Koi Security just raised $48 million from Battery Ventures and others to tackle a problem that makes security teams want to drink heavily: developers installing random shit on corporate networks.
The DC-based startup, founded by Unit 8200 veterans, targets the security nightmare of unmanaged software that traditional EDR tools completely miss. They've scaled to 500K+ endpoints and landed Fortune 50 clients, which suggests the problem is real and widespread.
EDR tools weren't designed for this modern shitshow where developers install random packages like they're collecting Pokemon cards.
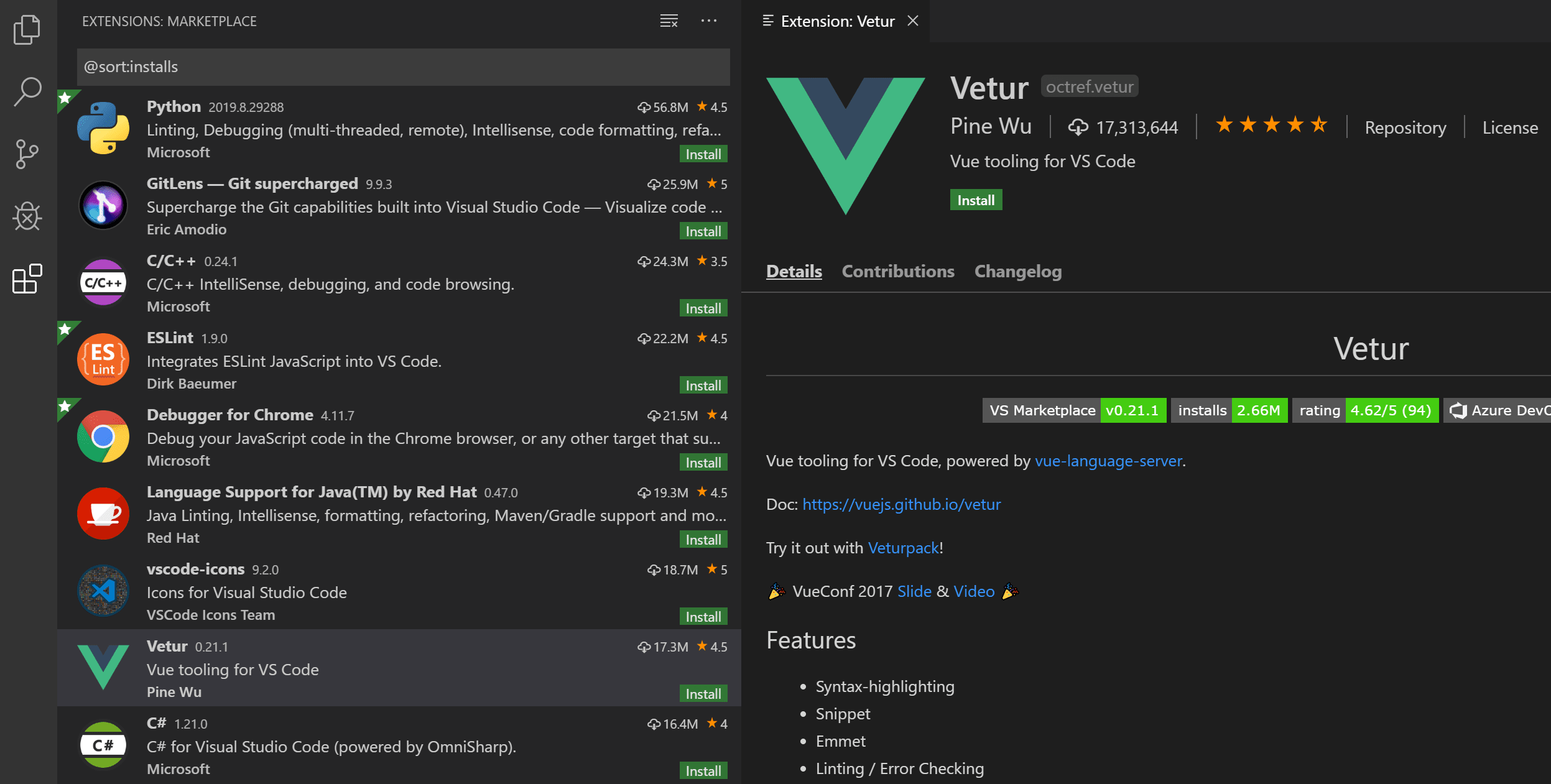
The VSCode Marketplace Discovery That Launched Koi
Koi's origin story demonstrates the severity of modern software supply chain risks. The founding team discovered a significant security vulnerability in how enterprises manage software through the VSCode Marketplace, Microsoft's central hub for Visual Studio Code extensions.
To prove the risk, they created a fake extension called "Darcula Official" - designed to mimic a popular dark theme but secretly steal source code and machine details. Within a week, this proof-of-concept extension had infected over 300 organizations worldwide, including multibillion-dollar companies and a national court network.
"Enterprises have no real control over the software flowing into their environments," explained Amit Assaraf, co-founder and CEO of Koi. "Packages, AI models, MCPs, and extensions are now critical parts of the stack, yet they remain invisible to traditional tools."
Beyond Traditional Binary Security
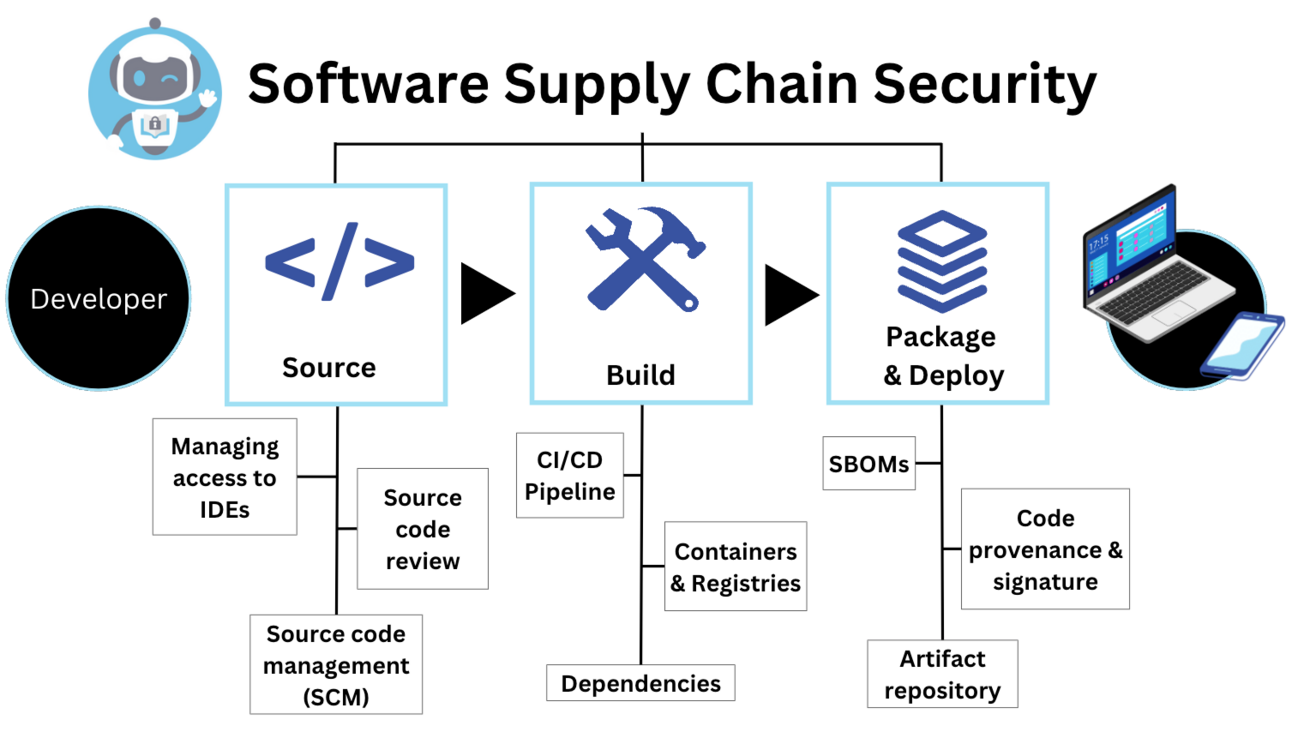
Traditional endpoint security focuses on compiled binary software, but modern enterprises increasingly rely on noncompiled software including code, operating system packages, containers, extensions, AI models, and model context protocol (MCP) services. These components operate at higher layers but retain the ability to access sensitive information like passwords, authorization keys, and proprietary code.
Koi's Supply Chain Gateway serves as a central checkpoint for all software accessing enterprise endpoints. The platform provides unified software inventory, real-time risk analysis, automated policy enforcement, and preventative fixes to block noncompliant components before they reach endpoints.
AI-Powered Threat Detection Engine
The company developed Wings, an AI-driven security engine that uses threat intelligence, classification, and sandboxing to identify threats that traditional scanners overlook. This approach enables Koi to detect sophisticated supply chain attacks that exploit the trust relationships inherent in modern software distribution.
From their initial VSCode research, Koi developed ExtensionTotal, a product specifically focused on detecting risky code editor extensions. This formed the foundation for their broader endpoint security platform, which now covers the entire enterprise software ecosystem.
The Inevitable Enterprise Wake-Up Call
The rapid enterprise adoption suggests security teams finally realize they have no fucking clue what's running on their networks. Traditional EDR solutions were built for an era when IT controlled all software installations. Now developers download whatever they need from npm, pip, VSCode marketplace, and random GitHub repos.
"We've built a product that enables organizations to curate what software is allowed in," says Assaraf. That's the diplomatic way of saying "we help you stop developers from accidentally installing malware."
Of course, knowing you need supply chain security and actually implementing it are two different things. Most enterprises will wait until they get pwned by a malicious npm package, then panic-buy whatever security vendor can fix it fastest.
The real question is whether enterprises will pay for proactive security or wait for the inevitable breach like they always do.