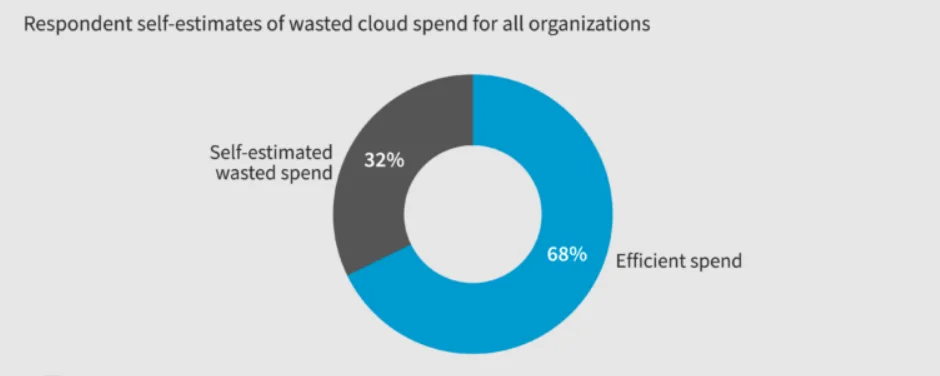
Every Prisma Cloud pitch starts the same bullshit way: sales demo in a lab with like 20 resources, everything works perfectly, costs look reasonable. Fast forward six months and you're explaining to your CFO why the security budget is hemorrhaging money and AWS is charging you for services you've never heard of.
I've deployed this thing at three different companies. It always goes the same way. Community discussions about cloud security cost management are everywhere. Stack Overflow questions about cost overruns are everywhere. Here's what actually happens when Prisma hits production.
Credits Burn Like Crazy (Sales Won't Tell You This)
Prisma's credit pricing sounds simple. Business Edition is 9k for 100 credits, Enterprise is 18k. Sounds reasonable until your AWS environment starts eating 400-500 credits a month and you realize you're fucked.
What Actually Happens:
- Dev scanning: burns credits like crazy - way more than you'd think
- Production: easily 300+ credits monthly if you have actual workloads
- Container scanning during builds: unlimited burn (this will fucking kill you)
- Compliance stuff: spikes during audits - I've seen 150+ credit months
- Agentless scanning: another massive chunk if you're not careful
That 18k Enterprise price? Yeah right. Budget for 60-120k annually just for credits, probably more if your CI/CD doesn't suck. Plus all the other AWS charges they don't mention. AWS forums are full of people getting surprised by this, and industry reports confirm what everyone already knows - security tools fuck your budget harder than anything else.
AWS Bills Start Looking Insane
Here's where Prisma really fucks you. It's not just the licensing. It starts eating your AWS resources like crazy.
Defenders Eat Memory Like Hungry Monsters: Defender agents eat like 200-300MB per container when scanning. Sounds small until you have 500 containers and suddenly need 100+ GB more RAM. At AWS EC2 pricing that's like 3k extra per month minimum, maybe way more. GitHub issues document this memory hell constantly.
Data Transfer Gets Brutal: Prisma streams telemetry constantly. Multi-cloud setup? You're gonna get fucked on egress fees. I've seen 15-25k monthly charges just for streaming security events between regions. Azure bandwidth costs are even worse. Data transfer optimization requires architectural changes you probably don't want to make.
Storage Costs Explode: Two-year retention sounds fine until you hit like 30TB of logs. Had one client paying around 6k monthly - maybe more - for RDS storage of compliance data that basically never gets looked at. Use S3 tiering or you'll hate your life.
Scanning Instances Don't Die: Agentless scanning spins up EC2 instances that sometimes don't terminate. Last deployment I did had like 40+ scanning instances running for weeks because cleanup failed. Cost the client something like 12k in surprise charges. AWS cost alerts are mandatory or this will bite you.
Your Budget Estimates Are Guaranteed to Be Wrong
Sales demos in clean labs with like 30 resources where everything talks to everything perfectly. Real production has thousands of resources across dozens of AWS accounts with networking that makes you want to quit engineering.
Everything Gets Scanned (Surprise!): That "one application"? It's actually an EC2 instance, plus containers, plus the repo, plus Terraform configs. Each gets scanned separately. What you thought was one workload burns 30-40 credits monthly minimum.
Multi-Account Hell: Got 50+ AWS accounts? Each needs separate Prisma setup. IAM roles, logging, monitoring, all duplicated. AWS multi-account setup is already painful, Prisma makes it worse. Every account becomes its own cost center. Automation samples help but don't fix the cost multiplication.
Global Deployments Triple Everything: US, EU, APAC? Data residency requirements mean separate Prisma instances for each region. Your licensing costs just tripled and you get cross-region networking fees for reporting. Fun times.
The Cortex Cloud Upgrade Nobody Asked For
They rebranded Prisma to Cortex Cloud with "enhanced AI" that basically means your credits burn faster. The AI prioritization sounds cool but processes way more data. Translation: your bills are about to get worse. Forrester's study conveniently ignores the cost increases because of course it does.
What This Means for Your Budget:
- AI processing burns more credits (they won't tell you how many more)
- Real-time detection generates 3x more alerts to process
- "Cases" feature correlates everything, eating more compute
- XDR integration adds another data ingestion bill
Damage Control: Existing customers get a few months grace period. Use this time to see how bad the credit burn gets and renegotiate before renewal. Those shiny new features will probably double your costs.
You Will Pay for Consultants Whether You Want To or Not
Prisma is too complex to deploy without expensive help. I've never seen a successful DIY deployment at enterprise scale.
Initial Deployment Hell: Budget 150-250k for consultants minimum. Multi-cloud IAM is a nightmare, policy tuning takes forever, SIEM integration breaks constantly. Palo Alto consulting is 400-500/hour but it's that or spend 8 months debugging IAM roles across 47 AWS accounts. Terraform providers exist but still need expert help because this shit is complicated.
Policy Management Never Ends: Custom compliance needs their weird query language. Clients spend 75-125k annually on consultants just to maintain policies. Audit season? Double that. Good luck hiring internally - nobody knows this stuff.
Every Update Breaks Something: Each Prisma release potentially fucks your custom integrations. Budget 50k+ annually for consultant firefighting during updates. Multi-cloud monitoring doesn't help when nothing talks to anything anymore after an update.
The alternative is 18+ month deployments and engineers quitting from multi-cloud IAM hell. Trust me, pay for the consultants.
Regional and Compliance Multipliers That Will Wreck You
GDPR in Europe Sucks: Data residency means separate EU Prisma instances that can't share threat intel properly. Costs are 50%+ higher than US deployments. GDPR requirements add legal costs and audit bullshit. Data sovereignty is expensive as hell.
Financial Services Are Fucked: Banks need air-gapped deployments, dedicated everything, extra security theater. Budget 3x standard pricing minimum. SOX compliance adds quarterly reporting hell that drives costs even higher.
Healthcare HIPAA Hell: Need BAAs, encryption everywhere, audit trails for everything. Infrastructure costs double easy, plus dedicated compliance consultants. HIPAA violations can cost millions so you're trapped paying whatever they ask.
Don't avoid Prisma. Just know you're walking into a cost explosion and budget accordingly. At least then you won't get fired when the bills arrive.