authentik replaces expensive SSO vendors like Okta, Auth0, and Azure AD. I run it on a $40/month DigitalOcean droplet for our 25-person startup and it handles everything Okta was charging us $375/month to do. That's a 90% cost reduction that goes straight to our bottom line.
The Setup Reality Check
The Docker Compose setup is straightforward if you follow their docs exactly. Don't try to get clever with the database config - just use their PostgreSQL defaults or you'll spend hours debugging connection timeouts.
Key gotchas from my deployment:
- Memory: Needs minimum 2GB RAM. I tried 1GB initially and it swapped itself to death
- PostgreSQL version: Version 2025.4+ requires PostgreSQL 16+. The upgrade breaks things if you don't follow their migration guide
- Initial admin: Save the recovery key or you'll be locked out. I learned this the hard way
The official Docker images are updated regularly, and their security guide covers hardening practices you'll actually need.
Protocol Support That Actually Works
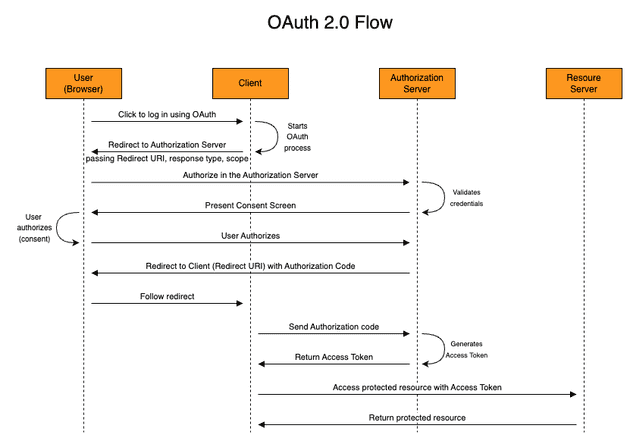
It supports OAuth2/OIDC, SAML, LDAP, and RADIUS. OAuth2 is plug-and-play with modern apps. SAML works but the config is fiddly - expect to spend time tweaking XML attributes for legacy enterprise apps.
The outpost system is clever - you can run auth components where you need them instead of proxying everything through one chokepoint. Saved my ass when dealing with geographically distributed services. The proxy provider handles forward auth beautifully with Traefik or nginx.
MFA and Security Features
MFA works great - I use Google Authenticator and my YubiKey. WebAuthn/Passkeys were a pain to set up initially but work flawlessly once configured. The security keys documentation is actually helpful.
The flow system lets you customize auth workflows. It's powerful but overcomplicated for basic SSO - I spent way too much time in the flow designer when simple defaults would've worked fine. The default flows cover most use cases without customization.
That said, you're probably wondering how authentik actually compares to the big commercial players. Let me break down the real differences.
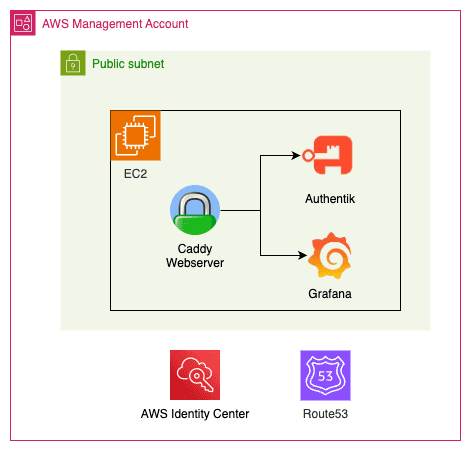
 authentik prioritizes flexibility over simplicity.
authentik prioritizes flexibility over simplicity.