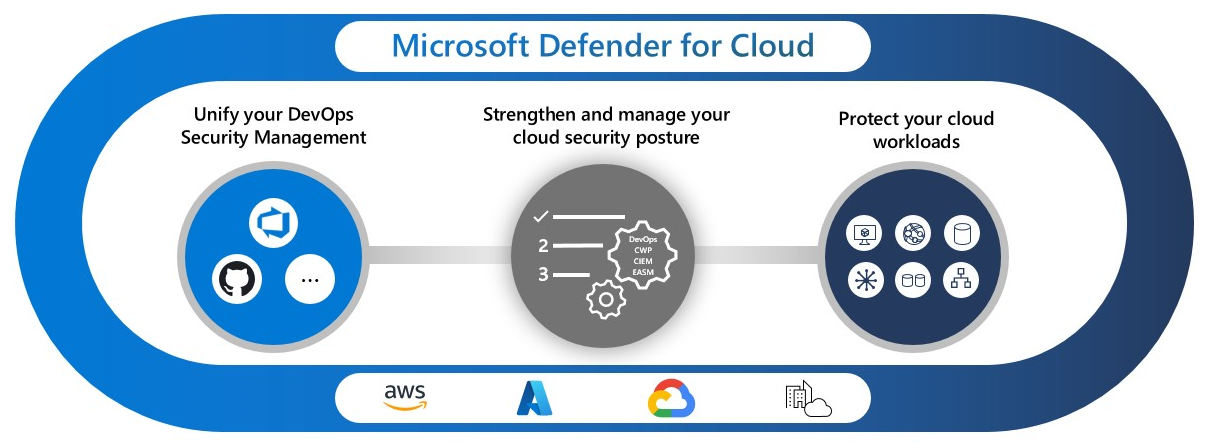
Microsoft Defender for Cloud is what Azure Security Center became when Microsoft decided they needed a fancy acronym to compete with Palo Alto and Wiz. It's a Cloud Native Application Protection Platform (CNAPP) that covers three main areas - and here's what you need to know if you're actually going to deploy this thing in production.
The Reality of Multi-Cloud Deployment
Here's the reality: the Azure integration works great. AWS integration? It's functional, but feels like it was built by a team that's never actually used AWS. The multi-cloud setup takes way longer than the "15-30 minutes" Microsoft claims. Plan on 2-3 hours for AWS if you want to do it right, and that's assuming your IAM policies don't fight you.
The GCP integration is... there. It exists. I've seen it work. But if you're heavily invested in Google Cloud security tooling, you're probably better off sticking with what you have.
Real deployment pain points I've hit:
- AWS connector fails every few weeks and requires manual intervention
- Multi-cloud policy sync is slower than molasses - expect 4-6 hour delays
- The "agentless" scanning sometimes just... stops working on random VMs
DevSecOps Integration: Better Than Expected
The DevOps security features are actually pretty solid. GitHub integration works well, Azure DevOps is seamless (shocking, I know), and even GitLab plays nice. The Infrastructure as Code (IaC) scanning catches the obvious stuff - misconfigured S3 buckets, overly permissive security groups, hardcoded secrets.
But here's the thing: it flags legitimate admin activity as suspicious about 30% of the time. Your PowerShell scripts will trigger alerts. Your automated deployments will trigger alerts. You'll spend the first month tuning it to not spam your SOC.
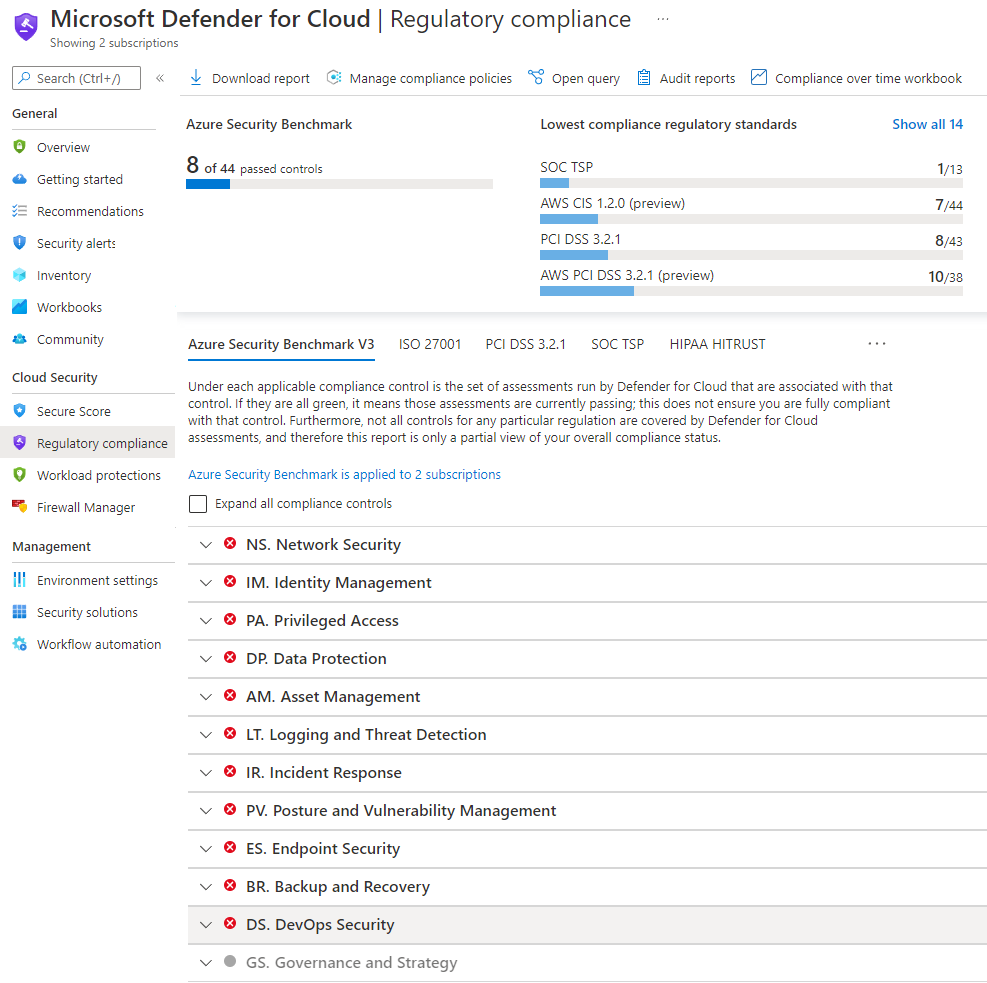
CSPM: Free Tier is Actually Useful
The foundational CSPM features are actually free and don't suck - which shocked the hell out of me given Microsoft's usual nickel-and-dime approach. You get basic posture assessment, compliance dashboards, and security recommendations without paying a dime.
The paid CSPM features like attack path analysis and the Cloud Security Explorer are useful if you're managing complex environments, but the learning curve is steep and the interface feels like it was designed by someone who's never actually investigated a security incident.


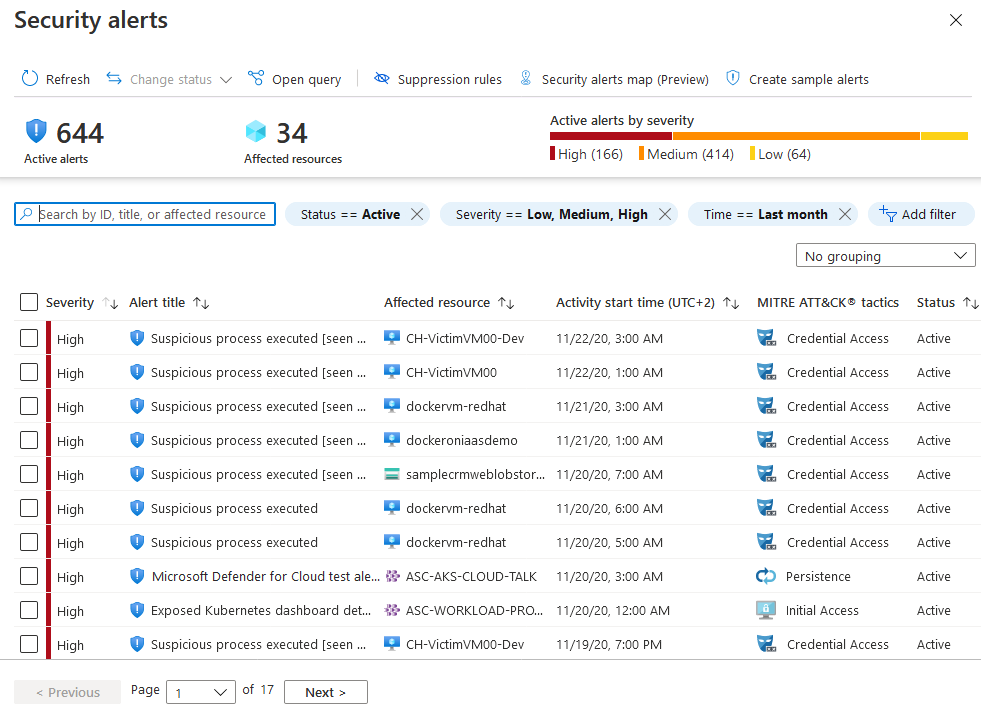
Workload Protection: Works If You Tune It
The threat detection is powered by Microsoft's threat intelligence, which is actually pretty good. But out of the box, it's noisy as hell. You'll get alerts for everything - legitimate maintenance scripts, normal admin activity, automated backups.
What actually works well:
- Container security for AKS clusters
- SQL injection detection (when it's not crying wolf)
- Malware detection on storage accounts
- Integration with Microsoft Defender for Endpoint
What needs work:
- Too many false positives on "behavioral analytics"
- Performance impact on production workloads is higher than advertised
- Alert fatigue is real - you'll spend weeks tuning thresholds (or just disable alerts entirely like I've seen some teams do)
The integration with Microsoft Sentinel and Microsoft Entra works seamlessly, which makes sense since it's all Microsoft. But if you're using third-party SIEM tools like Splunk, prepare for pain - you'll spend days writing custom parsers and questioning your life choices.