RHACS 4.8 Compliance:
What's Actually Fixed vs What's Still Broken
Look, RHACS 4.8 fixed some shit, but it's still not the magical compliance solution Red Hat sells you on.
I've been running it in production since the 4.8 GA release in July 2025, and here's what actually changed versus what's still a pain in the ass.
The compliance scanning used to fail with completely useless errors like "scan failed: internal error"
- turns out it was memory limits every damn time.
That's mostly fixed now
- the 4.8 release finally includes proper error reporting when scans fail. But the scanner still hits memory limits on larger clusters and dies silently. Pro tip: RHACS 4.8.1 has a memory leak in the network flow migration that killed our dev cluster during upgrade.
Pin to 4.8.3 or later.
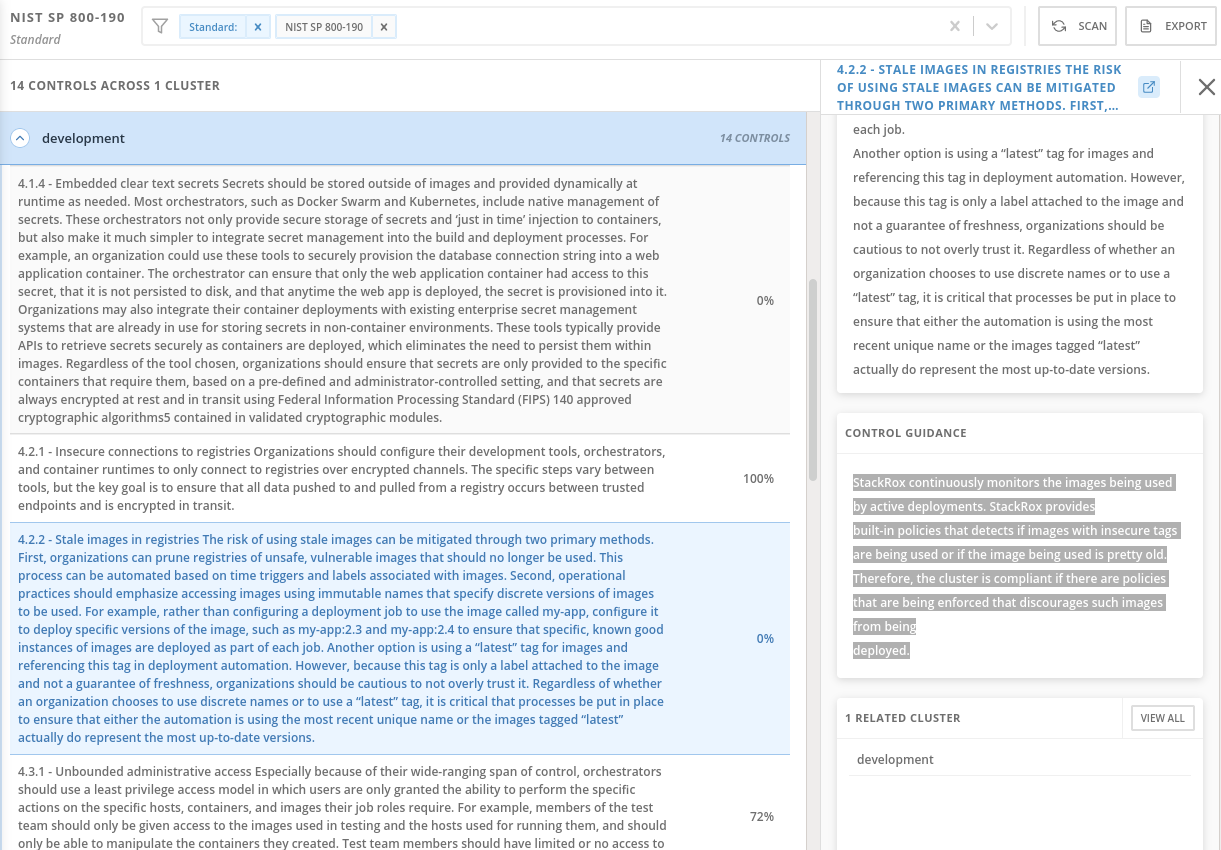
What Compliance Standards Actually Work
Standards that work out of the box:
- CIS Kubernetes Benchmark
- CIS standards are solid.
RHACS gets about 90% of these right. The remaining 10% are edge cases where your environment doesn't match CIS assumptions
- NIST SP 800-190
- [NIST container guidelines](https://nvlpubs.nist.gov/nistpubs/Special
Publications/NIST.
SP.800-190.pdf) map well to RHACS capabilities, but expect to tune policies for weeks
Standards that need heavy customization:
- HIPAA
- Works but requires massive policy tuning.
Every healthcare org has different PHI classification rules
- PCI DSS
- PCI requirements are strict as hell.
RHACS helps with technical controls but won't handle your network segmentation headaches
- SOC 2
- Good for security criteria, useless for availability and processing integrity
What doesn't work:
- OpenSCAP on OpenShift
- SCAP integration is clunky.
The compliance operator works but generates different findings than RHACS native scanning, confusing your auditors
RHACS 4.8:
What Actually Got Better
OpenShift Infrastructure Compliance Actually Works Now
The infrastructure compliance operator finally graduated from tech preview hell. RHACS infrastructure scanning now works with the compliance operator without crashing every other scan.
But it's still slow as fuck
- budget 30 minutes per cluster.
Compliance Reports Don't Die When One Cluster Fails
This was a massive pain point. If any cluster in your fleet failed scanning, you'd get zero compliance reporting. 4.8 fixes this
- failed clusters get marked as "scan failed" instead of breaking everything.
Policy as Code Is Finally Stable
Policy as Code moved from "tech preview that will eat your homework" to "actually works in production." You can manage policies as Kubernetes custom resources and integrate with GitOps workflows.
The CRD validation is solid and won't accept broken policy configs anymore.
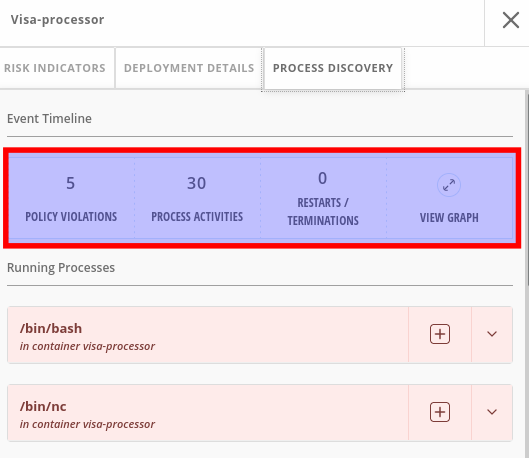
What RHACS Actually Collects (And What It Misses)
The compliance scanner grabs a shit-ton of data from your clusters, but understanding what it actually captures versus what auditors want to see is critical:
What it captures well:
- Docker daemon configs and runtime settings
- solid coverage here

Kubernetes RBAC policies and access patterns
excellent for auditor questions
Network policies and pod-to-pod communication rules
Container image vulnerability data from Stackrox Scanner V4
way faster than the old scanner
Pod Security Standards compliance across namespaces
What it struggles with:
File system permissions on worker nodes
hit or miss depending on your node setup
Runtime behavior analysis generates tons of false positives in microservice environments
Supply chain verification works great until you have private registries with custom cert chains
What auditors want but RHACS doesn't provide:
Data flow diagrams showing where PHI/PCI data actually goes
Change management audit trails for infrastructure modifications
Business process documentation linking technical controls to compliance requirements
The scanner is a resource hog on big clusters.
Had to bump memory limits after it kept crashing on our 400+ node production cluster.
Regulatory Reality Check
**HIPAA
- Healthcare's Special Hell:**
HIPAA technical safeguards sound straightforward until you realize every hospital defines PHI differently.
RHACS can enforce encryption and access controls, but you'll spend more time arguing with your legal team about data classification than configuring policies.
Real implementation time: 4-6 months, not the 6-8 weeks consultants promise.
Most of that time is figuring out which workloads actually process PHI versus which ones just might.
**PCI DSS
- Payment Card Nightmare:**
PCI DSS requirements are brutal.
Network segmentation requirements mean your microservices architecture just became a compliance clusterfuck. RHACS helps with vulnerability scanning and access control, but won't solve your network isolation headaches.
Expect your PCI audit to take 6 months longer than planned because your auditor will question every network policy exception.
**SOC 2
- The Documentation Grind:**
SOC 2 Trust Services Criteria are about demonstrating control effectiveness over time.
RHACS collects great technical evidence, but your auditor wants process documentation and change management records.
Type II audits are 12 months of documentation hell. RHACS automates evidence collection but someone still needs to write all the process documents auditors demand.
Enterprise Integration Hell
Automated Evidence Collection (That GRC Teams Hate):
RHACS generates tons of compliance evidence, but in formats that don't play nice with enterprise GRC tools.
You'll build custom export scripts for every audit cycle. ServiceNow GRC integration exists but requires custom API work.
Continuous Monitoring (That Creates Alert Fatigue):
Real-time compliance alerting sounds great until you're getting 200 alerts per day for policy violations that don't actually matter.
Tuning takes months and your SecOps team will hate you.
Third-Party Integration (API Hell):
Integrating with Splunk, Archer, or other GRC platforms requires custom development.
Budget 3-4 weeks because Service
Now's GRC API documentation was clearly written by someone who's never used it. Half the endpoints don't work as documented, and plan for ongoing maintenance when vendors change their APIs.
Now that you understand what actually works and what's broken in RHACS 4.8, let's look at the real implementation timelines for each compliance framework. Spoiler alert: they're all longer than Red Hat claims.

