RHACS 4.8 dropped in July 2025, and while Scanner V4 is supposed to be better than the old scanner that would crash randomly, it still chokes on those massive Node.js images your developers love to build. Trust me, when the entire team pushes at 5 PM on Friday, you'll find out real quick where the performance limits are.
Your devs are pushing containers to prod right now, and half of them probably contain dependencies with critical CVEs from 2019 that nobody's bothered to patch. RHACS integration will fuck up your pipeline on day one. Plan on spending a month unfucking the policies while developers complain that security is ruining their lives.
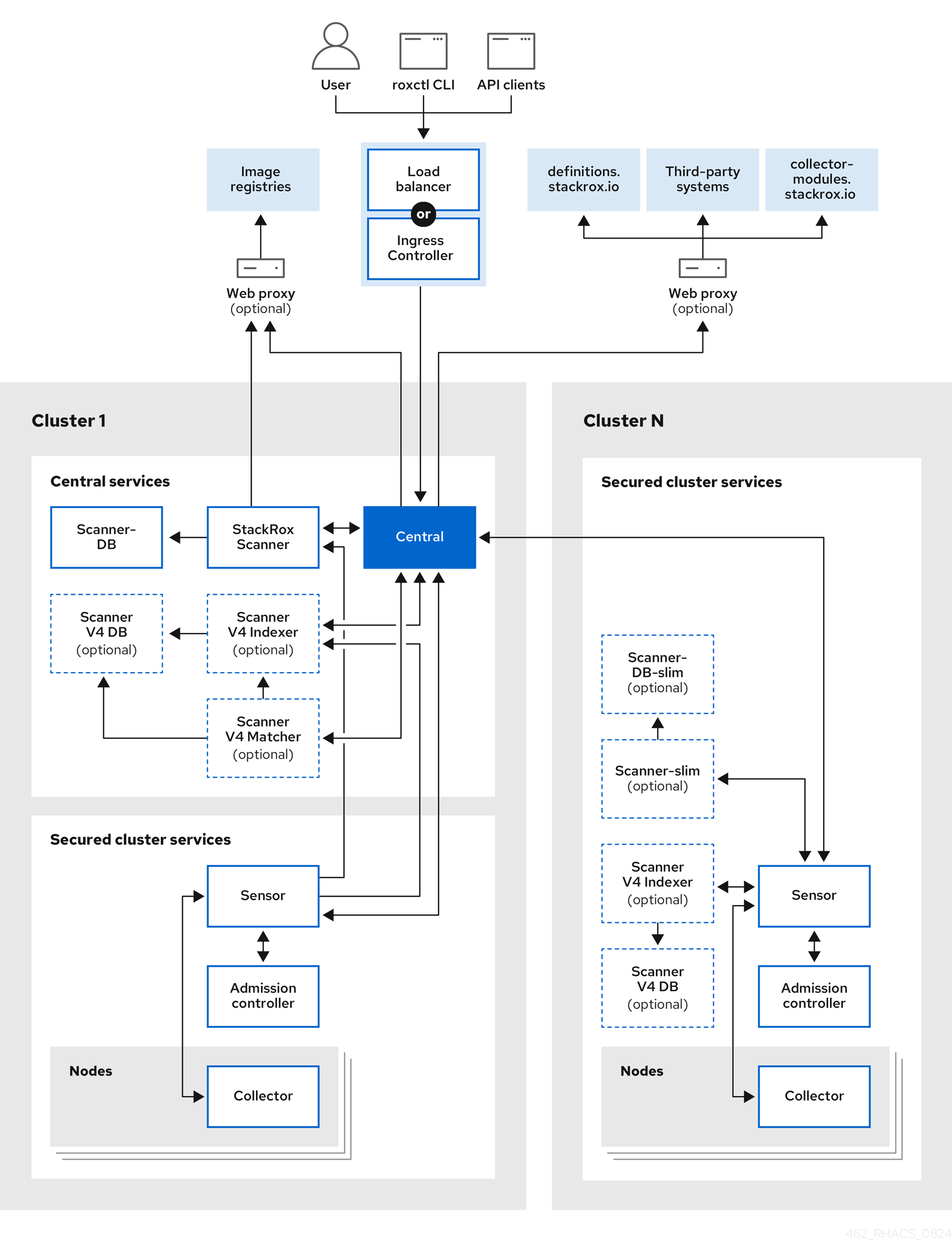
Here's how to actually integrate this thing
RHACS hooks into your CI/CD through the roxctl CLI and Kubernetes admission controllers. The sales pitch is simple: scan images during build, check deployment policies before deployment, block the bad stuff. Reality check: plan on weeks of policy tuning unless you enjoy getting paged at 2 AM because someone's legitimate deployment got blocked by an overzealous policy.
The official docs show you the demo setup. In real life, you'll spend weeks tuning policies so they don't break every single deployment. The defaults flag every container that runs as root - which kills half your infrastructure.
What actually works:
- Image scanning with
roxctl image scancatches most CVEs before deployment, though it'll miss zero-day vulnerabilities - Deployment checking with
roxctl deployment checkvalidates Kubernetes YAML against security policies - Admission controller enforcement blocks policy violations at the cluster level, though it adds 100-300ms latency to each deployment
- Registry integrations with Harbor, Quay, AWS ECR, Azure Container Registry, and Google Container Registry usually work without much hassle
What actually breaks:
- Default policies are fucking insane - they'll flag every container running as root, which breaks system containers, init containers, and half your infrastructure. Day one: every deployment fails. Spent 3 days figuring out why our logging sidecars died
- False positives everywhere during setup. I've spent entire sprints tuning policies while devs complain that security is "blocking innovation." One policy flagged our monitoring stack because Prometheus runs as root - obviously it fucking does
- Scanner V4 still dies on bloated Node.js containers during peak hours. You know the ones - 2GB images with every npm package ever created. Had a React app that pulled in like 800+ dependencies or something crazy. Took forever to scan and the devs threatened to push straight to prod
- Network issues between roxctl and Central in corporate networks with undocumented firewall rules and proxy configs nobody knows about. Spent a Tuesday troubleshooting why scans worked from my laptop but died in Jenkins
- Authentication failures with roxctl give you
exit code 13and zero useful info. Usually means your API token expired or has wrong permissions. The troubleshooting guide won't help much - just delete and recreate the damn API token. Happened to me twice last month
The Three Integration Patterns That Actually Work
1. Fail-Fast Image Scanning (Recommended Start)
Scan images early in the build process using roxctl image scan. This catches vulnerabilities before they reach your registry. Start with informational scanning, gradually enable enforcement as your images clean up.
## Basic CI/CD image scanning
roxctl image scan --image myapp:latest --endpoint $RHACS_CENTRAL_ENDPOINT --token $RHACS_API_TOKEN
2. Registry-Triggered Scanning
Configure RHACS to automatically scan images when pushed to your registry. Works well with Harbor, Quay, and cloud registries. Reduces CI/CD pipeline complexity but scanning happens after build.
3. Pre-Deployment Policy Validation
Use roxctl deployment check to validate Kubernetes manifests against security policies before deployment. Catches misconfigurations that image scanning misses.
## Validate deployment manifests
roxctl deployment check --file deployment.yaml --endpoint $RHACS_CENTRAL_ENDPOINT --token $RHACS_API_TOKEN
CI/CD platform integration hell
Jenkins Integration: Works Until It Mysteriously Doesn't
Jenkins has the most mature RHACS integration through the StackRox Container Image Scanner plugin. It mostly works, but I've seen the plugin randomly lose API tokens after Jenkins restarts, and the error messages are useless. The official Jenkins integration docs give you basic examples, but the Red Hat workshop labs have more realistic scenarios.
Happened to us: plugin works fine for weeks, then Jenkins auto-updates and boom - every build dies with "Error code 13." Spent half the day figuring out the restart corrupted some auth bullshit. Turns out the plugin stored tokens in some temp directory that got wiped during the restart.
GitLab CI Integration: YAML Hell but Actually Reliable
GitLab requires you to write custom YAML configs, but at least you get full control over the process. Red Hat's Trusted Application Pipeline docs are actually decent and the examples work - unlike most vendor documentation that assumes your environment matches their demo setup perfectly.
GitHub Actions Integration: Minimal but Gets the Job Done
GitHub Actions has basic RHACS support through Red Hat's Trusted Application Pipeline, but don't expect much hand-holding. Documentation is thin, so you'll be reading GitHub Actions YAML examples and figuring out the rest. Works fine for simple use cases.
Azure DevOps Integration: DIY Everything
Microsoft and Red Hat clearly didn't prioritize this. You're stuck writing custom scripts and calling roxctl commands manually. It works, but expect to write a lot of PowerShell or bash scripts to make it happen.
Policy tuning without getting fired
RHACS comes with like 375 security policies out of the box. Some make sense, others are completely nuts. The "no root containers" policy will break every sidecar, init container, and piece of infrastructure you actually need to run.
How to tune policies without your team wanting to murder you:
- Start everything in "inform" mode. Don't break builds on day one unless you enjoy being the most hated person in engineering
- Look at violation patterns for a few weeks. You'll discover that 80% of violations come from 3-4 policies that make no sense in your environment
- Enable enforcement for the real stuff first: critical CVEs, privilege escalation, secrets in environment variables
- Gradually enable more policies based on what won't make developers bypass your entire security setup
- Use policy scopes to be strict in prod, relaxed in dev
The Policy as Code feature in RHACS 4.8 finally moved from tech preview to GA. You can now manage policies as Kubernetes custom resources and integrate them into GitOps workflows. This is actually useful for teams that want policy management in their existing Git workflows, though you'll need to understand both RHACS policy syntax and your application requirements.
Performance and scaling shit
Scanner V4 is supposed to be better than the old scanner, but it'll still eat your resources if you let it. Give it decent CPU and RAM - depends on your image sizes and how many teams are scanning at once. During peak hours when everyone pushes at once, scanning becomes a bottleneck fast.
Red Hat's sizing guidelines are theoretical bullshit - your mileage will vary based on your weird images and whatever network setup you inherited. Check their performance guide then prepare to tune everything anyway.
Scaling patterns that work:
- Enable delegated scanning on clusters with heavy CI/CD workloads
- Use registry mirrors geographically close to your CI/CD infrastructure
- Cache scanned image layers to avoid redundant scanning
- Schedule compliance scans during off-peak hours
This stuff mostly works once you get it configured right. The hard part is figuring out which integration pattern works with your specific CI/CD setup.