What is Sysdig Secure
Sysdig Secure watches your cloud stuff while it's actually running and catches attacks that slip past everything else.
Most security tools check your setup when nothing's happening - they miss shit that matters when you're actually under attack. Sysdig watches your apps while they're running and catches the real problems.
It's built on Falco, which graduated from CNCF in February 2024 and is actually battle-tested. The runtime detection catches zero-days that signature-based tools completely whiff on.
Why Runtime Detection Actually Matters
Here's the thing: most security tools are looking in all the wrong places when the attack is already happening.
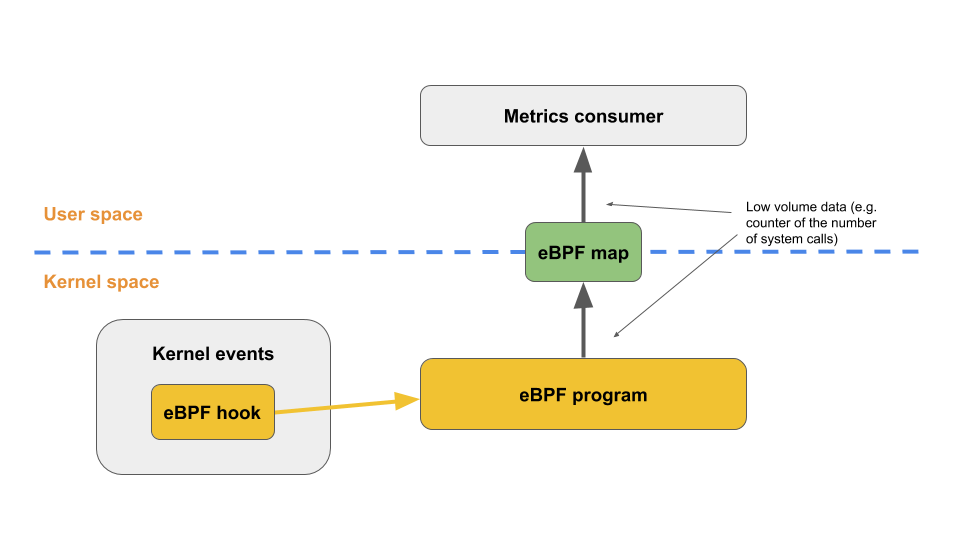
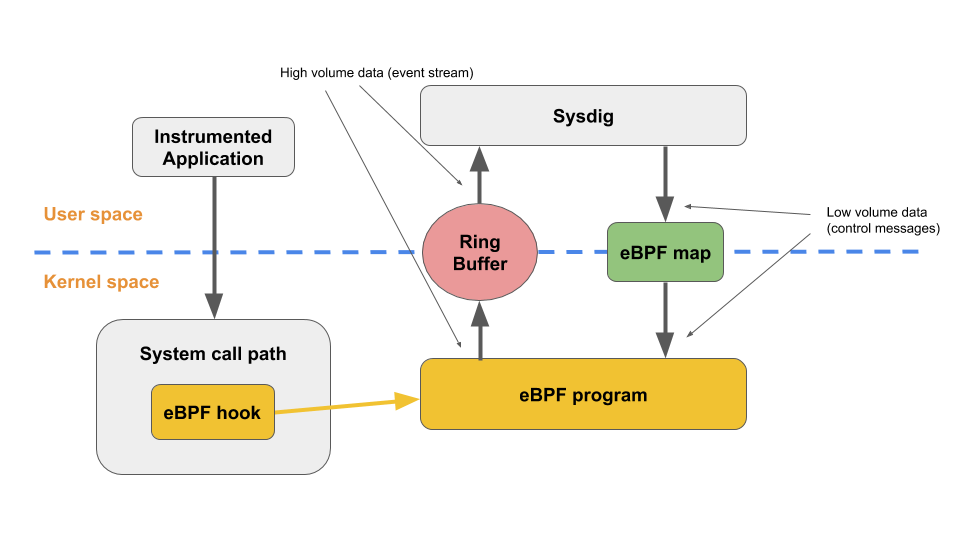
Sysdig uses eBPF to watch system calls in real-time, so it catches behavioral anomalies that signature-based tools never see. The performance impact is minimal - maybe 1-2% CPU overhead in most cases, though heavy workloads might see a bit more.
What it actually catches: Container escapes when something breaks out of its sandbox, crypto miners that hide behind legitimate binaries, lateral movement through weird network hops and privilege escalations, plus zero-day exploits that your signature-based tools never see coming.
Sysdig Sage AI Thing
They enhanced Sysdig Sage in 2025 with better platform integration - originally launched in 2023, but the 2025 updates actually made it useful. Basically ChatGPT for security investigations that doesn't completely suck now.
The AI correlation is actually pretty useful - instead of getting 10,000 individual alerts, it groups related events and shows you potential attack paths. The natural language search works well for non-security people who need to investigate incidents but don't know the syntax.
Real use case: Instead of learning complex query syntax, you can ask "show me all containers that made outbound connections to suspicious IPs in the last hour" and it figures out the rest. Though sometimes it gets confused by your custom labels and you end up writing the query manually anyway.
What It Actually Does
Sysdig tries to do everything in one tool. Configuration scanning finds your AWS buckets that are wide open and K8s pods running as root. Vulnerability management scans images and running workloads, but here's the useful bit - it prioritizes vulns in packages that are actually loaded and running, not just sitting on disk doing nothing.
Permission analysis spots overprivileged IAM roles and service accounts. Really helpful for cleaning up those "just give it admin for now" situations that never get fixed. Runtime protection is where Falco shines - catches weird behavior like processes spawning shells, unexpected network connections, privilege escalations.
The integration doesn't suck like most integrations - instead of juggling 5 different tools, you get one dashboard that correlates findings across all these areas. Less context switching, fewer false positives.
Real performance: Agent uses about 100-200MB memory depending on workload size. eBPF kernel integration means no dodgy kernel modules that can crash your nodes.
War story: Had this crypto miner that was a royal pain in the ass to find. AWS bill went crazy and took us way too long to figure out why. The thing was hiding behind normal processes but doing weird network shit to mining pools. Our expensive-as-hell security platform completely missed it - probably because it wasn't using some signature they knew about. Falco caught the weird behavior pretty fast once we got it running. Would've saved us a bunch of cash if we'd deployed it earlier instead of fucking around with other tools.
The bottom line? While other tools are busy scanning your infrastructure like it's a museum exhibit, Sysdig actually watches what's happening when attackers are already inside. That real-time visibility makes all the difference between catching an incident early versus explaining to your CEO why the entire AWS bill just tripled.