I've been using AWS CDK in production for three years now, and let me tell you - it's been a wild fucking ride. CDK is Amazon's answer to everyone who's ever screamed at their laptop while debugging YAML indentation errors at 2 AM. Instead of wrestling with CloudFormation JSON like it's 2003, you get to write infrastructure in actual programming languages.
Instead of debugging indentation errors in YAML files late at night, you write TypeScript (or Python, Java, C#, Go) and get actual compiler errors when you fuck up. The language support means you can use your IDE's autocomplete instead of memorizing CloudFormation resource properties.
The catch? CDK still deploys through CloudFormation under the hood, so when things break, you're still debugging CloudFormation stack errors. But at least you wrote the code in a language that doesn't make you question your career choices.

How CDK Actually Works (The Parts That Matter)
CDK has three main pieces you need to understand:
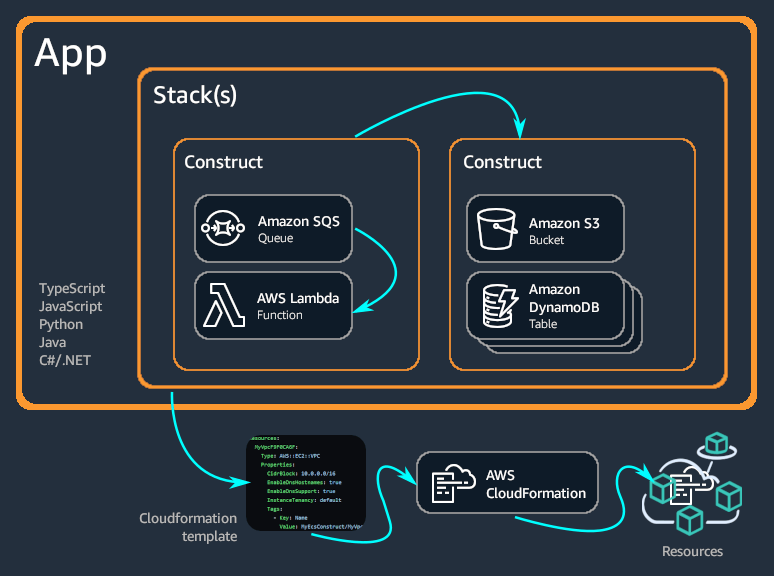
Constructs are basically infrastructure Lego blocks. AWS built these at three levels: L1 constructs are just CloudFormation resources with TypeScript wrappers, L2 constructs have sane defaults so you don't have to specify every fucking parameter, and L3 constructs are pre-built patterns like "web app with database." Stick with L2 constructs unless you need something specific.
Apps and Stacks organize your code, though "organize" is generous. One app can have multiple stacks - like one for networking, one for databases, one for your actual application. Keep stacks small or CloudFormation's 500-resource limit will murder your deployment. I was cruising along at 497 resources like an idiot, thinking "I'm basically a DevOps genius." Added 3 more Lambda functions for some bullshit feature request, and boom - deployment dies with a resource limit error. Spent my Saturday morning refactoring stacks instead of drinking coffee like a normal person.
CDK CLI is what actually does the work. Run `cdk synth` to see what CloudFormation shit it generates (always check this first), `cdk diff` to see what's about to break, and `cdk deploy` to pray it works. The CLI converts your code into CloudFormation templates - which is exactly why deployments take forever.
Which Language to Pick (And Why It Matters)
Look, here's the brutal truth about CDK language support that nobody wants to admit:
- TypeScript: Use this. Seriously. It's what AWS built CDK in, so you get new features first, best documentation, and most Stack Overflow answers. Every example online is in TypeScript.
- Python: Fine choice if your team already does Python. Documentation is okay, but you'll spend time translating TypeScript examples. Great for data teams who hate TypeScript.
- Java: If you're stuck in enterprise Java hell, this works. Lots of boilerplate, but at least you get strong typing. Expect verbose code.
- C#/.NET: Decent if you're already .NET shop. AWS actually keeps this up to date, unlike some of their other language bindings.
- Go: Fully supported as of 2025, requires Go 1.18+. Good choice if your team is already Go-focused.
Just pick TypeScript and thank me later. I watched a team spend three weeks trying to make Python CDK work exactly like the docs promised. Spoiler alert: the docs are all TypeScript examples poorly translated to Python. Every Stack Overflow answer, every blog post, every fucking GitHub issue assumes you're using TypeScript.
Fight this choice and you'll be debugging npm dependency hell at 2 AM while your production deployment shits itself and your manager asks why the "simple infrastructure change" is taking 6 hours. Don't be that person.

