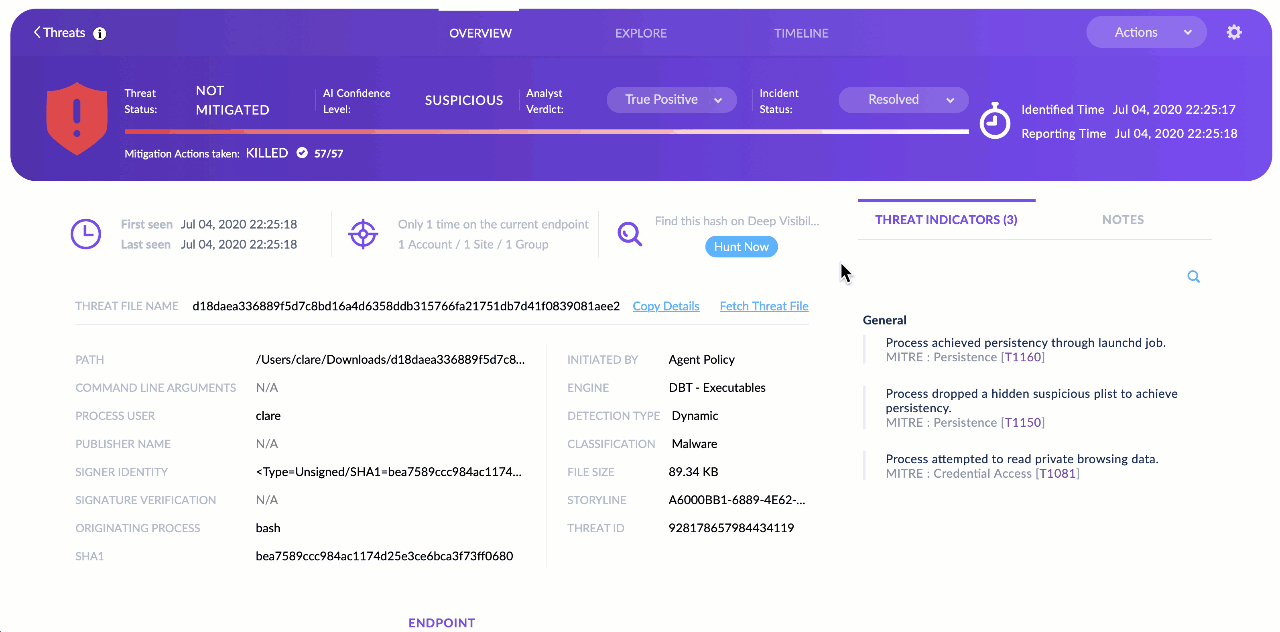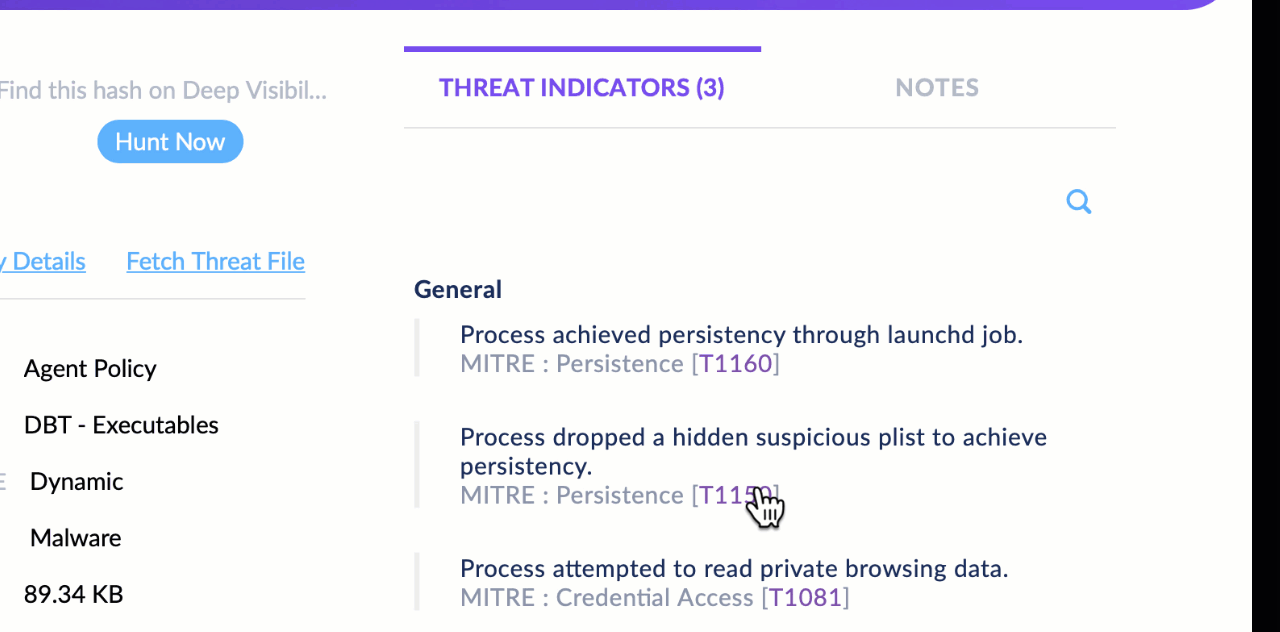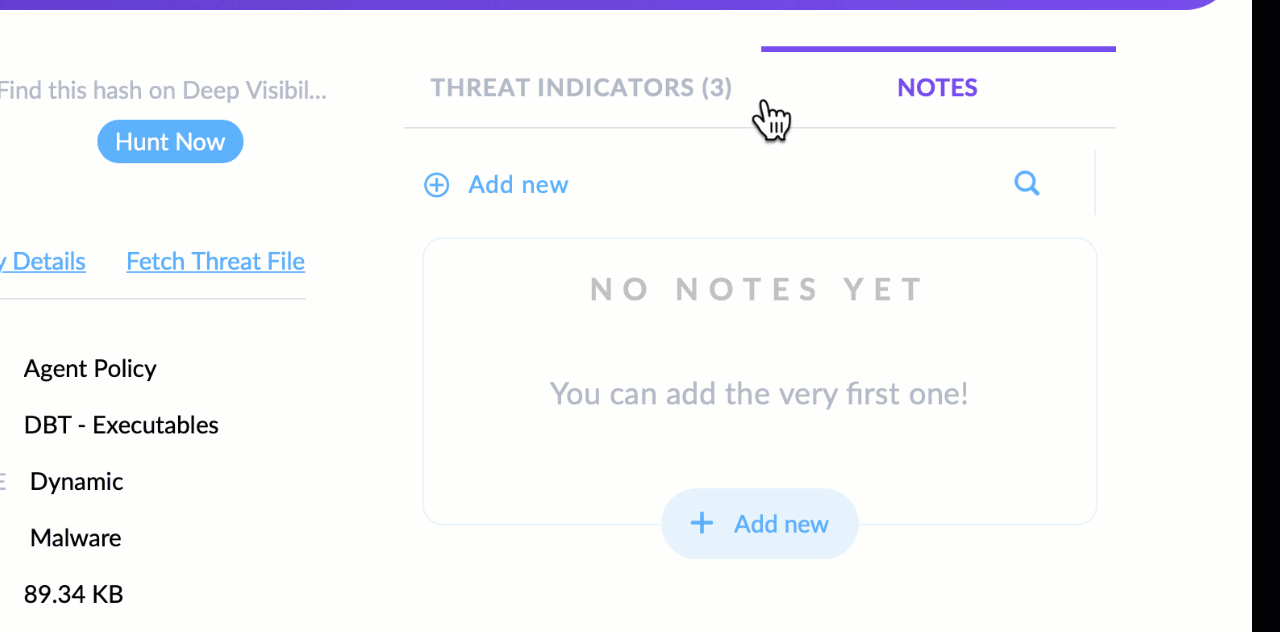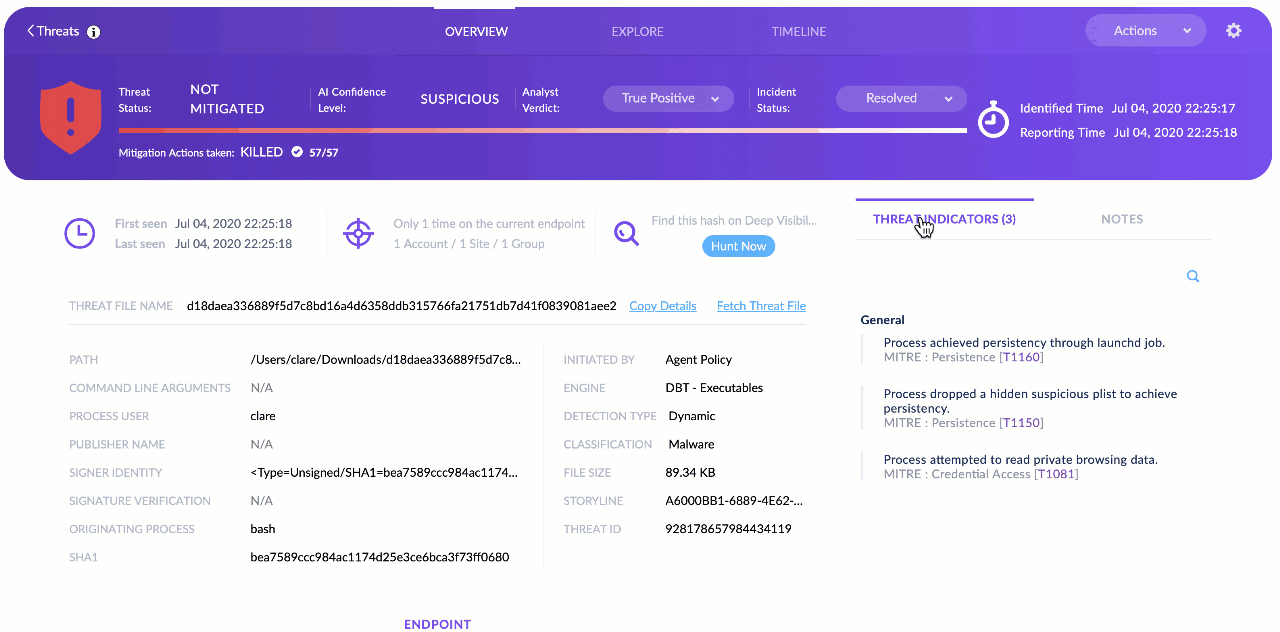
When Enterprise-Scale Hits Reality
SentinelOne's sales pitch makes deployment look like pushing a button. Install agent, apply policy, threats get blocked automatically. After deploying to thousands of endpoints across multiple continents, here's what actually happens when you scale this shit up.
Before you start this deployment clusterfuck, know that your network is about to become a very expensive science experiment.
The Bandwidth Reality Nobody Talks About
Your Network Will Cry
Agents upload a few MB daily normally. Sounds manageable until you multiply by 10,000 endpoints and your bandwidth gets destroyed. During incidents? Forget about it - agents go crazy uploading behavioral data and your network gets hammered.
Remote offices with shitty bandwidth will literally grind to a halt. Had this nightmare at our Mexico plant where 180 agents all started uploading behavioral data at once after a false positive triggered mass file scanning. Killed the entire office connection for 4 hours until we could throttle the agents. QoS policies become mandatory, not optional.
When SentinelOne's cloud services take a shit (and they will), your agents keep basic protection but lose everything that makes the platform worth paying for. No management console, no Purple AI, no automated response - you're flying blind until they fix their infrastructure.
Application Compatibility Hell
Legacy Apps Will Fight Back
Your 15-year-old manufacturing SCADA system that controls million-dollar equipment? SentinelOne thinks it's malware. The process injection techniques that legacy database apps use for legitimate operations trigger behavioral detection alerts constantly.
Custom .NET applications built before modern security practices look exactly like attack tools to machine learning algorithms. You'll spend weeks creating exclusions for legitimate business software while explaining to executives why the new security tool is blocking critical operations.
You'll spend the first 3-6 months babysitting false positives and tweaking policies because machine learning apparently can't tell the difference between legitimate business software and malware.
Had one deployment at a trading firm where their HFT system got blocked during market open because the memory injection patterns looked like exploitation. Cost them $300K in missed trades before we could emergency-exclude the trading software. Now I always test financial platforms first.
Certificate Management Becomes Your Full-Time Job
PKI Infrastructure Will Make You Miserable
SentinelOne agents require valid certificates for cloud communication. Sounds simple until you discover your enterprise PKI infrastructure has six different certificate authorities, three generations of intermediate certificates, and legacy systems that don't support modern cipher suites.
PKI is already a nightmare in enterprise environments, and SentinelOne makes it worse by requiring everything to be perfect all the time.
Certificate renewal at scale becomes an operational nightmare. When a bunch of agents can't validate certificates simultaneously, they all fail to check in. You end up with zero visibility into endpoint protection when you need most.
Multi-domain AD environments are a nightmare - trust relationships break in ways that make no sense. Certificate trust configuration becomes this obscure art that isn't documented anywhere useful.
The Performance Impact They Don't Mention
Resource Consumption Gets Real
SentinelOne markets itself as "lightweight" but behavioral analysis consumes significant CPU cycles. On older hardware or resource-constrained systems, users notice the difference. CAD workstations, video editing systems, and development environments with intensive compilation processes experience noticeable slowdowns.
The "lightweight" marketing claim is complete bullshit once you deploy at scale.
Memory usage? Anywhere from a few hundred MB to way more on busy servers. Database servers and virtualization hosts get hit hard. That "minimal system impact" marketing bullshit falls apart fast when you're already running tight on resources.
Real-time file scanning creates disk I/O bottlenecks on systems with traditional spinning drives. Network file shares experience performance degradation when multiple endpoints scan the same files simultaneously.
Professional Services: The Mandatory Tax
You Can't Do This Alone
SentinelOne documentation assumes perfect environments that don't exist. Complex enterprise deployments require professional services engagement that costs serious money beyond licensing fees - think hundreds of thousands. This isn't optional consulting - it's mandatory to avoid months of painful troubleshooting.
Their documentation assumes you have perfect lab conditions that don't exist in real environments.
Professional services teams know which undocumented configuration settings prevent agent installation failures. They understand policy hierarchy interactions that cause unexpected behavior. Most importantly, they've seen every possible way deployments can fail spectacularly.
The alternative is discovering these limitations through painful trial and error while your security team becomes increasingly frustrated with the platform and executives question the vendor choice.
Change Management at Enterprise Scale
Politics Matter More Than Technology
Business units will resist security measures that impact productivity. Sales teams won't tolerate CRM integration issues. Engineering teams will create workarounds if build processes trigger false alarms. Executive assistants will demand immediate resolution when document workflows get blocked.
User training becomes critical because SentinelOne behaves differently than traditional antivirus. Behavioral detection blocks legitimate activities while learning normal patterns. Without clear escalation procedures and realistic resolution timelines, help desk tickets explode and user confidence erodes.
Communication strategy matters more than technical implementation. Proactive updates on deployment progress, issue resolution status, and performance impact maintain business unit cooperation. Silent deployments that surprise users with blocked activities create lasting resistance to security initiatives.