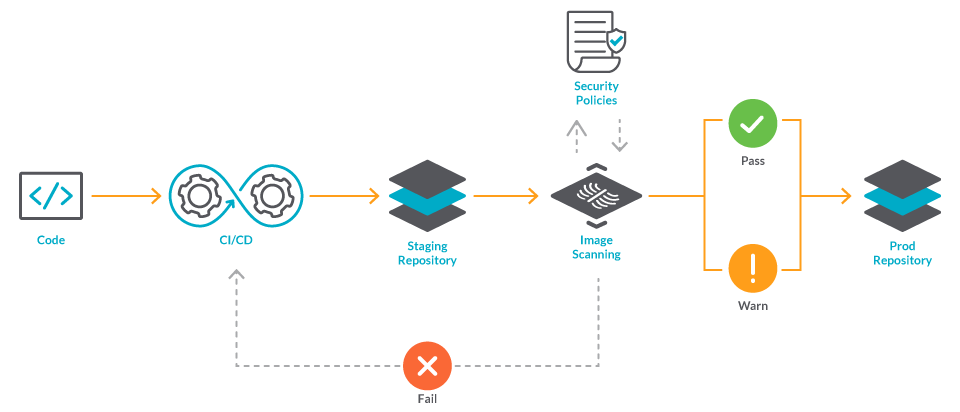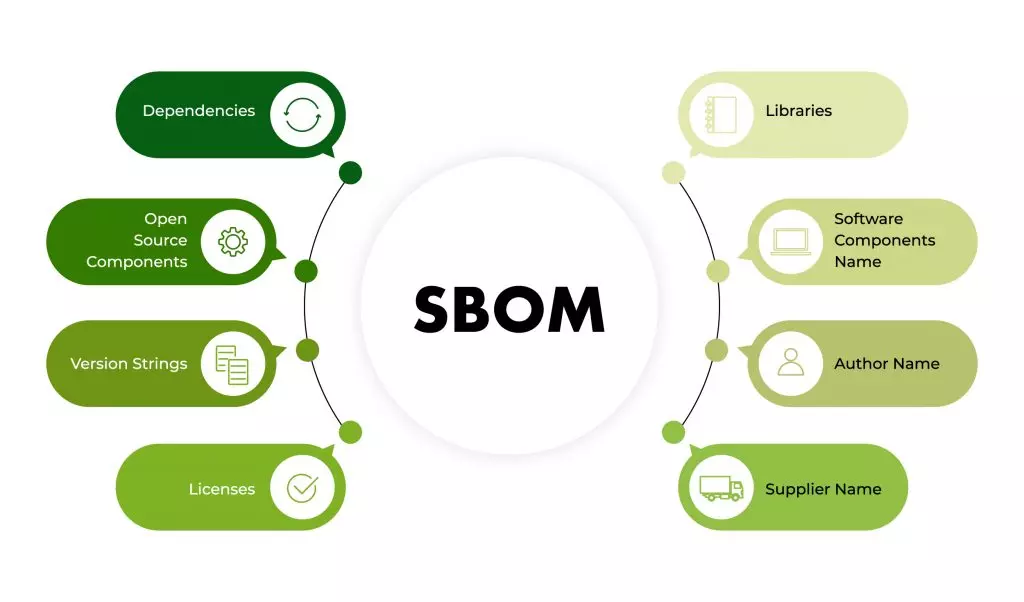
Anchore scans container images and tells you what's inside them. Unlike most security tools that just scan for vulnerabilities, Anchore starts by generating a Software Bill of Materials (SBOM) that lists every package, library, and dependency in your containers. Then it scans those components for known security issues.
The main value? You finally know what's actually running in production. Had a Log4j incident? Anchore can tell you which containers are affected in minutes instead of days. Though honestly, if you haven't been tracking your dependencies already, that's on you.
The Three Parts That Actually Matter
Anchore Secure finds vulnerabilities and other nasty stuff. It scans for known CVEs, malware, and leaked secrets. The scanning is fast - takes about 30 seconds for a typical Node.js container. But you'll spend way more time dealing with the false positives it throws at you. And trust me, there will be a lot of them.
Anchore Enforce blocks deployments that fail your security policies. This is where things get interesting (and frustrating). You write JSON policies that define what's allowed. First time you enable this, it'll break half your deployments because of some random OpenSSL vulnerability from 2019 that doesn't actually affect your app. I learned this the hard way during a Friday afternoon deployment.
Anchore SBOM manages all your software bills of materials. Supports SPDX, CycloneDX, and Anchore's own format. The SBOM management is actually pretty solid - you can import external SBOMs, track license compliance, and generate reports that make auditors happy.
Why It Exists: The Open Source Tools

The whole platform is built on two open source tools that you can use for free:
Syft generates SBOMs from container images. Works on filesystems and source code too. Has 7.6k GitHub stars and actually works reliably. The SBOM generation is surprisingly good - catches most dependencies, though it sometimes misses weird package managers. I've had it choke on some custom Maven setups, but that's probably Maven's fault anyway.
Grype scans for vulnerabilities using the SBOMs from Syft. 10.6k GitHub stars and updates its vulnerability database multiple times per day. Works well, but like all vulnerability scanners, you'll get false positives. Lots of them.
Honestly, most teams can get by with just these free tools. The Enterprise platform adds policy management, a web UI, and compliance reports - nice to have, but not essential unless you're dealing with government contracts or have compliance people breathing down your neck.
How the Damn Thing Works
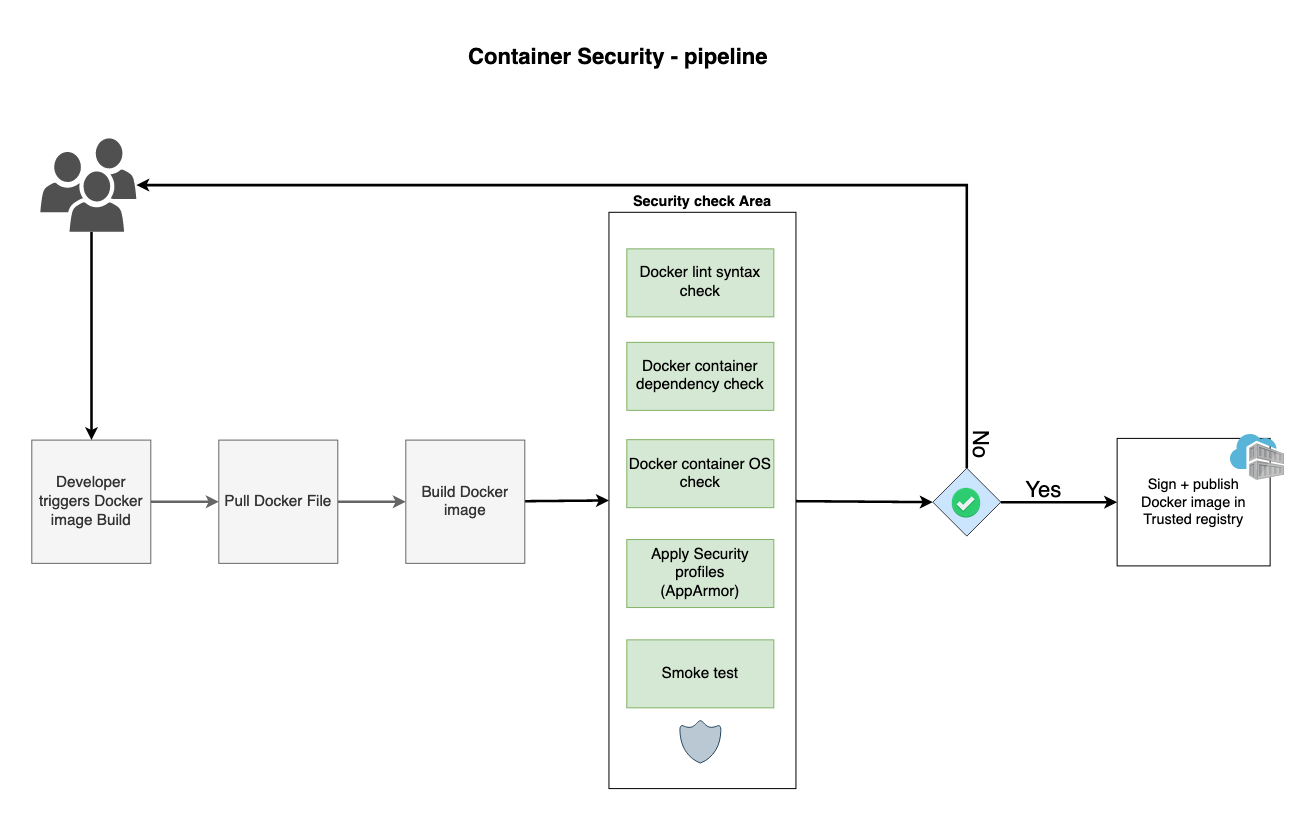
Anchore Enterprise (current version 5.19 as of August 2025) runs as a bunch of containers that talk to each other. Uses PostgreSQL for storage and has these main services:
- Data Syncer: Downloads vulnerability feeds from NVD, Red Hat, and others. Takes forever on first boot - about 45 minutes to sync everything. Sometimes longer if their feeds are having a bad day.
- Policy Engine: Runs your policy rules against scan results. This is where you'll spend most of your tuning time trying to make the damn thing stop flagging every OpenSSL version ever released.
- Analyzers: Actually scan the images and generate SBOMs. Can be CPU-intensive if you're scanning large images. I once watched it chew through 8 cores scanning a bloated Python image.
- API Server: REST API for everything. Well-documented and actually works, which is refreshing.
You can run it on Kubernetes (they provide Helm charts), Docker Compose, or use their pre-built AWS AMIs. The Kubernetes deployment is the most battle-tested option, though the resource requirements are higher than what they tell you in the docs.
For air-gapped environments, you can run it offline, but you'll need to manually download and import vulnerability database updates. Pain in the ass, but it works. Just budget extra time for explaining to security teams why the vulnerability data is a week old.