Three months ago our Lambda function got compromised and traditional endpoint tools didn't even know it existed. That's when I realized we needed something built for cloud workloads, not adapted from desktop security.
SentinelOne's cloud security platform actually understands ephemeral containers and infrastructure as code. Instead of trying to jam endpoint detection into cloud environments, they built from scratch for workloads that appear, run, and disappear in minutes.
OK, rant over. Here's the technical stuff that actually matters and why this thing doesn't suck:
Two approaches: agentless scanning connects to cloud APIs for config analysis, plus agents for runtime protection when needed. Agentless scanning found hundreds of problems in our environment within like 20 minutes - no agents, no network changes, just API keys. I think it was around 350 issues or something crazy like that, maybe more. Hard to count when you're staring at that many red alerts.
Core Platform Architecture
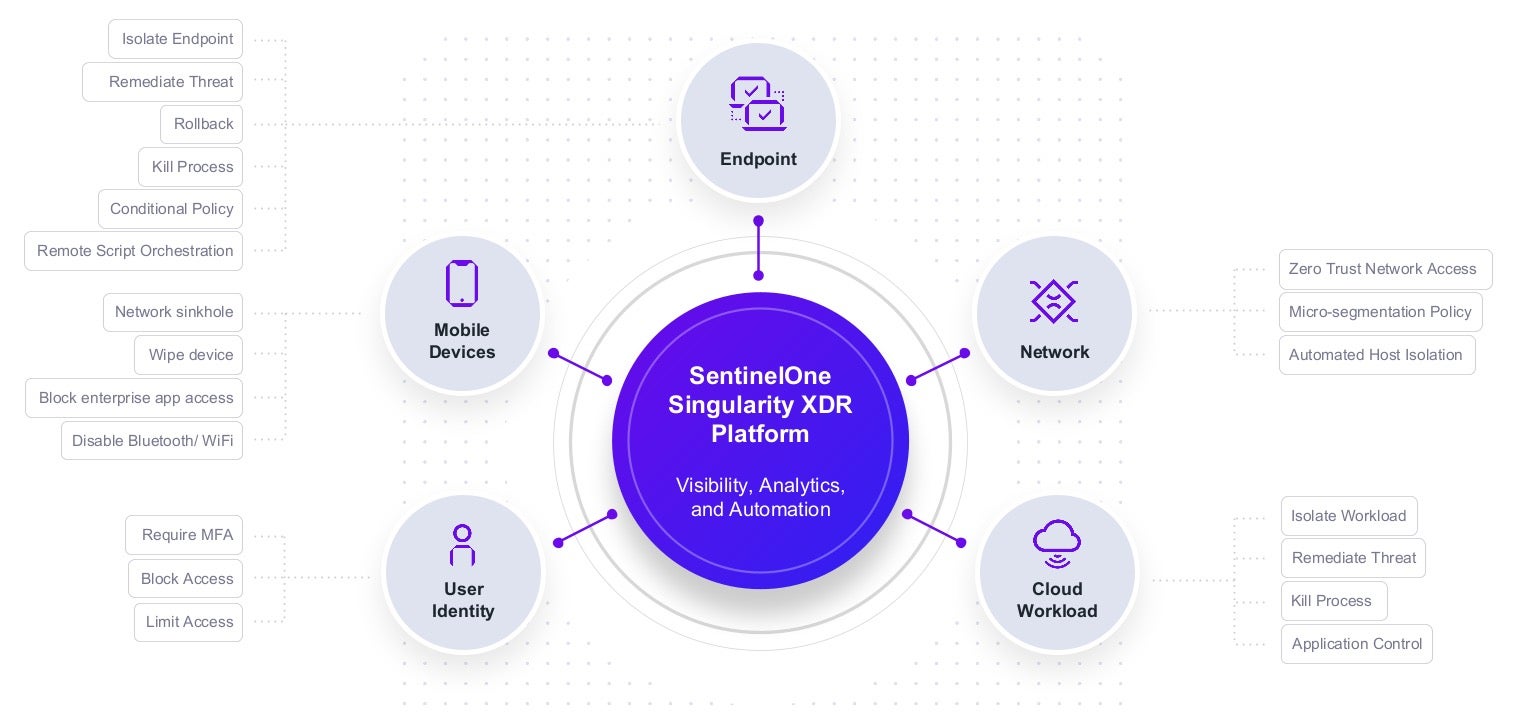
Built on their Singularity Platform data engine. Unlike vendors who stuck cloud features onto endpoint products, this was designed for cloud-scale telemetry from day one.
Setup is straightforward: give it read-only cloud provider APIs access and it discovers your entire environment - VMs, containers, Lambda functions, S3 buckets, IAM roles. Took me 15 minutes in our dev environment, but production took most of the day because cloud permissions were locked down and nobody remembered the service account passwords. The docs are garbage, so here's what actually works.
Runtime agents use eBPF on Linux (actually impressive tech) and kernel hooks on Windows. Way lighter resource usage than the security agent that was killing our production servers last year.
What It Actually Does
Configuration Scanning: Checks AWS, Azure, and GCP for the obvious problems - public S3 buckets, security groups open to 0.0.0.0/0, unencrypted databases. Has tons of checks covering CIS benchmarks. First scan was brutal - found like 400 issues, maybe more, mostly S3 buckets and IAM roles from dead projects that nobody bothered cleaning up. Just sitting there with admin access from that contractor who left in 2021.
Runtime Protection: Uses behavioral analysis instead of signatures to catch weird process execution and network patterns. When we had a cryptominer spin up in a container last month, it detected the abnormal CPU usage and killed the process within 30 seconds. Users rate it 4.4/5 which is pretty good for security software.
Incident Response: Remote investigation without SSH access to production. When our staging environment got compromised, I could collect forensics, isolate processes, and block network connections from the console instead of logging into individual servers. Works well for containers that might disappear before you finish investigating.
Permission Analysis: Maps cloud IAM to find risky permissions - service accounts with admin access, users inactive for months with database permissions, Lambda functions that can delete entire S3 buckets. Found a contractor's account that still had production access 8 months after they left.
AI That Actually Works
Most security vendors slap "AI-powered" on signature-based tools and call it innovation. SentinelOne feeds threat intelligence and endpoint data into models that learn your environment's normal patterns - which processes run in your containers, typical network behavior, usual service interactions.
When a container starts mining crypto or a Lambda function makes weird API calls, it flags the deviation. Not revolutionary, but better than managing signature databases.
Purple AI: Natural language queries for investigations. Ask "show me containers with critical CVEs that have internet access" instead of writing complex filters. Useful when you're debugging at 3am and can't remember query syntax. Works better than expected.
Attack Path Mapping
Instead of dumping 5,000 "critical" vulnerabilities that nobody has time to fix, it maps realistic attack paths through your infrastructure.
Connects vulnerabilities, misconfigurations, and network access to show how attackers chain exploits: "Internet-facing container with CVE-2024-1234 → lateral movement through overprivileged service account → access to production database."
Way better than arguing about CVSS scores. Shows what actually leads to data exfiltration instead of theoretical vulnerability ratings. Helped us prioritize fixing 12 real problems instead of 400 low-impact issues.
DevSecOps Integration
Scans Terraform, Dockerfiles, and Kubernetes manifests in CI/CD pipelines. Integrates with Jenkins, GitLab, GitHub Actions, Azure DevOps without breaking existing workflows.
When it finds issues, can fail builds or create tickets. We had it catch a hardcoded database password in a merge request last week - way easier to fix there than in production. Developers initially complained about build failures, but they prefer that to getting paged at 2am about data breaches.
"Shift-left" is mostly buzzword bullshit, but preventing problems in CI/CD beats fixing them in production. Nobody wants to get paged at 2am about hardcoded passwords while debugging why the database is on fire.
Multi-Cloud Reality
Works across AWS, Azure, and GCP because every company accidentally becomes multi-cloud. Data team uses GCP for BigQuery, developers prefer AWS Lambda, infrastructure runs Azure because of some contract from 2019.
Single console instead of juggling three different security tools. Cross-cloud threat correlation works - can track attacks that start in AWS, compromise Azure service accounts, and access GCP data. Native cloud tools can't do this.
Problem is, it's useless if it doesn't play nice with your existing tools.
Enterprise Integration
REST API with decent documentation and reasonable rate limits. Better than vendors who give you SOAP APIs from 2005.
SIEM Integration: Pushes events to Splunk, QRadar, ArcSight, Microsoft Sentinel in CEF/LEEF format. No custom parsers needed. Configure event filters first - our first day generated something like 47,000 "S3 bucket misconfigured" alerts that maxed out our Splunk license and cost us an extra $12K that month. Turned out every single dev environment bucket was flagged as a critical finding.
Ticketing: Auto-creates ServiceNow, Jira, PagerDuty tickets for issues. Created thousands of tickets on day one before we tuned severity thresholds. I think it was around 1,800? Infrastructure team was pissed. "Why is every S3 bucket a P1 incident?" was the exact Slack message I got, followed by several emoji that HR wouldn't approve of.
