Remember when everyone had sticky notes with passwords all over their monitors? Okta exists because managing login credentials is a nightmare that scales terribly.
Here's what actually happens without Okta: Sarah from accounting forgets her Salesforce password, calls IT. IT resets it. Two days later, she forgets her Slack password. Another ticket. Meanwhile, Bob from marketing is using "company123" for everything because he's tired of the reset dance.
Okta centralizes all this shit so your employees log in once and get access to everything they need. No more password reset tickets, no more "I can't access the tool I need to do my job" Slack messages at 3 PM.
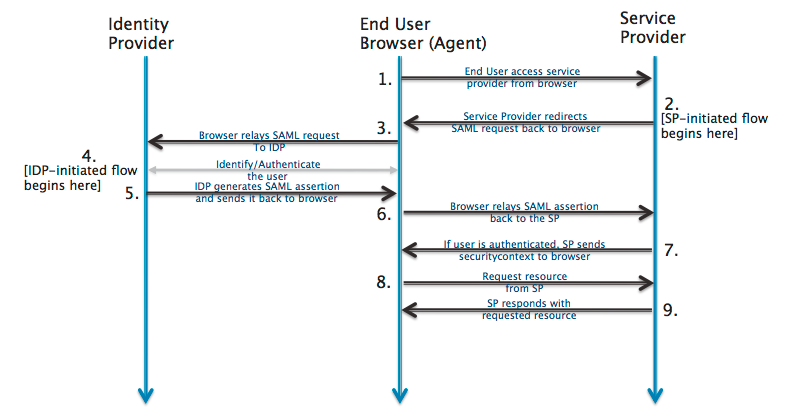
How Okta Actually Works (The Stuff That Matters)
Okta actually runs two completely different products, which confused the hell out of me at first:
Workforce Identity ($6/user/month to start): This is for your employees. When someone joins your company, you add them to Okta once and they automatically get access to Slack, Gmail, Salesforce, whatever. When they leave, you delete them from Okta and they lose access to everything. No more finding out someone who left 6 months ago still has admin access to your AWS account.
Auth0 (starts at $3,000/month): This is for customer-facing apps. If you're building a website where people need to create accounts, Auth0 handles the "Sign up with Google" buttons, password requirements, and all that user management crap so you don't have to build it yourself.
That $6 price is bullshit though. You need the $17/user plan if you want features that actually matter, like blocking logins from sketchy countries.
The Security Story (Why Your CISO Will Love It)
Here's why Okta isn't just convenient - it's actually more secure than the password chaos you have now:
When someone tries to log into your apps through Okta, it checks a bunch of things: Is this the same device they usually use? Are they logging in from their usual location? Is it 3 AM and they're suddenly in Russia? If something looks fishy, it makes them prove it's really them with 2FA.
The best part: When someone's credentials get compromised in some random data breach (and they will), the attacker can't do anything useful because they still need to get past Okta's security checks.
War story: In our first month, Okta caught someone trying to log into our Salesforce from Seattle, then Mumbai 10 minutes later. Turns out our VP of sales had his password leaked in some data breach and didn't tell anyone. Without Okta, that asshole would've had access to our entire customer database.
The other thing that saved our ass: when Karen from HR clicked that phishing email (because of course she did), Okta blocked the login because it came from a sketchy IP in Romania. Her password was compromised, but the attacker couldn't actually access anything.
The Integration Reality (This is Where Okta Shines)
Okta has over 7,000 pre-built integrations with basically everything your company uses. And before you ask - yes, they probably have your weird legacy app from 2003 too.
Okta speaks SAML, OAuth, OpenID Connect, and even ancient LDAP for those systems from the Bush administration. In theory, you click a few buttons and it works. In practice, you'll be debugging certificate issues at 2AM because someone fat-fingered the metadata URL.
How long this actually takes:
- Popular apps like Salesforce work fine, they've got templates
- Weird legacy stuff will ruin your weekend - SAML configuration is always broken somewhere, usually the certificate path
- Custom apps? Hope your developers know OAuth because debugging "invalid_grant" errors at 3AM is nobody's idea of fun
- Pro tip: When Okta says "15 minutes setup", they mean if everything goes perfectly and your app isn't broken
The newer stuff they're working on includes managing service accounts and API tokens, which beats hardcoded credentials in CI/CD. When shit breaks, their dev docs are actually helpful (rare for enterprise software).