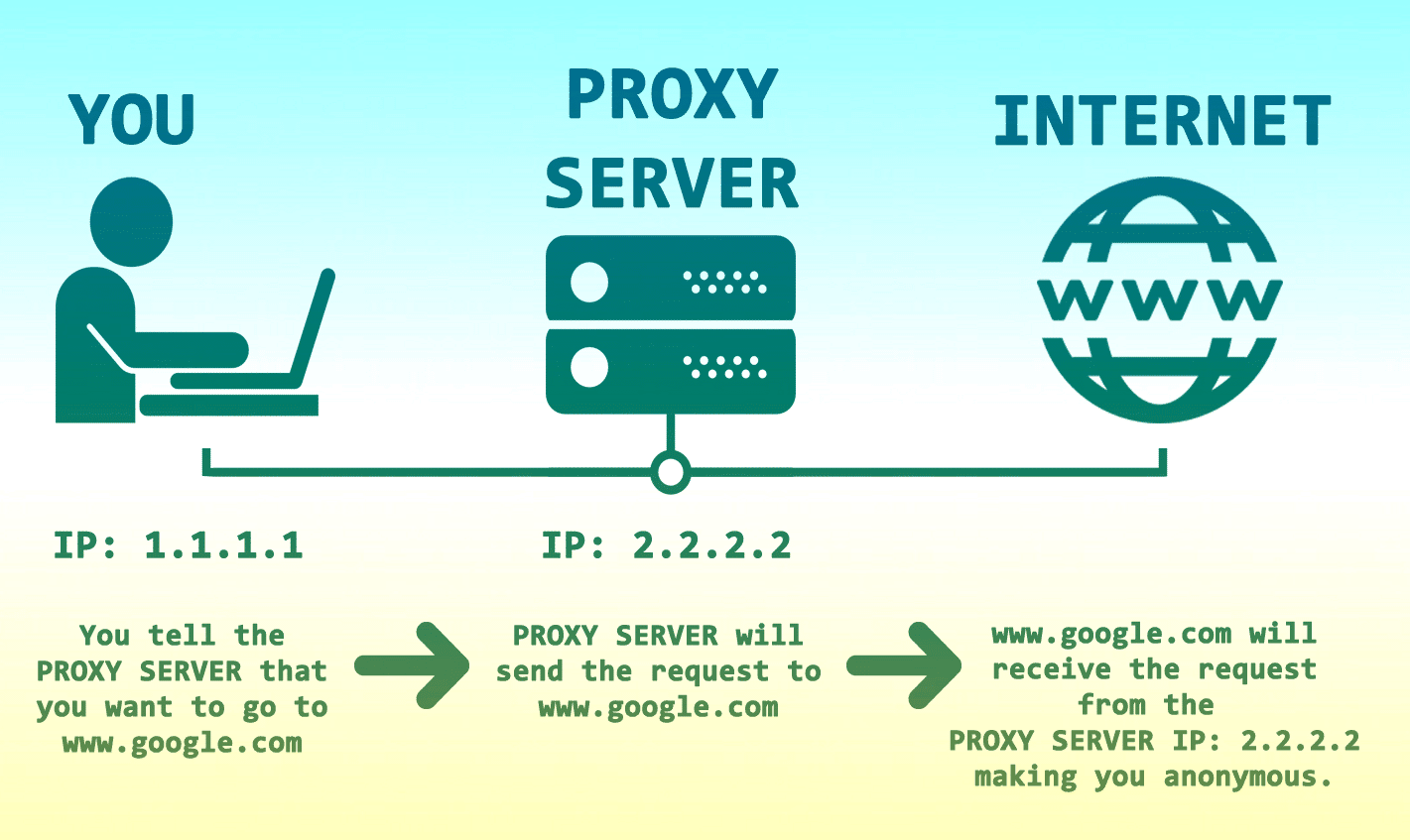
I started using 3proxy in 2019 when I needed a proxy for development testing and Squid was being a pain in the ass. Turns out 3proxy has been around since 2002 and is BSD licensed, so you can use it commercially without worrying about licensing bullshit.
The main reason I keep using it: it handles HTTP, SOCKS4/5, DNS proxying, and port forwarding in one binary. Most proxy tools either do HTTP well or SOCKS well, but not both. Squid is great for HTTP caching but SOCKS support is nonexistent. HAProxy is amazing for load balancing but it's complex as hell to configure for basic proxy needs.
3proxy just works. Install it, write a basic config, done. No enterprise bloat, no GUI nonsense, just a small C binary that does what you expect.
How It's Actually Built
You get separate binaries (socks, proxy, tcppm, udppm) if you want to run just one service, but honestly the main 3proxy daemon is easier to manage. I tried the separate binaries once to save memory but the difference was like 500KB - not worth the hassle of managing multiple processes.
What Protocols It Doesn't Suck At
Most proxy tools focus on one protocol and half-ass the others. 3proxy actually does them all properly:
- HTTP/1.1 and HTTPS - Works with browsers, curl, whatever. Handles CONNECT method properly for HTTPS tunneling
- SOCKS4/4a/5 - Actually supports UDP with SOCKS5, which a lot of implementations just ignore
- DNS Proxy - Caches DNS responses so you're not hitting 8.8.8.8 for every request like an idiot
- Port forwarding - TCP and UDP forwarding that doesn't randomly die like netcat tends to do
- Legacy protocols - POP3, SMTP, FTP proxying if you're stuck supporting ancient shit
Cross-Platform Bullshit You'll Encounter
3proxy runs on basically everything from Windows 98 to current stuff, which is impressive for a C program. Same config file works on Windows and Linux, unlike nginx where you need different setups for different platforms.
Gotchas I've learned the hard way:
- Windows service install fails silently if you don't run as admin - took me 20 minutes to figure that out
- Ubuntu puts binaries in
/usr/local/bin/3proxybut CentOS puts them in/usr/sbin/because why not - File paths use forward slashes everywhere, even on Windows. I spent an hour debugging why my log file wasn't working because I used backslashes
- Compilation from source is straightforward on Linux but you need the right Makefile for your distro
Memory Usage That Doesn't Suck
On my VPS, 3proxy uses about 3MB RAM when idle and maybe 12MB handling 200-300 concurrent connections. Total disk footprint is under 5MB including configs and logs.
Compare that to Squid, which happily ate 150MB on the same server just sitting there doing nothing. 3proxy uses threads instead of forking new processes for each connection, so you don't get that memory explosion problem where each connection costs you 2MB of RAM.
Features That Actually Work

3proxy comes with features that would cost you serious money from commercial vendors:
- Access control - Block by user, IP, domain, time of day. ACL syntax is weird but once you get it, you can do complex rules
- Authentication - Plain text passwords, hashed passwords, RADIUS if your company is into that masochism
- Bandwidth limits - Per-user quotas that actually work. Tried this with Squid once and it was a nightmare
- Proxy chaining - Route through multiple proxy hops. Useful for privacy setups or when your network is a mess
- Logging that doesn't suck - Custom formats, syslog integration, even ODBC database logging if you want to make yourself miserable
Config reloads with kill -USR1 work without killing connections, which is great. But if you have syntax errors, the reload fails and you're stuck with the old config. Always test with 3proxy -t first - learned that after accidentally breaking production.