What It Actually Scans
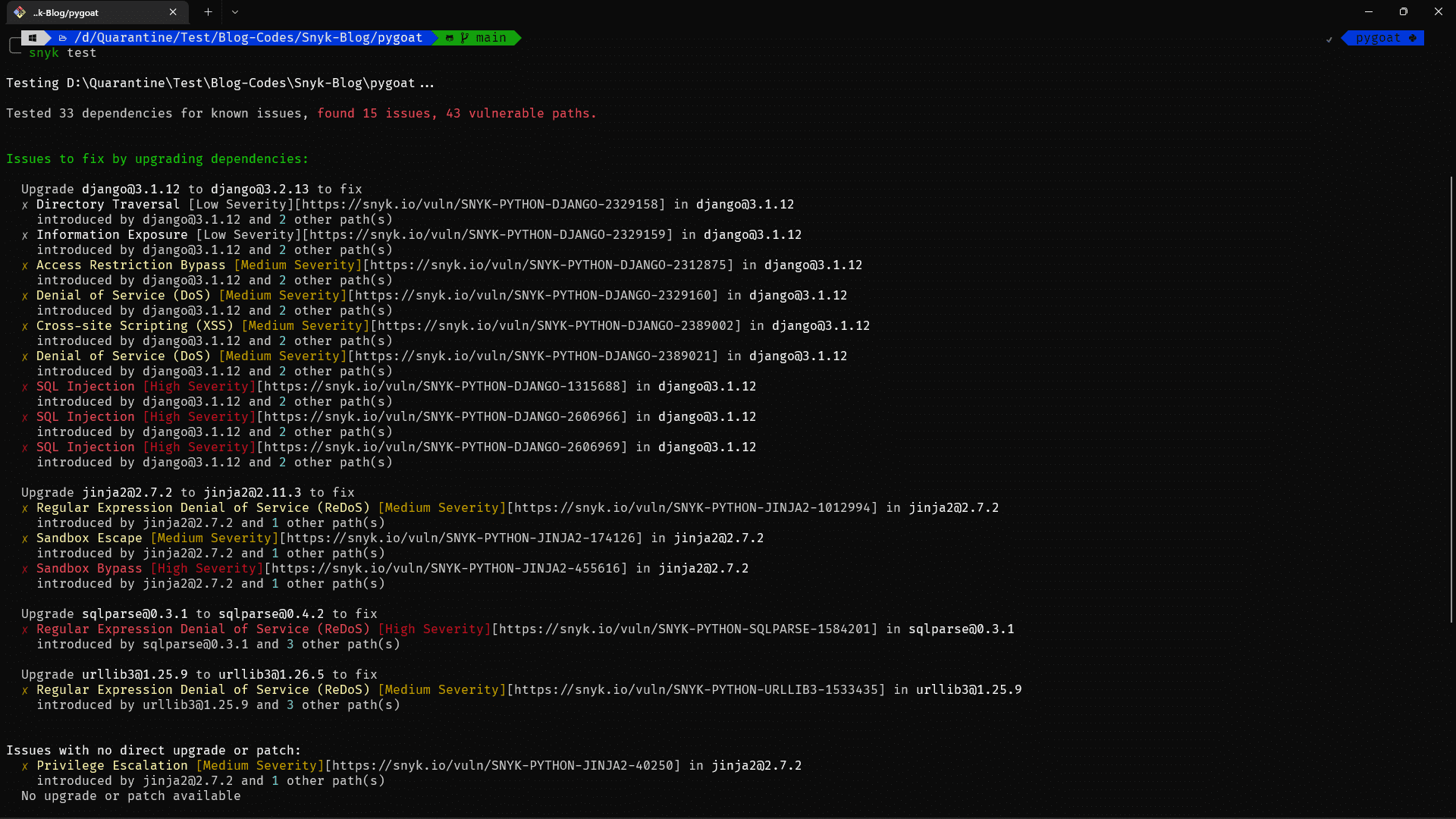
Dependency Vulnerabilities - Main reason people use Snyk. Scans package.json, requirements.txt, Gemfile and whatever other dependency files you've got lying around. I use it mostly on Node projects where it's caught actual vulnerabilities that npm audit missed or marked as "low severity bullshit". Found some prototype pollution bug in lodash 4.17-something that would've let attackers fuck with our session handling. Sometimes flags minor crap that doesn't actually affect how you're using the library, but when it finds real shit it's worth the money.
Code Analysis - Scans your source code for security problems. Found actual XSS issues in our React components - specifically dangerouslySetInnerHTML usage that looked safe but wasn't. Also caught some SQL injection patterns in raw queries we thought were fine. Sometimes flags weird framework patterns that aren't actually vulnerable, but when it finds real shit it saves your ass. Had it suggest updating to a newer version of some library that completely broke our authentication flow - took 3 hours to roll that back and ignore the "fix".
Container Scanning - Scans Docker images for vulnerabilities. Use this in CI and it's caught base image problems we'd never have found manually. Saved us when node:16 had some container escape bug that could've been really bad. The fix recommendations actually help - tells you which Alpine or Ubuntu base images don't have the problem instead of just saying "update everything."
Infrastructure as Code - Scans Terraform and Kubernetes configs for security problems. Caught overly permissive IAM roles in our AWS setup that would've been a nightmare to fix in prod. Found S3 buckets configured for public read that shouldn't have been. Better than the free tools that just spam you with 200 "potential" issues.
How Fast Is This Thing?
Scans are fast enough that you won't want to kill yourself waiting. Our Node project - I think it's like 40K lines? maybe more? - takes like 90 seconds for full dependency and code scanning. Could be 2 minutes if it's feeling slow. CLI output actually makes sense - shows severity levels and links to fix info instead of just dumping 50 CVE numbers with zero context about which ones will actually bite you.
Integration with Development Workflows
I use Homebrew on Mac because npm global install kept breaking every time Node updated. Authentication works fine with snyk auth unless you're behind corporate firewall hell - then you need API tokens.
We run it in GitHub Actions on every PR, catches issues before they hit main and blow up production. The VS Code plugin gives real-time feedback while coding, though it's slow as shit on large projects - takes like 30 seconds to scan a React app with maybe 200 components? Could be more, I didn't count.
The web dashboard tracks trends across projects but loads slower than a 56k modem. Still beats manually parsing CLI output from 12 different repos.