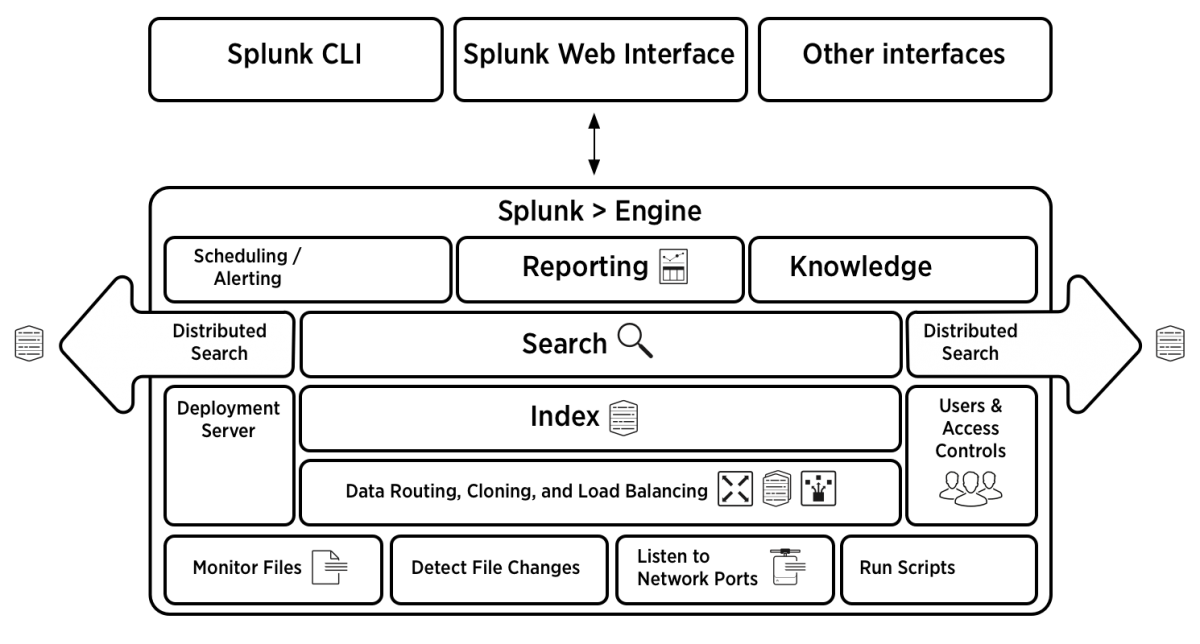
The core Splunk architecture involves three main components: forwarders that collect data, indexers that store and process it, and search heads that provide the interface for querying.
Splunk eats log files and makes them searchable. They've been doing this since 2003, which in tech years means they're ancient but stable. Cisco bought them for $28 billion in 2024, which should tell you something about how much money flows through this ecosystem.
The core architecture includes Universal Forwarders that collect data, indexers that store and process it, and search heads that let you query everything.
What It's Actually Good For
- Log Search: The core functionality that still works great - SPL syntax is weird but powerful
- Security Monitoring: If you need SIEM and have the budget - Splunk Enterprise Security is industry standard
- Compliance Reporting: Generates pretty charts for auditors - SOX, HIPAA, PCI DSS coverage built-in
- Custom Dashboards: If you like clicking things instead of writing SQL - Dashboard Studio is actually decent
- Machine Learning: MLTK and Splunk AI for anomaly detection
The Reality Check
Big companies use Splunk because it works and they can afford it. Small companies use it until they see the bill. The learning curve is steep, the pricing is brutal, and you'll spend months getting it configured properly. But once it's working, it does what it says on the tin.
Recent Gartner reports still rank Splunk as a leader in SIEM, despite the acquisition uncertainty. The community support is still strong, though Stack Overflow threads show the usual complaints about complexity.
What They Don't Tell You
SPL is weird as hell. If you're coming from SQL, prepare to hate everything for the first 6 months. Error messages are useless and the documentation assumes you already know Splunk. Even the training courses cost $3k+ and don't teach you the gotchas you'll hit in production.
Universal Forwarders break randomly. That lightweight agent they talk about? Works great until you have to deploy it on 500 servers with different OS versions, security policies, and network configs. Then you'll hate your life. Windows Server 2019 breaks if you have certain security policies enabled - learned that one the hard way.
The pricing will shock you. Calculate your costs wrong and you'll get a surprise $50k bill. License violations happen constantly and the penalties are brutal. Splunk's pricing page won't tell you the real numbers - you'll need to call them. The pricing secrecy is intentional - they want to extract maximum value based on your specific situation.
Who Actually Uses This Shit
FINRA uses it because they're regulated to death and need bulletproof audit trails. Financial companies love it because compliance officers understand paying millions for log search better than explaining why they went with "the free option." Major banks process billions of transactions through Splunk daily.
Healthcare companies like Regeneron use it because HIPAA compliance is easier when you can search everything. Health IT companies built their entire monitoring infrastructure on Splunk. Manufacturing companies use it to monitor industrial systems because when a $10 million machine breaks, you don't fuck around with open source solutions.
Government agencies love it too - NASA uses it for mission-critical monitoring, and the Department of Veterans Affairs processes millions of medical records through Splunk. The federal marketplace shows dozens of Splunk deployments.