What is a SAML Identity Provider?
A SAML Identity Provider is the thing that either makes single sign-on work beautifully or turns into a debugging nightmare that ruins your weekend. When it works, users log in once and magically access everything. When it doesn't work (which is 60% of the time), you'll be troubleshooting XML namespaces and certificate mismatches until you question your career choices.
SAML stands for Security Assertion Markup Language, but veterans call it "Shit Always Mysteriously Loses" because that's more accurate.
The Identity Provider acts as the authentication bouncer - it decides who gets in and stamps their metaphorical hand with a cryptographic assertion. The Service Provider (your actual app) trusts this stamp, assuming the IdP hasn't been compromised and the certificate hasn't expired (narrator: it has).
SAML Architecture: A 5-Step Dance to Failure
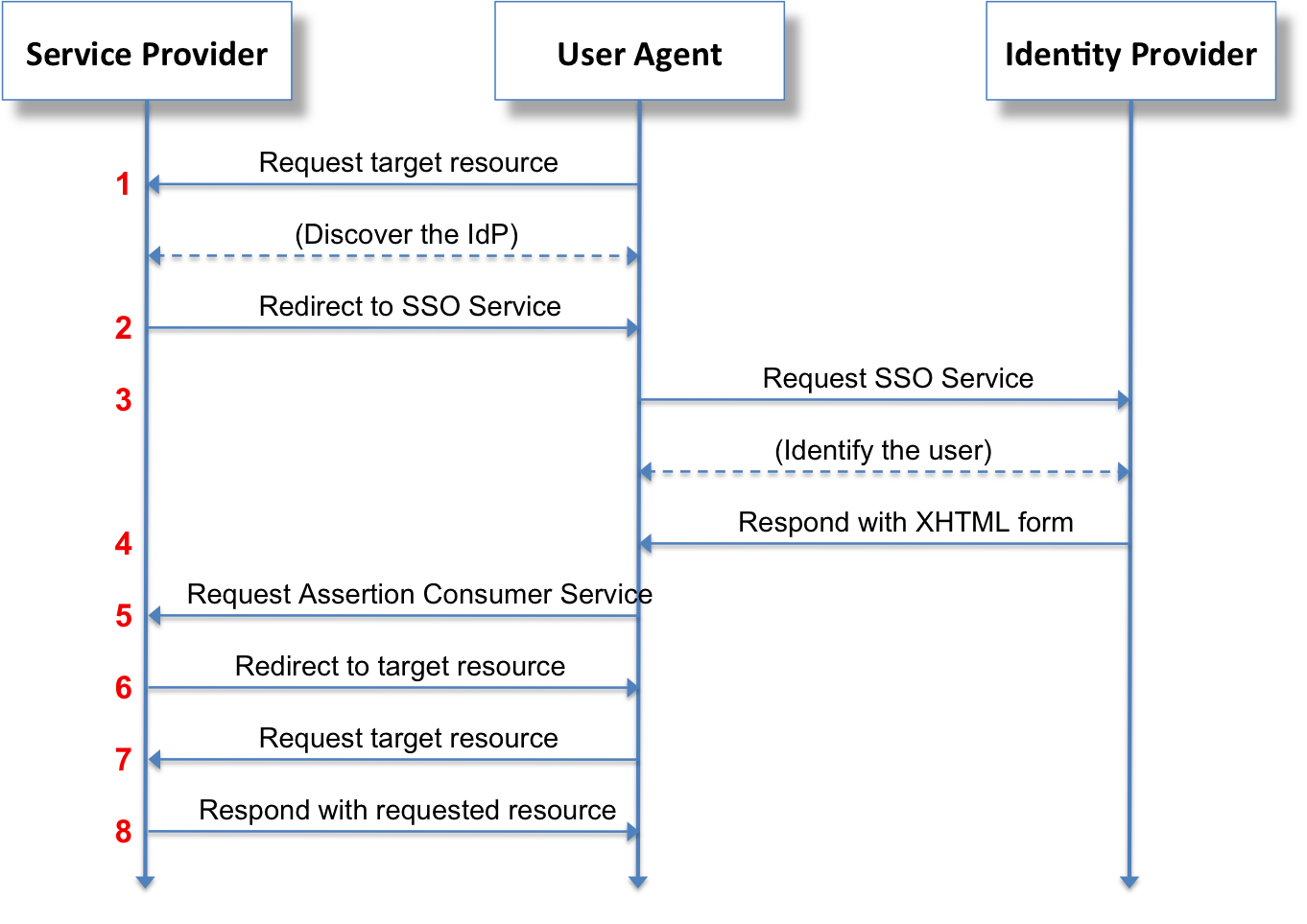
Complex multi-step authentication flow involving browser redirects and XML validation
SAML authentication flow - what could go wrong? (Everything.)
Here's how SAML should work:
- User clicks login - Easy part, nothing breaks yet
- Service Provider redirects to IdP - This is where certificate errors start appearing
- IdP authenticates user - If lucky, this works. If not, enjoy generic "Authentication Failed" errors
- IdP sends signed SAML response - Certificates expire here 73% of the time
- Service Provider validates response - Clock skew issues kill this step regularly
That perfect 5-step flow? It breaks at step 2 when your metadata doesn't match, certificates don't validate, or the response format changed in the latest vendor update.
What actually happens:
- User gets bounced between systems 4 times
- Error message says "Authentication Failed" (thanks, very helpful)
- You spend 3 hours discovering someone changed the signing algorithm
- Certificate expires during your vacation
- Production breaks because staging worked fine with different metadata
The theoretical advantages:
- Single sign-on: When it works, users love it
- No password storage: Until you need emergency access and realize everything's federated
- Attribute sharing: Assuming your LDAP schema matches what the app expects
- Audit trail: Great for explaining to auditors why authentication failed at 2am
Certificate Hell and Other SAML Fun Facts
Digital Signatures: Where Dreams Go to Die
SAML assertions are XML documents that get cryptographically signed to prove they're legitimate. Sounds simple? Ha.
Three types of SAML assertions that will break:
- Authentication Statements: "Yes, user logged in 5 minutes ago" - assumes your clocks are synchronized (they're not)
- Attribute Statements: User's email, role, department - assuming your LDAP attributes match what the app expects
- Authorization Statements: What the user can access - rarely used because nobody can figure out how to map permissions properly
Every assertion gets digitally signed with X.509 certificates. These certificates will:
- Expire during your busiest day
- Use different algorithms than your app expects
- Get revoked by your security team without warning
- Work perfectly in test but fail in production
Metadata: The Source of All Evil
SAML metadata describes how systems talk to each other. It's an XML file that contains endpoints, certificates, and capabilities. This file will:
- Get out of sync between environments
- Have different certificate fingerprints than expected
- Use HTTP URLs when you need HTTPS
- Work for everyone except your production setup
Protocol Bindings: Pick Your Poison
SAML supports different ways to pass messages around:
- HTTP Redirect: Puts SAML data in URLs. Breaks when URLs exceed browser limits (happens frequently)
- HTTP POST: Posts SAML in form data. Breaks when servers reject large POST bodies
- SOAP: For backend systems. Breaks when firewalls block non-standard SOAP headers
Each binding fails differently, giving you variety in your suffering.
Why Companies Still Use SAML Despite the Pain
Operational Efficiency (When It Works)
SAML centralizes user management, letting you provision/deprovision from one place instead of logging into 47 different admin panels. User onboarding drops from days to hours when everything's working, with automated user management improving operational efficiency by up to 70%.
Reality check: You'll spend those saved hours debugging why Sarah from accounting can't log into Salesforce.
Security Features That Actually Matter
- Multi-Factor Authentication: Works great until users lose their phones and blame IT
- Conditional Access: "User location: North Korea" - probably block that
- Session Management: Centrally log everyone out when you discover a breach
- Audit Logs: Perfect for explaining to auditors why someone accessed customer data at 3am
SAML vs. Everything Else
Authentication protocols compared: SAML's XML complexity vs. OIDC's JSON simplicity
SAML vs OpenID Connect - the eternal battle between XML complexity and JSON simplicity
- SAML: XML hell that enterprises love because "it's mature"
- OIDC: JSON-based sanity that works with mobile apps
- SAML: Does authentication and authorization poorly
- OAuth: Does authorization well, authentication not at all
The real choice: Use SAML for enterprise web apps because your compliance team demands it. Use OIDC for everything else because you want to stay sane.
Most smart companies run both protocols side by side. SAML for the corporate apps that finance approved in 2019, OIDC for the modern stuff developers actually want to build.
Bottom line: SAML works when implemented correctly by people who understand certificate management, XML namespaces, and why clock skew breaks everything. Unfortunately, most implementations are done by consultants who bill by the hour and disappear before things break in production.
