The MSI vs Admin Console Reality Check
Most enterprise deployments fail because teams try to do everything through Group Policy and MSI installers. The old admin-settings.json approach works, but it's a pain in the ass to maintain. You're editing JSON files, redistributing them through MDM, and debugging policy conflicts when developers have local overrides.
The new Settings Management through Admin Console actually changes the game for once. Policies are cloud-based, you get real-time compliance reporting, and there's no more JSON file distribution nightmare that made me question my career choices.

But here's the catch: you still need the MSI/PKG installer to get Docker Desktop on machines initially. The Admin Console only manages settings after Docker Desktop is installed and developers are signed in.
Multi-Organization Rollout Strategy That Doesn't Suck
Large enterprises often have multiple business units that need different registry allowlists. The Company administration feature lets you manage multiple organizations under one umbrella.
Create separate organizations for different teams:
company-platform-team- Gets access to internal artifact registriescompany-frontend-team- Needs different registries for npm packages converted to containerscompany-security-team- Minimal registries, maximum restrictions
Use organization access tokens for automation instead of sharing service account credentials across teams.
The 48-Hour Rollout Schedule (Or How to Not Ruin Everyone's Week)
Don't deploy RAM organization-wide on a Monday morning. Seriously. Just fucking don't. I've seen deployments that blocked entire engineering teams because someone forgot to allowlist the internal registry used by CI/CD. Last time we did this, 200+ developers couldn't build anything for 4 hours while we frantically added registry.internal.company.com and all its goddamn mirror domains. I think I aged 5 years that day.
Phase 1 (Week 1): Pilot Testing
- Deploy to 10-15 volunteer developers across platforms
- Include at least one person from each major product team
- Enable comprehensive allowlists - better to be too permissive initially
- Monitor the Settings Reporting dashboard for compliance issues
Phase 2 (Week 2): Controlled Expansion
- Expand to 50-100 developers
- Tighten allowlists based on audit logs from Phase 1
- Test Group Policy deployment for Windows environments
- Verify Jamf Pro integration works with your existing MDM
Phase 3 (Week 3+): Full Rollout
- Deploy to remaining developers in batches of 100-200
- Have support staff ready for the inevitable "why can't I pull this image" tickets
- Prepare communication explaining what changed and how to request new registries
Settings Management Performance at Scale
The new cloud-based Settings Management actually scales much better than the old admin-settings.json approach that made everyone's life miserable. We've tested deployments with 2000+ developers and policy propagation stayed under 6 hours.
Key metrics from large deployments:
- Policy creation: Instant in Admin Console vs 2-4 hours for JSON file distribution
- Compliance reporting: Real-time vs manual auditing with JSON files
- Policy updates: 2-6 hours propagation vs full MDM redistribution cycle
- Developer impact: Settings locked in UI vs confusing JSON override behaviors
Platform-Specific Deployment Gotchas at Scale
Windows + Active Directory Integration: The MSI installer works great with Group Policy, but RAM policies don't integrate with existing AD group memberships. You'll manage Docker policies separately in the Admin Console.
macOS + Jamf Pro: [PKG installer deployment](https://docs.docker.com/enterprise/enterprise-deployment/use-jamf-pro/) handles the Docker Desktop installation, but you still need developers to sign in manually for RAM to work. Plan for support tickets from developers who forget to authenticate. So many fucking tickets. I spent 3 weeks tracking down why macOS devs had inconsistent registry access - turns out half of them never signed into Docker Desktop after the Jamf install.
Mixed Platform Environments: Policy precedence can get weird when you have developers switching between company laptops and personal machines. The Admin Console policies always win over local JSON files, which helps maintain consistency.
CI/CD Integration Nightmare Prevention
The biggest enterprise deployment failure is forgetting about CI/CD systems. Your build agents need Docker too, and RAM will block them from pulling images unless you plan ahead. Learned this when our Jenkins agents started throwing registry access denied errors at 3am, failing every build until I could figure out why our automation wasn't authenticated properly.
Service accounts for build systems need (and this is where it gets expensive):
- Docker Business licenses (they count against your seat count)
- Separate organization or team membership for automated systems
- Broader registry allowlists since CI/CD often pulls from more registries than developers
Use organization access tokens instead of sharing individual developer credentials with CI systems. Much easier to rotate and audit.
Monitoring and Compliance at Enterprise Scale
The Settings Reporting dashboard literally saves your ass when security audits come around. Thank fuck for this feature. Download compliance reports as CSV files for evidence that your registry access controls are actually working.
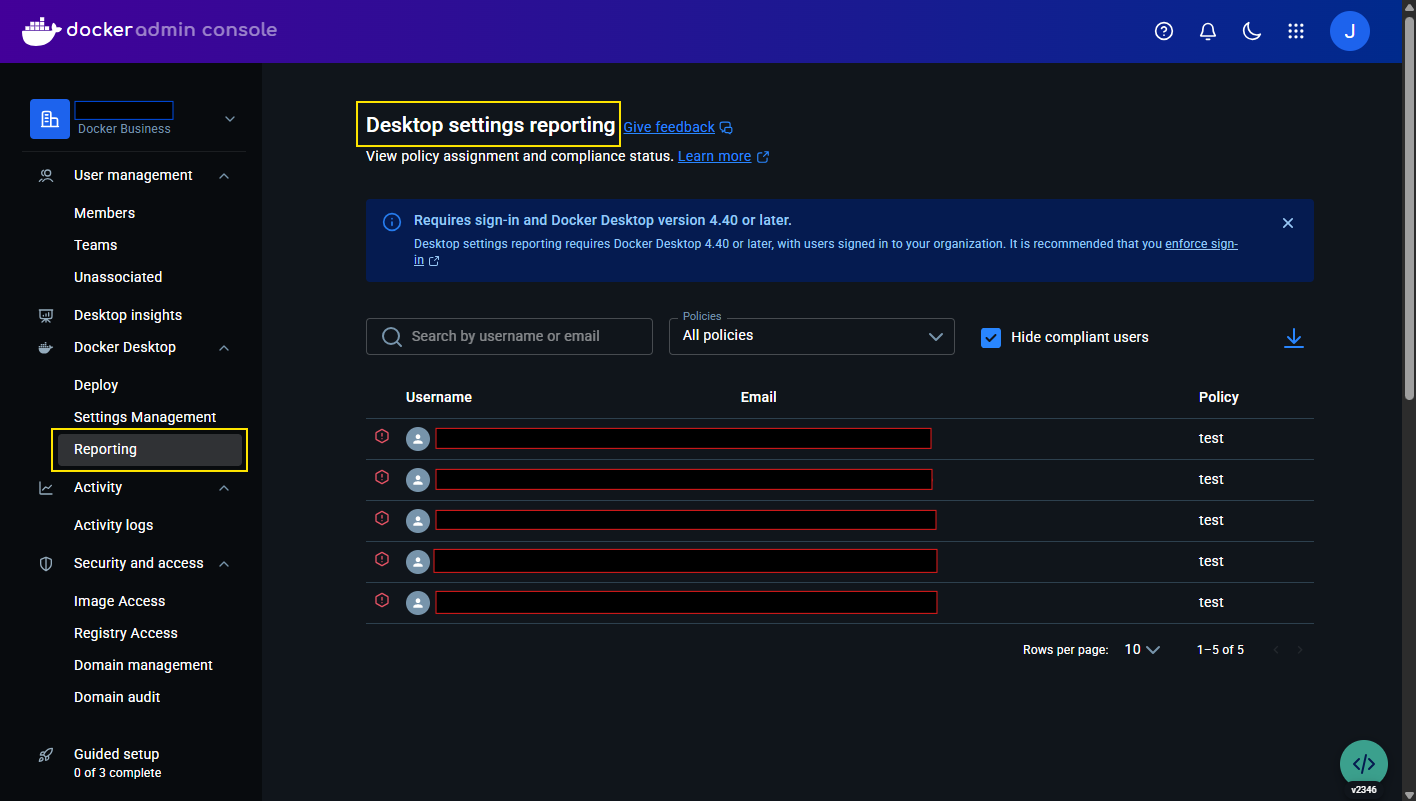
Set up monitoring for:
- Non-compliant developers (usually means they're signed out or using personal accounts)
- Policy propagation delays (anything over 8 hours indicates a problem)
- Registry allowlist violations (developers requesting access to new registries)
- Build system failures (CI/CD agents getting blocked by RAM restrictions)
Integration with existing security tooling like Sysdig or SIEM systems helps correlate Docker security events with broader security monitoring.
