After two years of running Pulumi in production with a team that was initially skeptical as hell, I can tell you what actually happens when you bet your infrastructure on this thing. This isn't another tutorial or feature comparison - it's a real-world evaluation of what works, what doesn't, and what you'll actually experience when you bet your infrastructure on Pulumi.
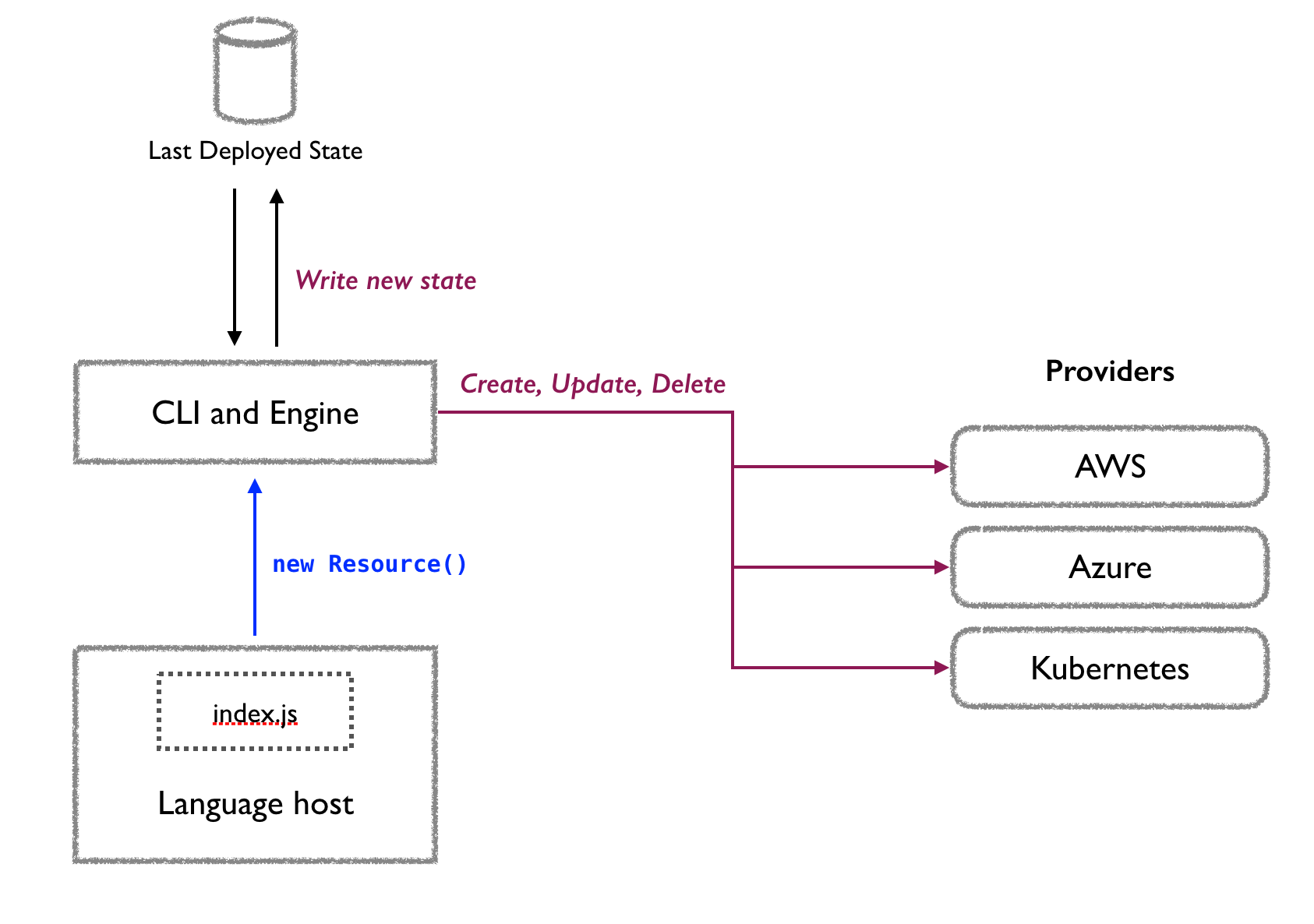
The core engine consists of the language host (runs your code), deployment engine (calculates changes), and resource providers (manage actual cloud resources). This separation is what makes Pulumi powerful - you get real programming languages with declarative infrastructure management.
OK Fine, Some Things Actually Work
Developer Experience is Legitimately Superior: The IDE integration isn't marketing fluff. Having real autocomplete, type checking, and refactoring tools for infrastructure code changes everything. When a developer can Ctrl+Click to jump to a resource definition or get IntelliSense for AWS resource properties, it eliminates the constant context switching between documentation and code.
Testing Infrastructure Code Actually Works: Unlike YAML-based tools where "testing" means hoping your syntax is correct, Pulumi enables real unit tests. This changes everything - you can catch configuration errors, dependency issues, and resource conflicts before they hit production. The ability to mock cloud services and validate infrastructure logic has prevented several outages.
Complex Logic Becomes Manageable: When you need to create 20 similar resources with slight variations, or implement conditional resource creation based on environment variables, real programming languages shine. A simple for loop in TypeScript beats wrestling with Terraform's count and for_each.
What Nobody Warns You About (The Shit Parts)
Pricing Will Hurt Your Budget: The pricing model starts innocent enough at $40/month for teams, but then it scales based on resources managed. We're paying around $580/month for our setup. Terraform Cloud would cost us maybe $120-140/month for the same thing. Yeah, it's expensive.
Ecosystem Gaps Are Real: While Pulumi supports 290+ providers, newer cloud services often appear in Terraform first. We've had to wait 3-6 months for critical AWS features to become available in Pulumi. The auto-generated providers help, but they're not always reliable.
Learning Curve for Operations Teams: Despite marketing claims about "familiar languages," operations engineers who've spent years with declarative tools struggle with imperative infrastructure code. The mental model shift from "describe what you want" to "program how to get it" creates friction in teams with mixed backgrounds.
Does This Thing Actually Work When It Matters?
State Management is Solid: Pulumi Cloud's state backend has been reliable. No data loss, no corruption issues in our experience. The automatic backups and versioning work as advertised. However, we've experienced 3 service outages in 2 years that prevented deployments entirely.
Deployment Speed: Infrastructure deployments average 15% faster than our previous Terraform setup, primarily due to better dependency resolution. However, the initial program execution adds 10-30 seconds of overhead that pure declarative tools don't have.
Error Handling is Fucking Terrible: When shit breaks, the error messages are useless. "Resource creation failed" - oh great, thanks Pulumi, really narrowed it down there. You'll spend way too much time digging through AWS CloudTrail to figure out what actually went wrong. Enable verbose logging from day one: pulumi up --logtostderr -v=9 - you'll be typing that command a lot.
How Your Team Will Actually React
Developers Love It: Front-end and back-end developers adopted Pulumi quickly. The familiar syntax and tooling reduced onboarding time from weeks to days. Code reviews for infrastructure became as natural as application code reviews.
DevOps Teams Are Mixed: Senior engineers appreciate the power and flexibility. Junior engineers and those from traditional operations backgrounds prefer the explicit nature of declarative tools. Plan for a 3-6 month transition period and additional training costs.
Security Teams Need Convincing: The policy as code features help, but security teams initially worried about developers having too much flexibility in infrastructure code. We addressed this with CrossGuard policies and mandatory code reviews.
The Times It Completely Screwed Us Over
So this one time, AWS provider... I think it was 5.42.0? Maybe 5.41-something? Either way, it completely fucked our EKS setup overnight. Just stopped working. Error message was something like "InvalidParameterException: Cluster version 1.27 is not supported" which made absolutely no sense because we'd been running 1.27 for months.
Took us like 4 hours to figure out they changed the default Kubernetes version in the provider update. Four fucking hours. On a Tuesday morning. With production down. Now we pin every provider version because trust is apparently a luxury we can't afford.
Then there was this other clusterfuck where someone (who shall remain nameless but knows who they are) manually tweaked an RDS instance in the AWS console. Don't ask me why. Pulumi completely lost its shit and started throwing "resource differs from expected state" errors everywhere. Real helpful, right?
Spent most of a Saturday comparing Pulumi state files to actual AWS resources line by line until we figured out what got changed. Good times. Really what I wanted to do with my weekend.
Oh, and let's not forget the time when our deployment just... hung. For like 2 hours. Some kind of dependency loop that the engine couldn't figure out, timeout error was useless as always, and we couldn't even cancel the damn thing properly. Had to pulumi cancel and then clean up the half-deployed mess manually. That was fun to explain to management.
The Bottom Line
Pulumi isn't a revolutionary replacement for existing tools - it's an evolutionary improvement with clear trade-offs. The developer experience improvements are real and significant. The ability to test infrastructure code and use familiar programming constructs adds genuine value. However, the higher costs, smaller ecosystem, and team transition challenges mean it's not automatically the right choice for every organization.
For teams with strong development backgrounds building cloud-native applications, Pulumi's benefits outweigh the costs. For traditional infrastructure teams managing stable, well-understood environments, the advantages are less compelling.
The tool itself is production-ready, but success depends more on team composition and organizational priorities than technical capabilities.

