Today is Sunday, September 21, 2025. Look, I've been dealing with systemd since RHEL 7 came out in 2014, and it's... complicated. systemd is the thing that replaced the old System V init system you probably learned on, and it split the Linux community harder than vim vs emacs ever did.
Developed by Lennart Poettering and team at Red Hat, systemd took over as PID 1 on pretty much every major Linux distro. The old guard hated it because it violates the Unix philosophy of "do one thing and do it well" - systemd does fucking everything. The new guard loves it because it actually works better than the shell script mess we had before.
Instead of those sequential shell scripts in /etc/init.d/ that took forever to boot your system, systemd starts everything in parallel using dependency graphs. My server used to take 2 minutes to boot with SysV init - now it's done in 15 seconds. Of course, when something breaks, you'll be staring at dependency trees until 3am wondering why your web server won't start because some obscure dependency chain decided to take a vacation.


Core Architecture and Components
systemd isn't just one binary - it's a whole ecosystem of components that all talk to each other. Here's what you're actually dealing with:
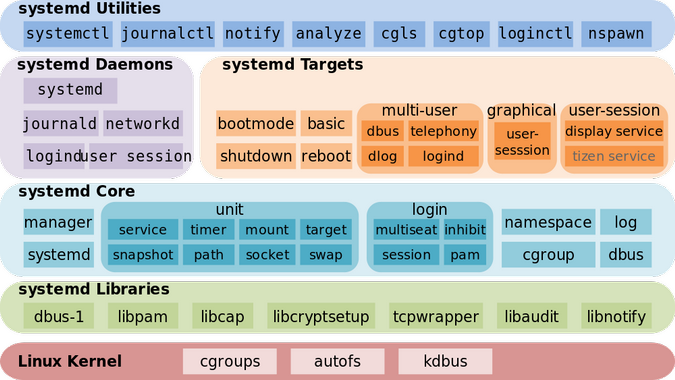
systemd-journald replaced your beloved /var/log/messages with a binary journal format that you can't just grep anymore. Yeah, I miss being able to tail log files too, but journalctl is actually better once you stop fighting it. The journal has built-in log rotation and won't fill up your disk like the old days when someone forgot to rotate auth.log.
systemd-networkd handles network configuration, and it's... fine. I still prefer NetworkManager for desktops, but networkd is solid for servers. Works with systemd-resolved for DNS resolution (which confused the hell out of me for months until I understood split DNS) and systemd-timesyncd for NTP synchronization.
The whole thing runs on D-Bus, which means when you type systemctl restart nginx, you're not actually calling a binary - you're sending a D-Bus message. This is why systemctl hangs sometimes when D-Bus gets overloaded - usually at the exact moment you need to restart a failed service in production. Fun fact: you can talk to systemd directly through D-Bus if you really want to hate yourself and have 4 hours to kill debugging why your scripts randomly stopped working after a systemd update.
Unit-Based Service Management
Instead of shell scripts, systemd uses unit files - basically INI-style config files that describe what your service does and how it relates to other services. Took me forever to understand the difference between `Wants=` and `Requires=` (hint: Wants= won't fuck up your boot if the dependency fails).
The killer feature is cgroups - each service gets its own resource container. Remember the bad old days when a runaway process could kill your whole server? systemd puts everything in cgroups, so you can set memory limits, CPU quotas, and I/O constraints right in the unit file. I've seen this save production servers more times than I can count.
Socket activation is actually pretty clever, even though it confused me for months. Instead of starting a service at boot and having it sit there eating memory, systemd creates the socket and starts the service only when someone tries to connect. This idea came from macOS, and it works great until you spend 3 hours debugging why your service won't start because the socket permissions are wrong. Ask me how I know.
Current Status and Adoption
Like it or not, systemd won the init wars. By 2025, it's everywhere - RHEL 9, Ubuntu 22.04 LTS, SUSE, even Debian finally gave up and adopted it. The only holdouts are Gentoo (which lets you choose OpenRC), Alpine Linux (still using OpenRC), and Void Linux (using runit).
systemd 258 came out just 4 days ago on September 17, 2025, and it's a big one - over 260 new features including factory-reset tooling and better credential management. The controversial bit? They're finally killing System V compatibility in version 259. Those old /etc/init.d/ scripts that still worked? Not anymore. Time to convert everything to unit files or get left behind.
The performance numbers don't lie though. Boot time analysis with systemd-analyze shows my Ubuntu server hitting multi-user mode in 8 seconds versus the 45 seconds it used to take with Upstart. Your mileage may vary, but systemd is genuinely faster.
Integration with Modern Infrastructure
The good news is systemd plays nice with modern DevOps tooling. Kubernetes uses systemd's cgroups under the hood through containerd, and cloud-init generates systemd units when you spin up EC2 instances. If you're using Ansible or Puppet, they'll create unit files for you instead of trying to manage SysV scripts.
The declarative unit files actually make Infrastructure as Code easier - you can version control your systemd configs and deploy them consistently across environments. My team keeps all our unit files in Git, and they deploy the same way whether it's dev, staging, or production. It's one of the few things about systemd that just works without surprises.