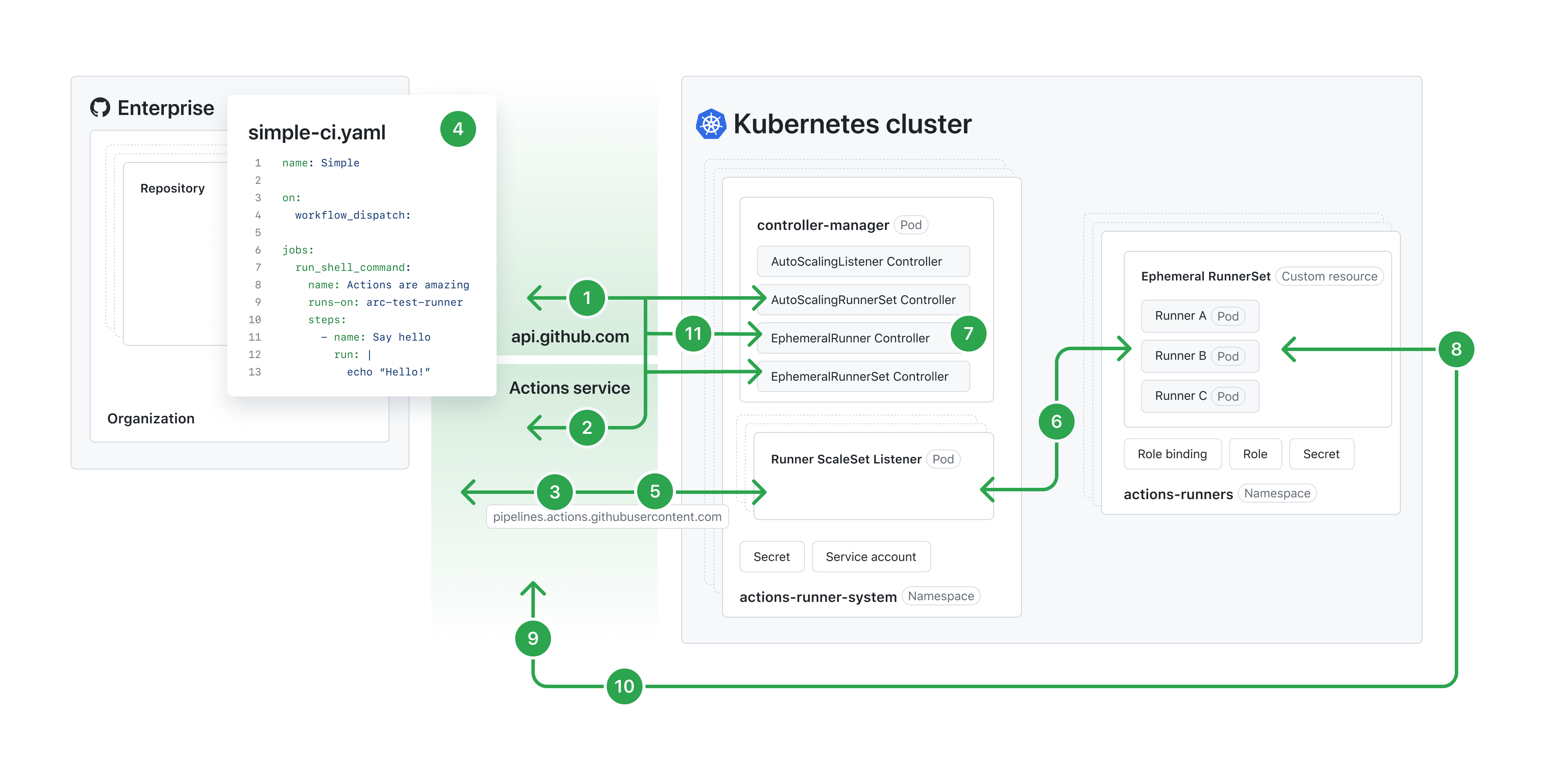
GitHub Actions launched in 2019 and basically killed the external CI/CD market overnight.
Why pay CircleCI like 130 bucks a month when GitHub gives you a few thousand free minutes? Why maintain a Jenkins cluster when you can just write YAML files that actually work?
Here's the deal: Git
Hub Actions runs your CI/CD stuff directly inside GitHub repositories.
Push code, trigger workflows, deploy to production
- all without leaving GitHub. It's not revolutionary, it's just convenient as hell.
The Reality Check
I've been debugging GitHub Actions since 2020, and here's what actually matters:
- Free tier is decent
- unlimited public repos, few thousand minutes for private ones
- YAML debugging will break your soul
- spent like 2 hours yesterday on a missing space
- **Windows costs double, mac
OS is fucking insane**
- Apple licensing means 10x pricing
- Marketplace actions are sketchy
- pin to commits or watch your deploys randomly explode
- Still better than babysitting Jenkins
- low bar but whatever
What Problems It Actually Solves
Look, I'm tired of maintaining CI servers.
GitHub Actions fixes that:
No more weekend Jenkins outages.
No more webhook bullshit between Git
Hub and CircleCI. Secrets live in your repo settings instead of some plugin that breaks every update. Open source gets unlimited builds. And uploading artifacts doesn't require configuring AWS buckets.
The Technical Reality
GitHub spins up fresh VMs for each job. Linux gets decent specs depending on whether your repo is private. Windows costs double the minutes. macOS costs 10x because Apple's licensing is ridiculous.
Jobs timeout after like 6 hours. If your build takes longer than that, you have bigger problems. The runner images get updated weekly with whatever tools are popular, so you don't maintain your own build agents like with Jenkins.
Honestly, it just works for most stuff. But here's what happens when you try to run it in production...
When to Use GitHub Actions vs Alternatives

Use GitHub Actions if:
- Your code's on GitHub anyway
- You're tired of paying CircleCI's bills
- Jenkins maintenance is killing your weekends
- You want matrix builds without the complexity
- You need dependency caching that actually works
Skip it if:
- You need complex pipeline orchestration (look at Tekton or Argo)
- Your builds need special hardware (self-hosted is possible but painful)
- You're deep in Git
Lab or Azure DevOps already
- GitHub's privacy terms don't work for your compliance
- You need advanced pipeline approvals beyond basic environments
Why This Matters
GitHub Actions didn't revolutionize CI/CD
- it just made it convenient. Instead of treating automation like separate infrastructure that needs babysitting, Actions makes it feel like part of your repo. You push code, stuff happens, you go back to building features.
The convenience has trade-offs. YAML will frustrate you. Marketplace actions will break at the worst times. Bills might surprise you if you're not careful with macOS builds. But for most teams, the productivity gains beat the headaches.
The real question isn't whether you should use GitHub Actions. It's how to use it without losing your sanity. Let's talk about what that actually looks like.