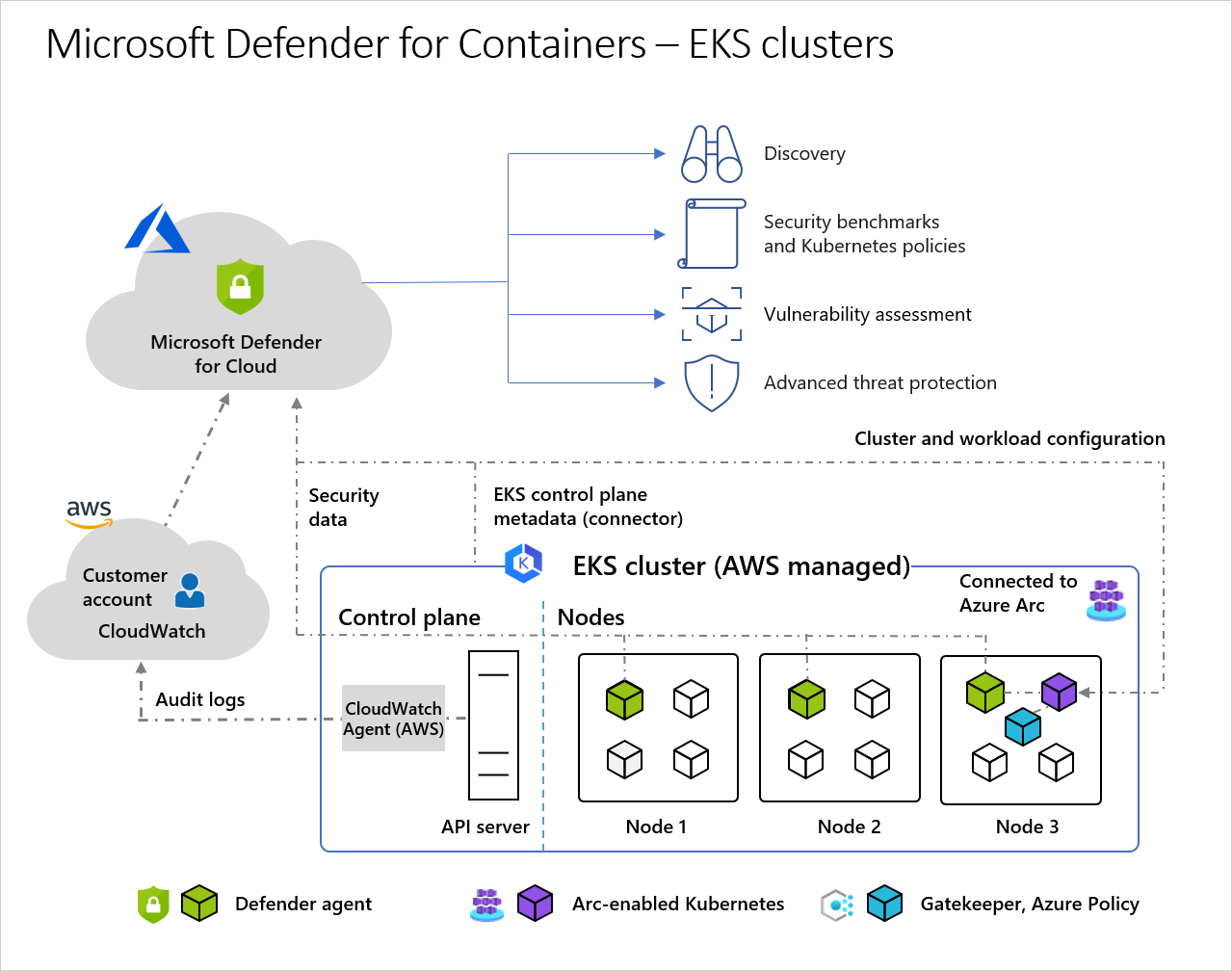
CVE-2025-9074 has a CVSS score of 9.3 - that's "game over" level. If you're on Docker Desktop older than 4.44.3 on Windows or Mac, any random container can completely own your machine.
Here's how Docker fucked this up: they exposed the Docker Engine API to all containers without any authentication. Because apparently basic security is too fucking hard. Any container could connect to the management API and create new privileged containers with full host access.

How the Vulnerability Works
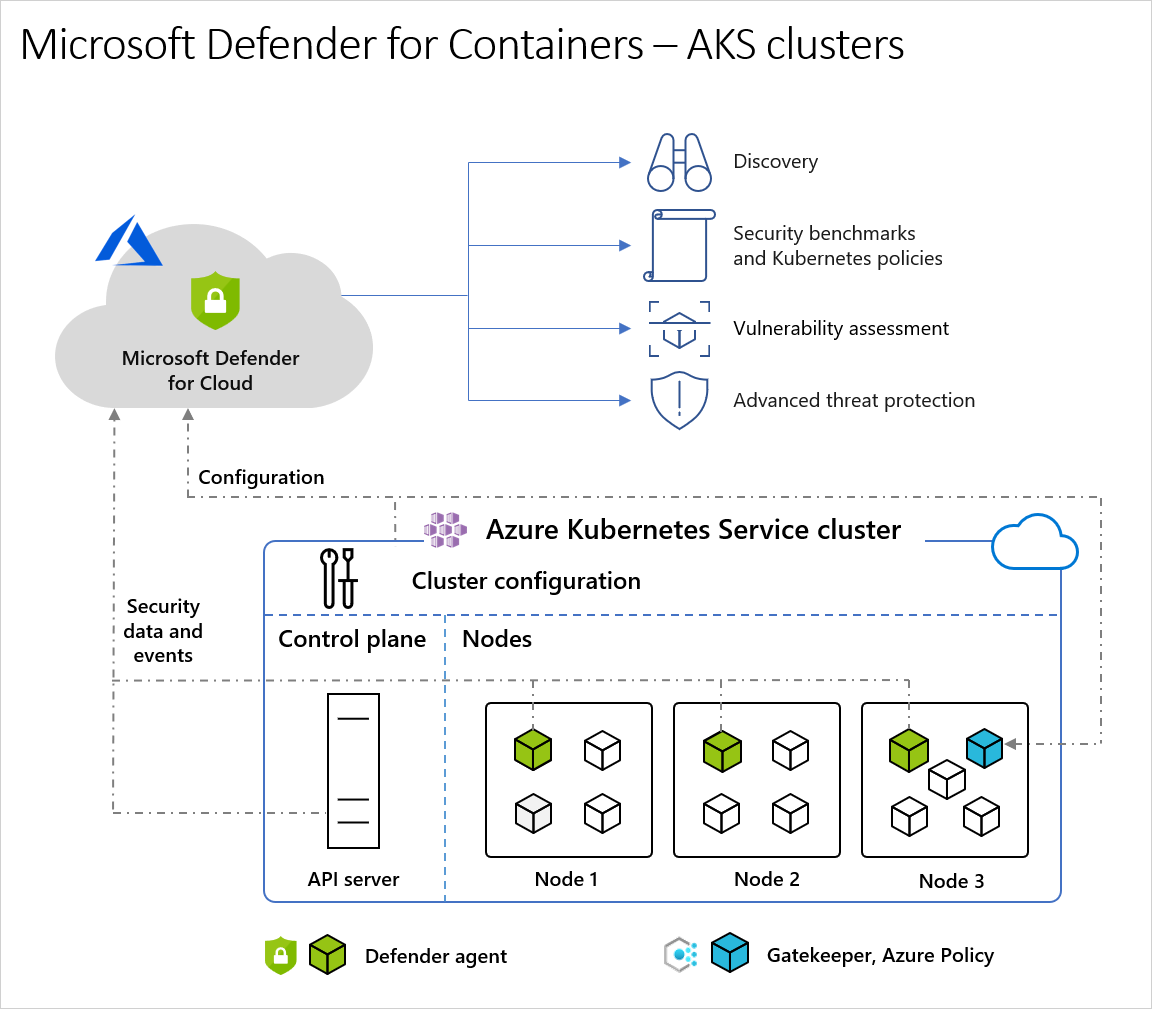
So what happened? Docker Desktop exposed their management API at 192.168.65.7:2375 without any authentication. Any shitty container could just HTTP POST to create privileged containers with your entire filesystem mounted.
Felix Boulet found this while network scanning. The API was wide fucking open - containers could make requests to 192.168.65.7:2375 and basically become root on your machine.
The exploit is stupidly simple:
- POST to create a container with host volume mounts
- POST to start it with full filesystem access
That's it. Two HTTP requests and your machine is owned. It's basically SSRF but instead of reading data, they get root access to your entire system.
Docker's "Enhanced Container Isolation" didn't do shit against this. The API exposure completely bypassed every security feature they marketed.
Impact by Platform
Windows (WSL2): You're totally fucked. Containers can mount your entire C:\ drive with admin rights, steal browser cookies, banking credentials, SSH keys - everything.
macOS: Also fucked, just with more steps. While macOS file permissions help a bit, attackers can backdoor Docker Desktop and social engineer the permission prompts that macOS users always click "Allow" on anyway.
Linux: You're fine. Linux Docker uses Unix sockets instead of TCP endpoints, so containers can't reach the management API. This is why we can't have nice things on Windows/Mac.
How Fucked You Actually Are
The exploit needs exactly:
- One POST request to create a container with host mounts
- One POST request to start it
That's it. No fancy buffer overflows or ROP chains - just two HTTP requests that any script kiddie can copy-paste from GitHub.
Even better: any web app with SSRF bugs can exploit this remotely. A compromised WordPress site can make requests to Docker's API and own your entire development machine without ever running a container directly.
This is textbook container security failure - the container runtime's own API becomes the way out of the sandbox.
Am I Totally Fucked?
Quick check:
- Docker Desktop version < 4.44.3? You're fucked
- Running on Windows or macOS? Still fucked
- Running containers from Docker Hub? Extra fucked
- Got web apps with SSRF bugs? Remotely fucked
Docker pushed the fix on August 20, 2025 in version 4.44.3. Every single Docker Desktop version before that on Windows/Mac is vulnerable.
If you haven't patched yet, drop everything and fix this. Working exploits are already public on GitHub - this isn't theoretical anymore.