HashiCorp fucking betrayed the community in August 2023 with their Business Source License bullshit. But honestly? The license change just gave everyone permission to admit what they already knew - Terraform sucks in production.

HashiCorp's BSL License: Corporate Greed Disguised as Protection
HashiCorp's license change from MPL 2.0 to BSL wasn't about protecting innovation - it was about killing competitors like Spacelift and env0 who were eating their lunch. They saw Terraform Cloud's pathetic adoption rates and decided to lawyer their way out of competition instead of building better software.
The BSL is poison for any serious engineering organization. You can't use it commercially to compete with HashiCorp, which means every startup using Terraform is one pivot away from a legal clusterfuck.
The community told HashiCorp to go fuck themselves. Within weeks, the OpenTofu initiative launched as a fork of Terraform 1.5.6 - the last version before HashiCorp lost their minds. I think over 100 companies pledged support, but honestly who's counting - everyone was already planning their exit strategy anyway.
The Technical Reality: Terraform Was Always Broken
The license change just gave everyone permission to say what they'd been thinking: Terraform's technical foundation is garbage.
HCL is a Programming Language for People Who Hate Programming: HCL's syntax makes YAML look elegant. Community discussions are full of engineers complaining about for_each syntax gymnastics and HCL's general limitations. Need error handling? Hope you like cryptic Error: error occurred messages that tell you absolutely nothing. Complex infrastructure in HCL becomes an unmaintainable nightmare of nested conditionals and string interpolation that would make a PHP developer cringe.
HCP Terraform's Pricing is Designed to Fuck You: Their Resources Under Management model is predatory as hell. They charge $0.00014 per resource per hour. Do the math - that's over a grand monthly for around 10,000 resources, maybe more. I've seen companies with like eight grand AWS bills pay something crazy like fifteen or maybe eighteen thousand a month to HCP Terraform. One CTO literally asked me why they're paying HashiCorp more than Amazon. The math makes no fucking sense.
Worse yet, they count everything as a "resource" - including data sources that just read information. So your terraform state with like 4,800 actual resources becomes something insane like 14,500 billable "resources" overnight. Cloud billing discussions document similar predatory pricing from other vendors, but HCP Terraform takes it to a whole new level.
Terraform's "Testing" is a Joke: Good luck unit testing HCL. The best you get is terraform plan which tells you nothing about whether your infrastructure will actually work. No debugger, no real IDE support (VSCode highlighting doesn't count), no proper testing framework. You're essentially deploying untested code to production and hoping for the best. State corruption happens regularly, and when it does, you're debugging with terraform show and prayer.
Why Smart Teams Are Jumping Ship
Real engineers are ditching Terraform faster than you can say "state drift":
- Atlassian Bitbucket: Migrated from Terraform to Pulumi in 2 days using conversion tools. What they don't tell you: it took 3 weeks to fix all the edge cases, but it was still worth it.
- Every startup I know: Chose OpenTofu over Terraform Cloud because they're not idiots who want to pay more for state storage than actual infrastructure.
- Enterprise teams: Moving to programming languages because explaining HCL syntax to senior developers is embarrassing. Pulumi vs Terraform comparisons consistently show developers prefer actual programming languages over DSL hell.
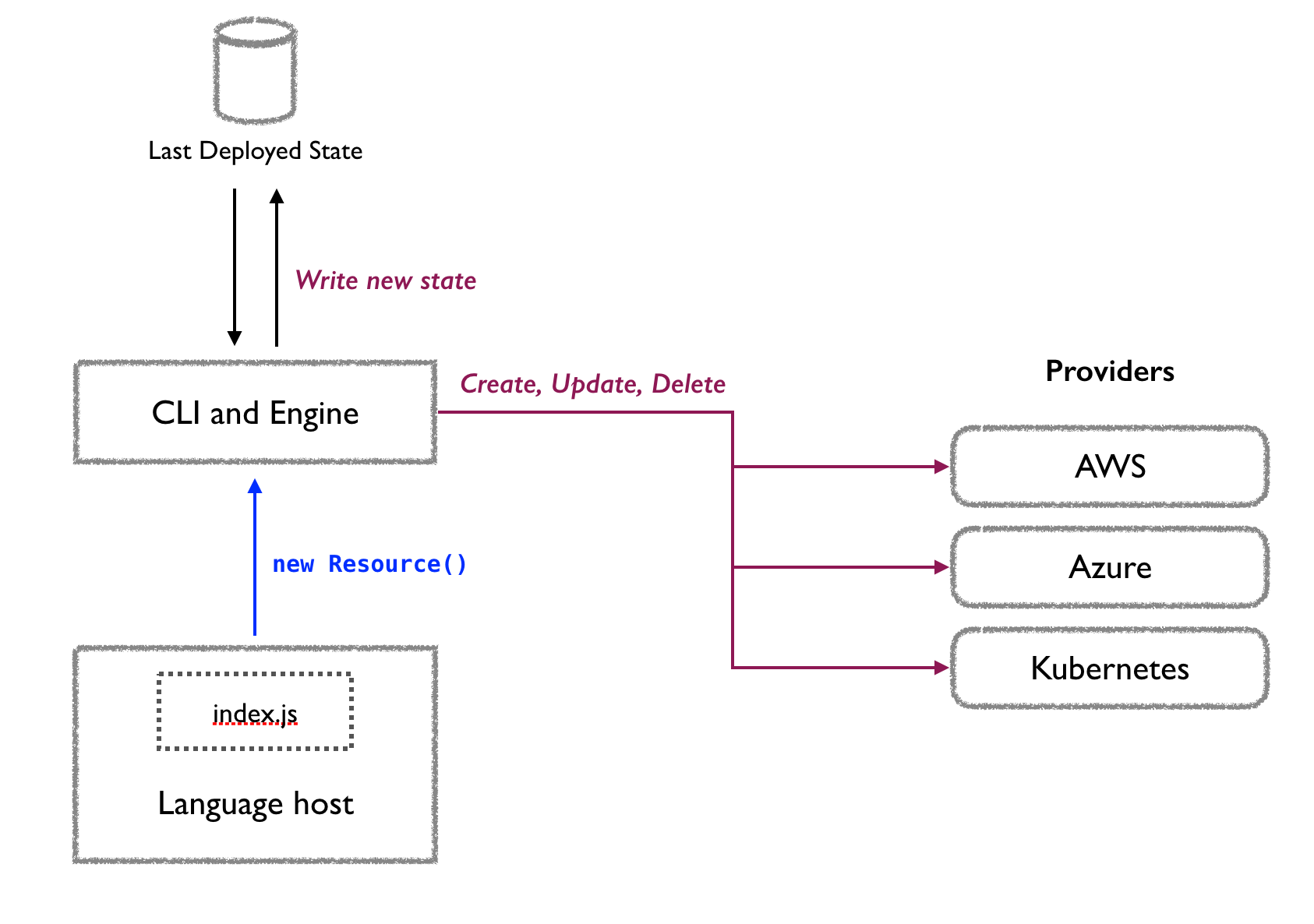
What Engineers Actually Need (Not HashiCorp's Vision)
Look, rant aside, here's the technical reality. After debugging Terraform at 3am for the hundredth time, here's what actually matters:
- State management that doesn't randomly break (like Terraform's backward compatibility issues)
- Error messages that aren't written by sadists
- Costs you can predict without a PhD in HashiCorp pricing
- Real programming languages with actual testing frameworks
- Not paying a vendor protection racket for basic features
- Community governance that doesn't pull rug changes
Anyway, back to the technical bullshit - the alternatives aren't perfect, but they're better than dealing with HashiCorp's vendor lock-in. OpenTofu is literally the same tool with better politics. Pulumi lets you write actual code. Cloud-native tools just work without the complexity theater.
Pick based on what your team can actually handle, not what sounds good in architecture reviews.