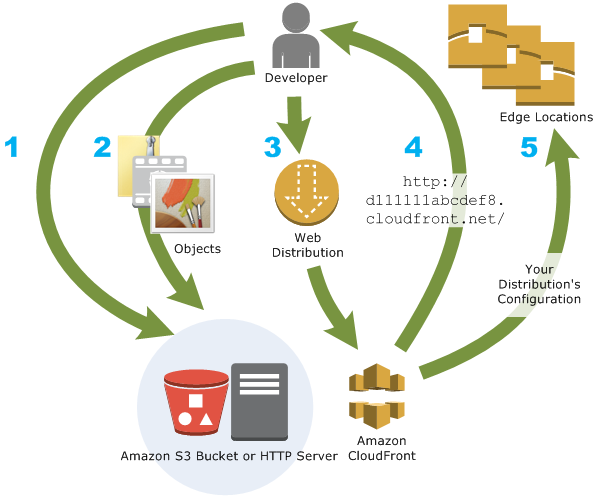
CloudFront is AWS's CDN that's been around since 2008. It works like any other CDN - caches your content closer to users so they don't have to reach back to your origin server every time. Sounds simple, right? It's not.
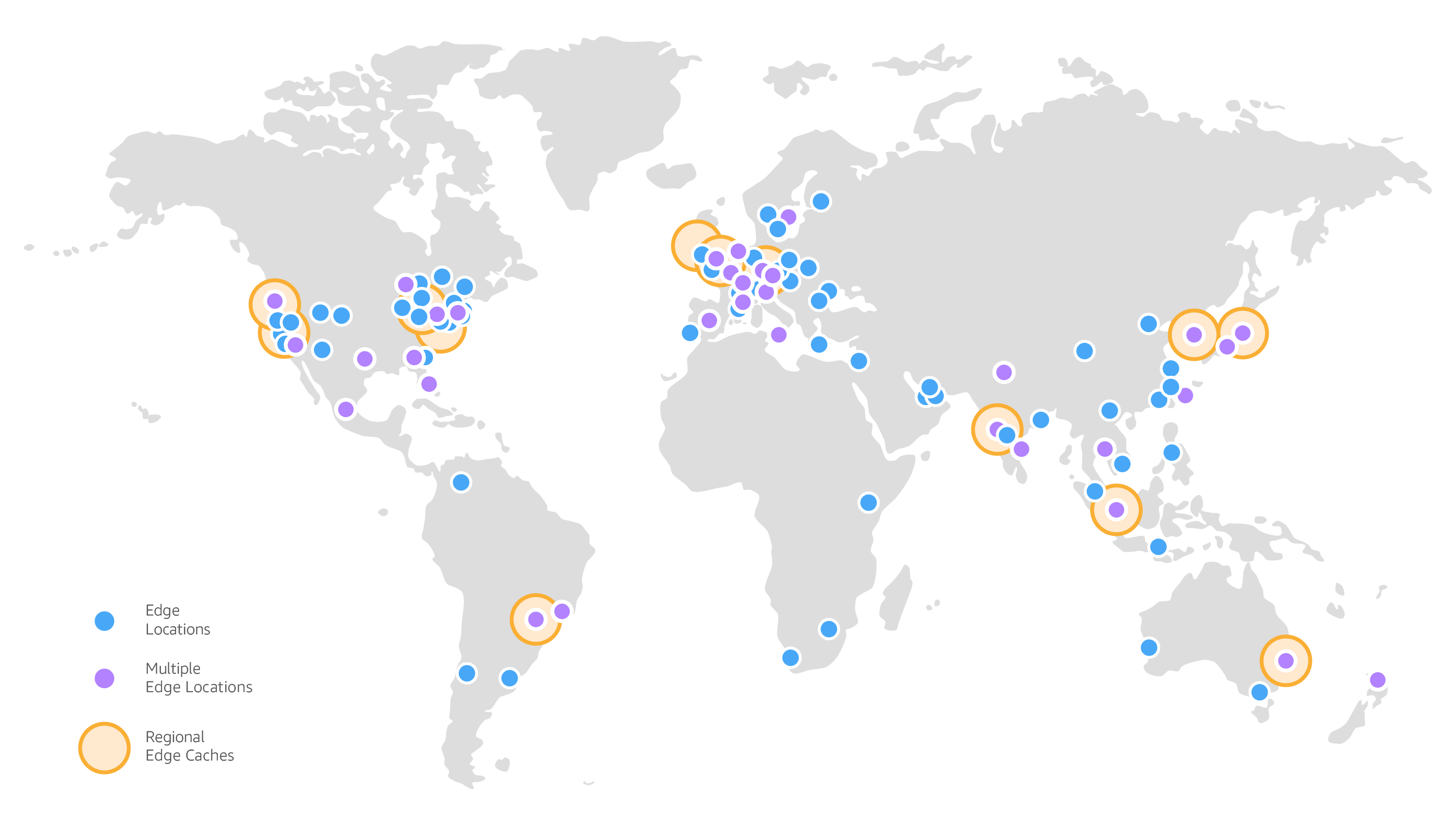
The Three-Tier Shit Show
CloudFront has this weird three-tier architecture that AWS loves to overcomplicate:
Edge Locations are the 700+ servers where your content gets cached. These are spread across major cities, but don't expect even coverage. Some locations are fast, others will make you want to throw your laptop. The official edge location list changes constantly because AWS keeps adding more, which is nice, but good luck figuring out which one your users are actually hitting.
Regional Edge Caches sit between the edge locations and your origin. AWS has 13 of these globally, and they're supposed to reduce origin load. In practice, they add another layer of potential failure. When something goes wrong, you get to debug through two cache layers instead of one.
Embedded PoPs are AWS's attempt to get even closer to users by putting cache servers inside ISP networks. Sounds great until you realize you have zero visibility into which ones are working and which ones are basically broken.
Cache Behavior Hell

Here's where CloudFront gets really fun. Cache behaviors in CloudFront are batshit insane - whoever designed the priority system was either drunk or hates developers. They work backwards from what any sane person would expect. You configure cache behaviors to tell CloudFront how to handle different URL patterns, but good luck figuring out which one actually matches.
I learned this the hard way last Tuesday when CSS updates deployed everywhere except three random edge locations in Germany. Spent 6 hours pulling my hair out before realizing we had cache behavior priority conflicts. Rule #2 was overriding rule #1 because reasons. The CloudFront troubleshooting docs are actually decent, unlike most AWS documentation.
Cache invalidations are 'instant' according to AWS marketing, but I've timed them at 15-20 minutes regularly. AWS docs claim 2 minutes maximum - that's complete horseshit. I've literally watched paint dry faster. Use versioned URLs instead - it's faster and actually works.
AWS Integration: The Lock-In
The only reason to choose CloudFront over Cloudflare or Fastly is if you're already deep in the AWS ecosystem. Data transfer from S3 or EC2 to CloudFront is free, which is nice because AWS charges for everything else.
CloudFront works well with S3 for static sites and ALB for dynamic content. The ACM integration for SSL certificates is actually smooth, and Shield Standard DDoS protection is included.
Here's where AWS gets you by the balls - once you're using CloudFront, you're trapped in their pricing nightmare. Scaling globally means your AWS bill starts looking like a small country's GDP. Asian traffic costs 3x more than US traffic - $0.140/GB vs $0.085/GB. Nobody mentions this gotcha until you get a $5000 bill for serving videos to users in Tokyo.
Performance Reality Check

CloudFront performance varies wildly by location. US East Coast? Lightning fast. Southeast Asia? Prepare for disappointment. The AWS global infrastructure page shows all their edge locations, but doesn't mention that some are significantly better than others.
We eventually said fuck it and switched to Cloudflare after getting daily complaints from our Singapore users about 8-second page loads. Our Bangkok users were threatening to cancel subscriptions. Cloudflare's edge network just performed better in those regions. CloudFront is fine if your users are mostly in North America and Europe.
The Bottom Line
CloudFront works fine if you're already paying AWS for hosting and don't want to deal with another vendor. It's not the fastest CDN, not the cheapest, and definitely not the most user-friendly. But it integrates well with other AWS services and won't randomly break your site.
Before committing: test your specific use case from multiple global locations, budget for Asian traffic costs, and plan your cache strategy around versioned URLs instead of invalidations. If you need global performance that doesn't suck everywhere, honestly consider Cloudflare first.



 Because AWS charges for literally everything: data transfer, requests, failed requests, successful requests, requests that looked at your distribution sideways.
Because AWS charges for literally everything: data transfer, requests, failed requests, successful requests, requests that looked at your distribution sideways. Good fucking luck with that. CloudFront's cache behavior priority system was designed by sadists. It's like CSS specificity but even more backwards and with zero documentation about what actually wins. The
Good fucking luck with that. CloudFront's cache behavior priority system was designed by sadists. It's like CSS specificity but even more backwards and with zero documentation about what actually wins. The