
AWS Edge Services are Amazon's answer to the latency problem. You know the drill - users complaining about slow apps, especially those poor bastards not in US-East-1. So AWS scattered computing power across the globe to get closer to users. Does it work? Yeah, mostly. Will it solve all your problems? Hell no.
The Reality of 700+ Edge Locations
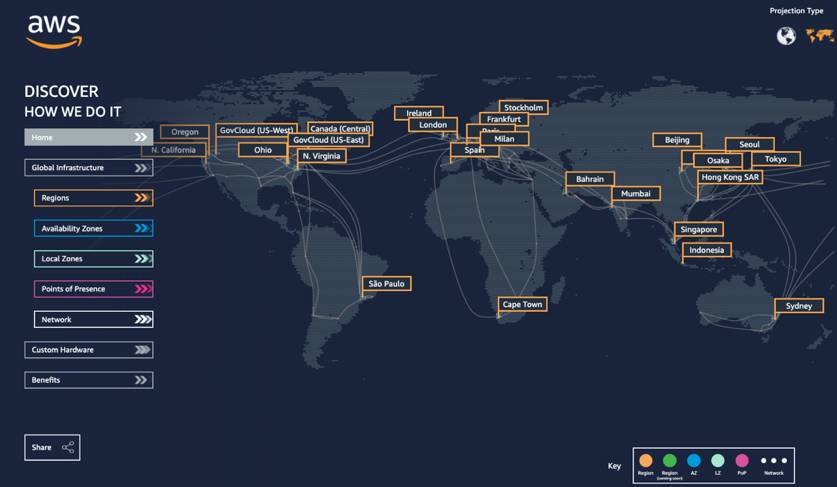
AWS loves to brag about their 700+ CloudFront Points of Presence with 13 Regional edge caches. Sounds impressive until you realize half of them are in places your users aren't, and the ones that matter are overloaded during peak hours. Black Friday last year, CloudFront basically died in US-East. Response times went to hell - like 800ms instead of the usual 50-100ms. Had to failover to Cloudflare for hours.
You can check AWS's real-time edge location status but they don't publish performance metrics. Compare that to Cloudflare's transparency reports where they actually show you which locations are performing well.
CloudFront: The Good and The Ugly
CloudFront is AWS's CDN. When it works, it's great - I've seen page load times drop from 2 seconds to 200ms. But here's what they don't tell you:
- Cache invalidations cost $0.005 per path. Sounds cheap? I've seen monthly bills spike 300% because someone invalidated
/assets/*instead of specific files. - Cache misses destroy performance. Your "edge-optimized" site becomes slower than if you just served from S3.
- Asia-Pacific pricing will destroy your budget. We serve a lot of users in Singapore - went from $200/month to $900/month just by expanding there. Same traffic, 4.5x the cost.
For reference, check out AWS's CDN performance comparison and third-party CDN benchmarks to see how CloudFront stacks up. Fastly and KeyCDN often outperform CloudFront in specific regions.
Lambda@Edge: Powerful but Painful

Lambda@Edge lets you run code at CloudFront locations. Cool idea, brutal execution. 15-minute deployment times mean you'll be waiting around like it's 2010. And debugging? Good fucking luck. Error logs are scattered across regions, and half the time you can't tell which edge location failed.
Real talk: If you need sub-second cold starts, use Cloudflare Workers. Their V8 isolates start instantly while Lambda@Edge takes 2+ seconds on cold start. Vercel Edge Functions and Netlify Edge Functions are also faster alternatives.
For detailed Lambda@Edge limitations, check the AWS documentation and this comprehensive performance analysis.
The Services That Actually Matter
CloudFront - The main CDN. Use it, but understand the pricing gotchas.
Lambda@Edge - Serverless at the edge. Powerful but slow to deploy.
AWS Outposts - AWS hardware in your datacenter. Expensive as hell but works if you need hybrid cloud. Pricing starts at $200k+ upfront.
Local Zones - AWS regions in metro areas. Good for latency-sensitive apps in supported cities. Currently available in 32+ metro areas.
Wavelength - 5G edge computing. Only works in specific carrier networks like Verizon and KDDI. Limited availability and expensive.
Skip the IoT edge stuff unless you're actually doing IoT. SageMaker Edge Manager sounds cool but it's overkill for most web apps. For IoT specifically, check out AWS IoT Greengrass instead.
Marketing promises versus production reality? That's where the real fun starts.



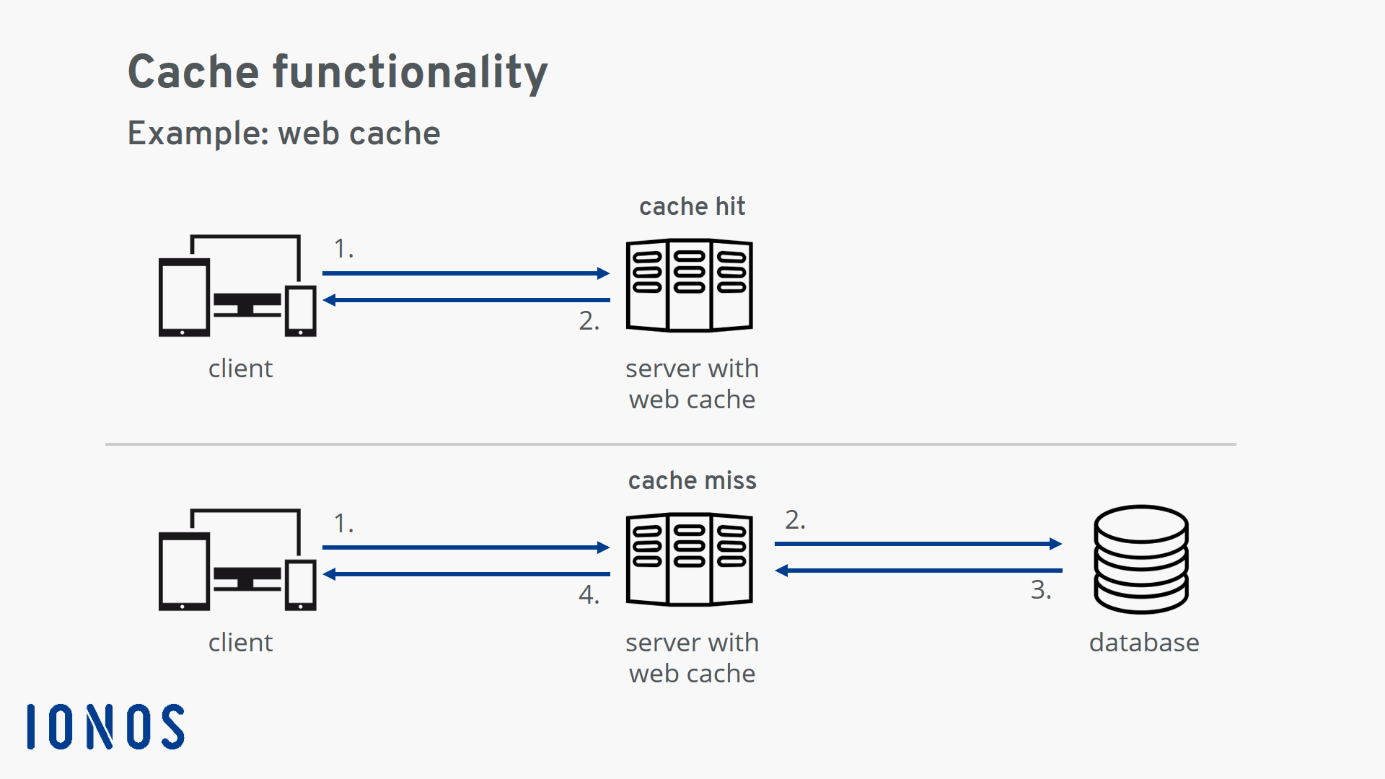 Cache misses are killing you.
Cache misses are killing you.