Look, if you're reading this, you probably got stuck evaluating EDR solutions because someone got spooked by a phishing email that made it through your mail filter. Again.
Defender for Endpoint is Microsoft's version of "we can do security too" and surprisingly, they didn't completely fuck it up. It's endpoint detection and response that actually works, though it comes with the usual Microsoft quirks that'll make you question your life choices.
The Reality of Deployment

Plan for 3-6 months of your life to disappear. Anyone telling you this is a "simple deployment" has never tried to push agents to 10,000+ endpoints while dealing with legacy systems compatibility that should have been retired when Obama was in office.
The Windows integration is solid because, well, Microsoft owns Windows. macOS support exists but feels like an afterthought - expect some features to be "coming soon" for the next two years. Linux support is actually decent, which shocked the shit out of me.
Mobile device support is where things get weird. iOS works through the app, Android integration is better but still feels bolted on. Don't even think about managing BYOD devices without wanting to drink heavily.
What You're Actually Getting
Real-time protection that doesn't completely murder your CPU, unlike some EDR solutions that turn every machine into a space heater. The cloud analytics piece is where Microsoft actually knows what they're doing - they see more Windows telemetry than God.
KQL hunting queries are powerful but prepare to hate your life while learning them. If you don't have a security analyst who speaks KQL, budget for training or hiring someone who does. The learning curve is vertical.
Automatic incident response works about 70% of the time. The other 30% you'll be manually cleaning up whatever it decided was "suspicious" - usually your legitimate admin tools or that one developer who insists on running unsigned PowerShell scripts.
The Microsoft Integration Tax
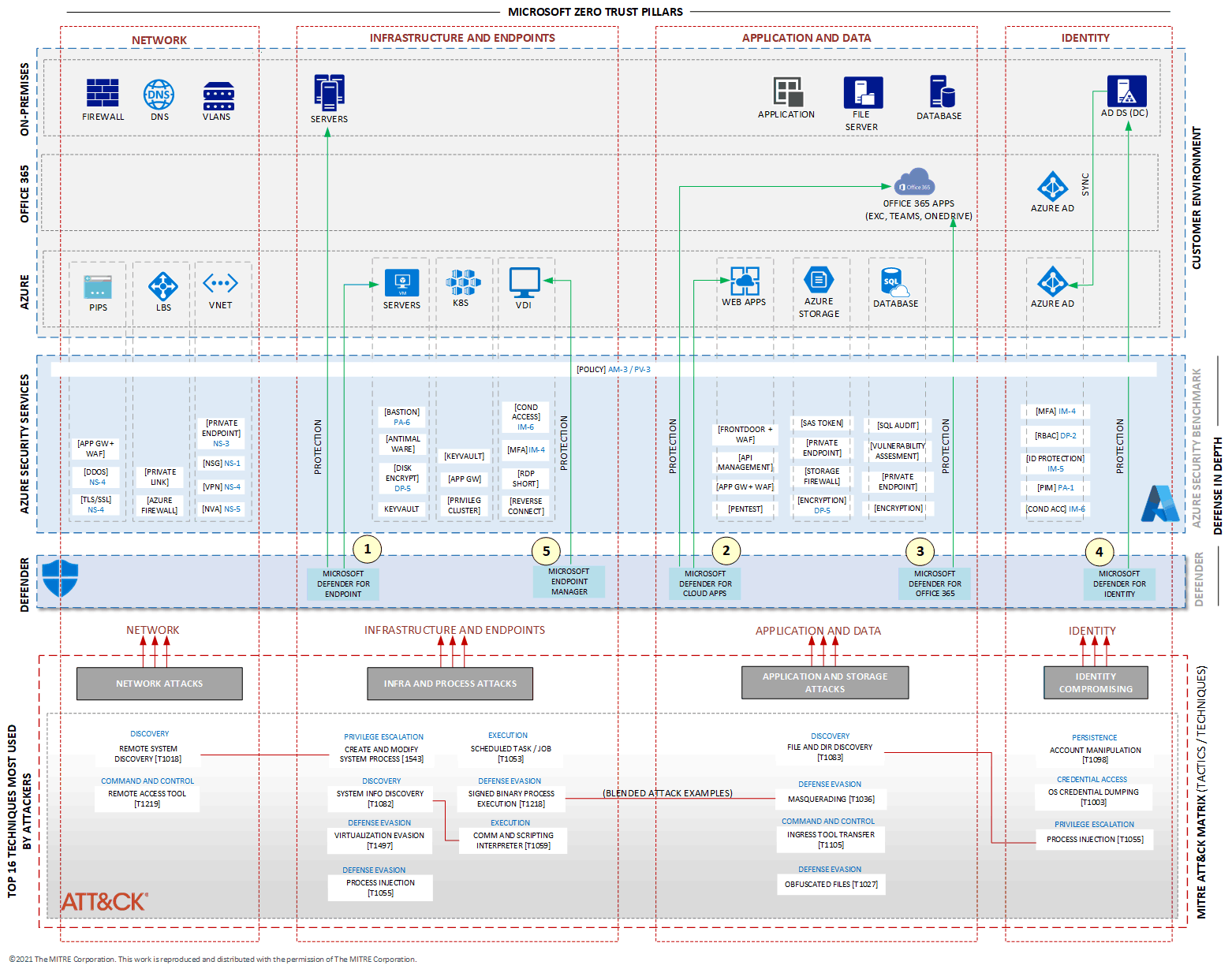
Here's what they don't tell you upfront: this thing integrates with everything Microsoft, which sounds great until you realize you now need licenses for Defender XDR, Sentinel, Intune, and whatever other acronym soup Microsoft is selling this quarter.
The Microsoft 365 E5 integration is smooth, but good luck explaining to finance why your "free" Windows Security now costs like $60 per user per month.
The good news is the Azure AD integration works without the usual Microsoft authentication headaches. Device compliance policies actually enforce what they say they will, and the conditional access rules don't randomly lock everyone out (looking at you, every other Microsoft product).
You'll also get dragged into the Microsoft Defender XDR ecosystem, which means learning another dashboard that looks suspiciously similar to the last three Microsoft security consoles. At least the threat intelligence feeds are decent - Microsoft actually sees a lot of real attack data from their massive install base.
As of September 2025, Microsoft has been pushing multi-tenant endpoint security policy distribution, which is great if you're an MSP managing multiple clients and terrible if you're trying to keep things simple. The new custom installation paths for Linux and offline security intelligence updates for macOS actually solve real problems, assuming you have the patience to test them properly.
The onboarding process varies by platform - Windows deployment is the smoothest, macOS needs additional config that'll make you question Apple's security model. For Linux endpoints, expect to spend quality time with package managers and custom repositories. Mobile device management through Intune works but needs careful policy configuration to avoid breaking legitimate apps. Don't forget to check system requirements before deployment, especially for older Windows versions that Microsoft pretends still exist.