Look, I'll be straight with you. If you're running containers in production without proper security scanning, you're basically asking for trouble. Checkmarx Container Security exists because regular SAST tools miss the massive security hole that containerization creates.
The Three Ways Containers Screw You Over
Base images are security nightmares. Every ubuntu:18.04 container you deploy comes pre-loaded with dozens of critical vulnerabilities that'll make your security team panic. That "harmless" Node 14 Alpine image? Yeah, it's got enough CVEs to keep penetration testers busy for weeks. Check the Ubuntu security notices if you want to see how many vulnerabilities your base images actually contain.
Package managers don't give a shit about security. When `npm install` or `pip install` runs during your Docker build, it's pulling in vulnerable dependencies that your regular code scanning never sees. Supply chain attacks went up 742% last year according to Sonatype's research. I watched one team spend 3 months tracking down vulnerabilities that Dependabot flagged - turned out they were all in container layers that nobody bothered scanning.
Runtime configurations are a fucking mess. Containers deploy with hardcoded database passwords in environment variables, root privileges they don't need, and exposed management interfaces that scream "please hack me." The CIS Docker Benchmark documents hundreds of configuration mistakes, but static analysis tools can't catch this shit because it only becomes a problem when the container actually runs. Read the NIST container security guide for the full horror show of runtime configuration vulnerabilities.
Checkmarx uses Syft technology to tear apart your container images layer by layer. It finds packages across more languages than you probably even use - Go, Rust, Python, Node, plus weird stuff like Dart and Haskell that nobody else bothers checking.
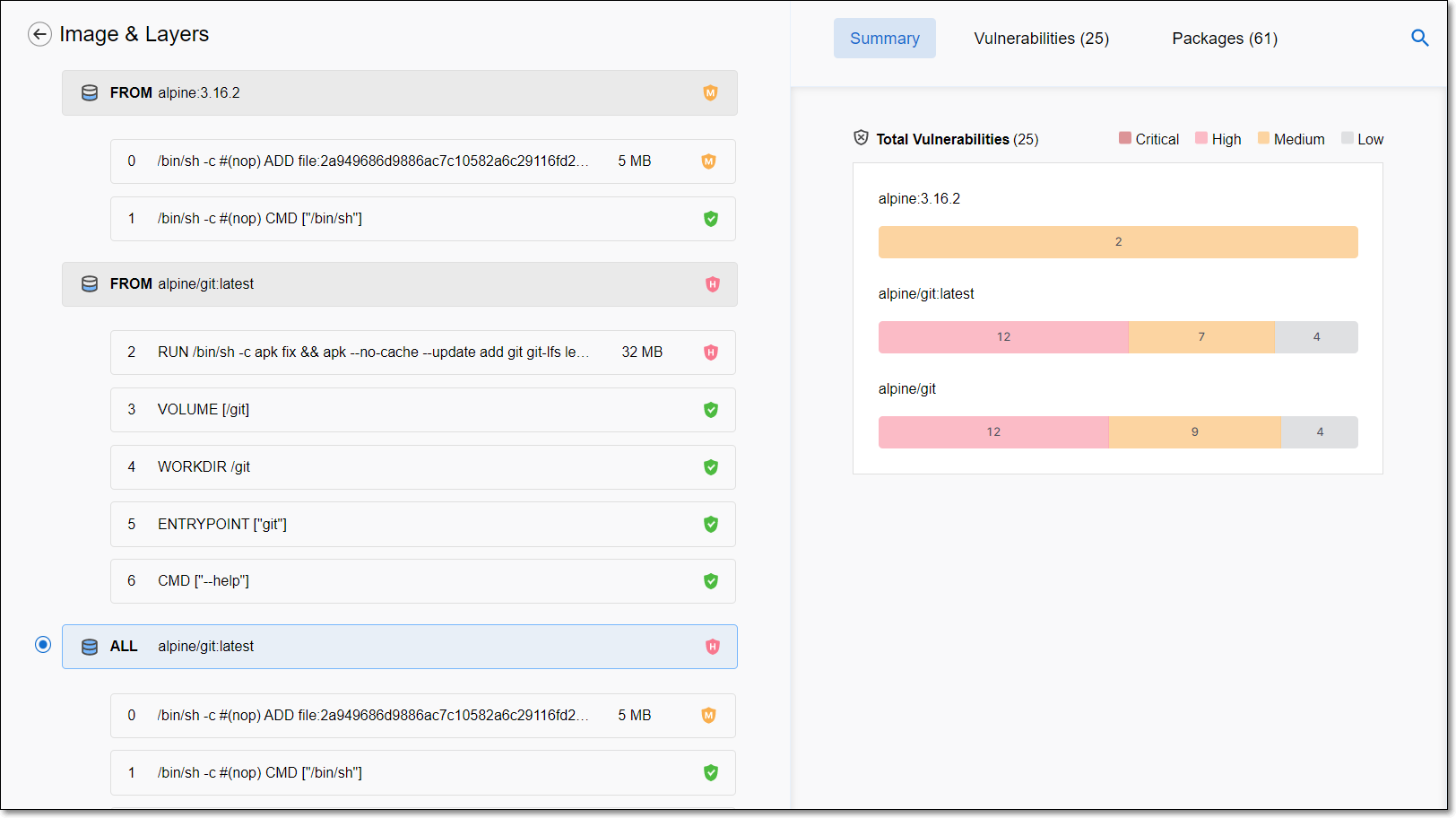
Container scanning tears apart each layer of your image - base OS packages, language dependencies, application code, the whole fucking mess. Each layer adds more vulnerabilities until you're staring at 200+ security issues in what you thought was a simple web server.
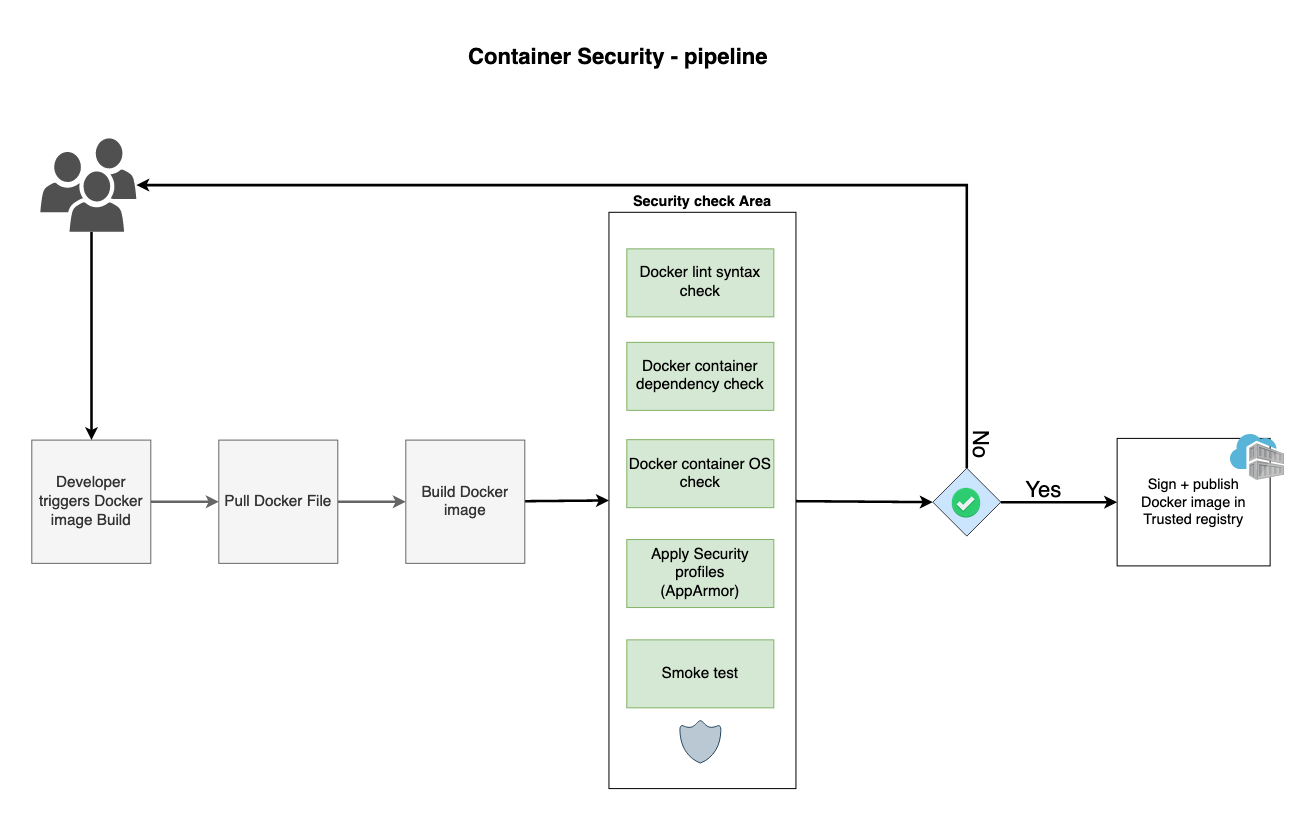
How This Thing Actually Works
Checkmarx splits container security into three parts that you'll implement in order (or everything breaks):
Dev tools that don't suck: The Docker Desktop extension actually works without account setup or authentication hell. It scans your local images and tells you immediately when you're about to deploy garbage. Docker Desktop extension works great until you try to scan a private registry and spend 3 days debugging authentication tokens.

CI/CD integration that'll slow down your builds: The CLI hooks into your pipelines and adds 5-30 minutes to every deployment (depending on how many containers are queued). Supports cloud scanning if your registry plays nice, or local scanning if you enjoy watching Docker pull gigabytes of base images.
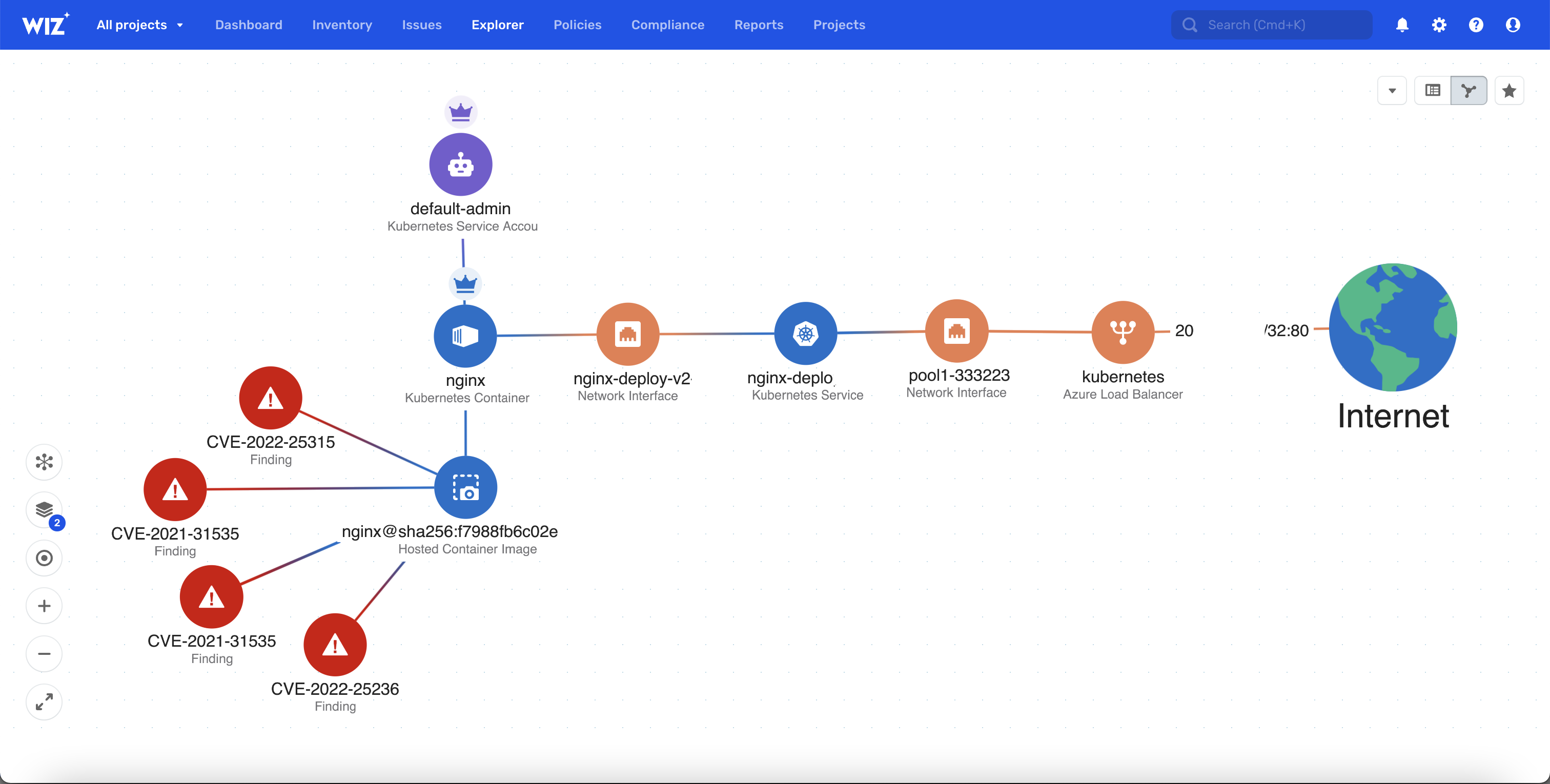
Production correlation that costs extra: Sysdig integration shows which vulnerabilities in production containers are actually being exploited. Spoiler alert: it's like 3% of them, but you need to pay for both Checkmarx AND Sysdig licenses to find out which 3%.
The incremental approach sounds great until you realize each step introduces new failure modes. Docker Desktop extension works great until you hit a private registry and authentication breaks mysteriously. CI/CD scanning works until you exceed concurrent scan limits and builds start queuing for 30 minutes. Runtime correlation works until you realize you're paying $150k+ annually for tools that tell you 97% of your vulnerabilities don't actually matter.
The Parts That'll Cause You Headaches
Image scanner that actually works: Checkmarx tears apart your Dockerfiles, docker-compose configs, and Helm charts to find every vulnerability hiding in your container layers. Unlike the basic scanners that only check your application packages, this thing digs into every layer of your base images to find shit you didn't even know was there.
When I say "comprehensive," I mean it finds vulnerabilities in packages you forgot you inherited from that Ubuntu base image you copied from some random blog post three years ago. It'll discover dependency vulnerabilities in languages you don't even use but somehow ended up in your container ecosystem.
Private registry nightmare: Supports major registries like AWS ECR, Google Artifact Registry, Azure Container Registry, plus Harbor and Nexus if you're into self-hosted complexity. Cloud scanning works when authentication doesn't randomly break. Local scanning with Docker/Podman works when you enjoy waiting for multi-gigabyte image pulls in your CI environment.
Policy engine that'll make developers hate you: Configure thresholds that block deployments based on vulnerability severity, age, and type. Start with "critical vulnerabilities older than 10 days" so hotfixes don't get blocked, then watch developers find creative ways to work around your policies when you get stricter.
Runtime correlation that costs a fortune: The Sysdig partnership identifies which vulnerabilities actually matter in production. Sounds great until you realize this cuts the bullshit alerts by 95%, meaning you were panicking about 95% of vulnerabilities that don't actually pose real risk.
Reality check: this shit requires getting authentication working across dev, CI/CD, and production without everything breaking, configuring policies that don't make developers hate you, and convincing three different teams to actually change how they work. Budget 2-3 months and expect at least one complete authentication meltdown that takes down deployments for a day.
The Docker Desktop extension actually has a decent interface that shows vulnerability counts and remediation suggestions without making you navigate through enterprise vendor hell. It's probably the only part of this whole setup that won't make you want to throw your laptop out the window.