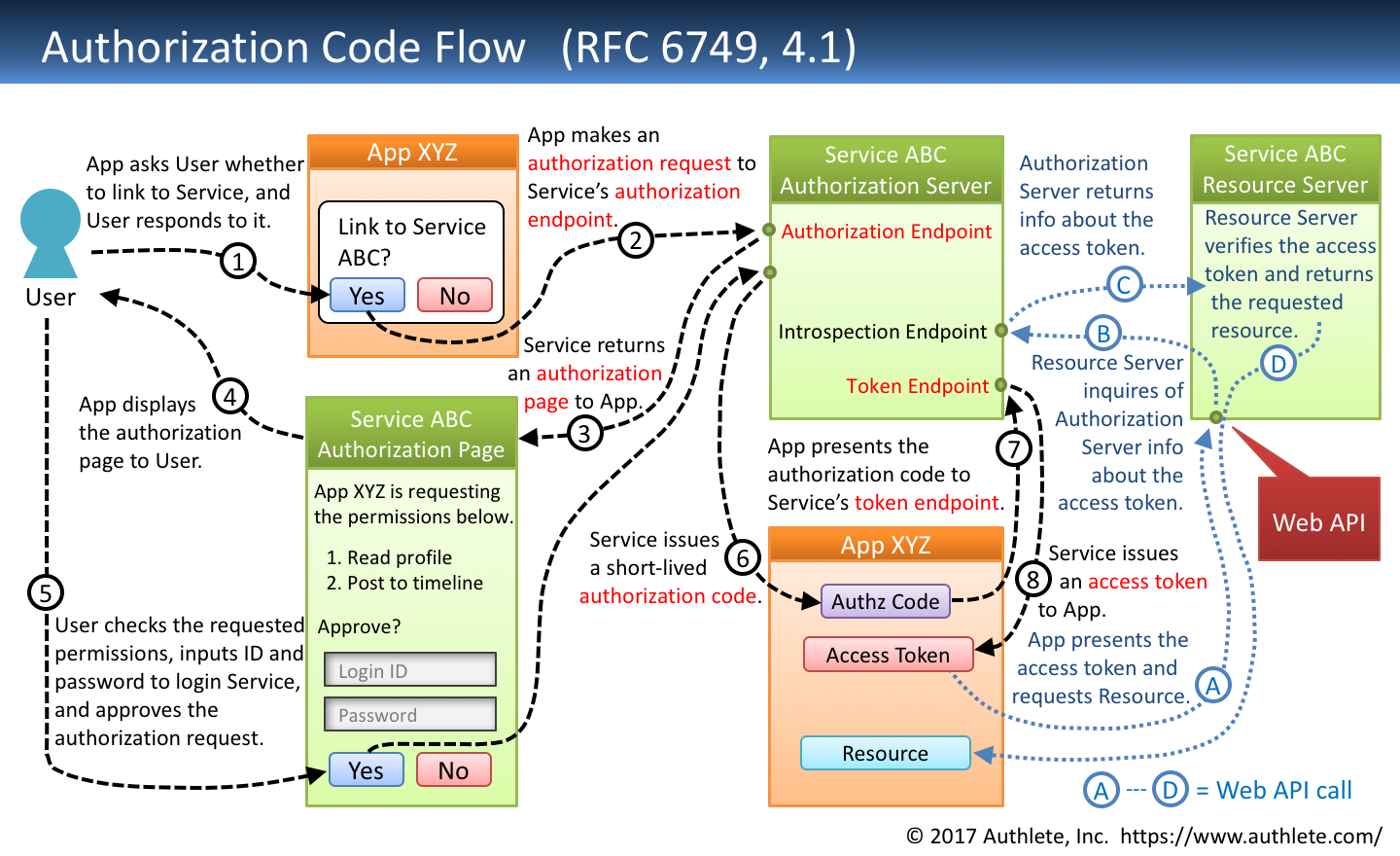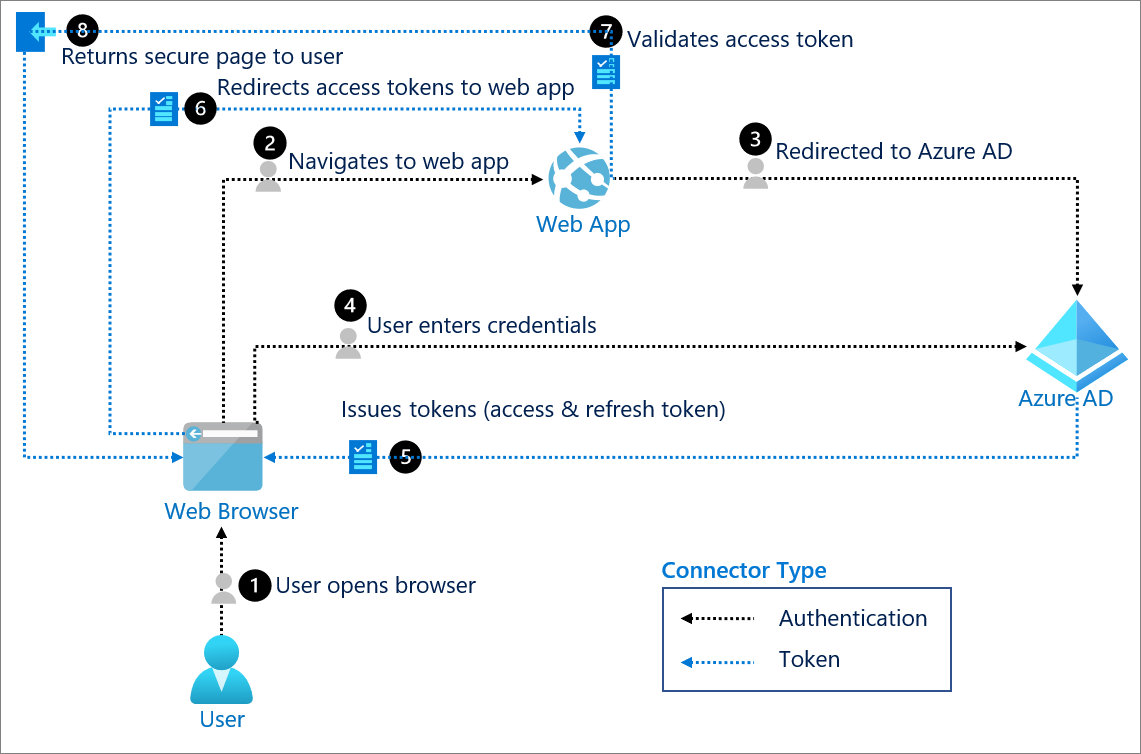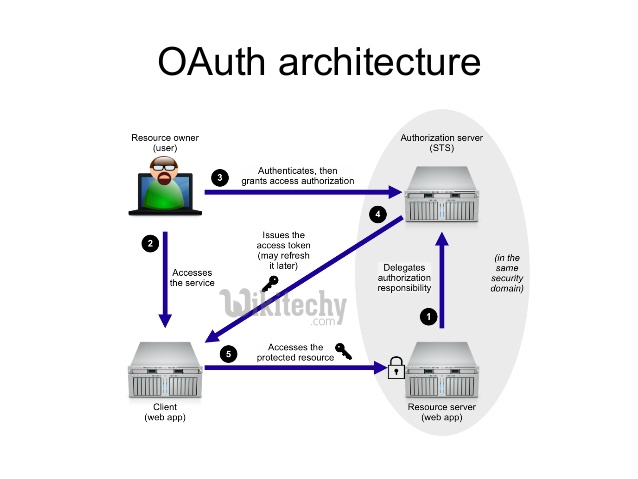
OAuth has four players, and yes, the naming is confusing as hell. The Resource Owner (you), the Client (the app), the Resource Server (where your data lives), and the Authorization Server (the bouncer checking IDs). Most people think OAuth is about login—it's not. OAuth is about authorization. It's the difference between proving who you are and proving what you can do.
I once debugged a legacy system from 2008 that stored Twitter passwords in a MySQL table with no encryption. The table was called user_secrets. I died a little inside. That's the world OAuth 2.0 was built to replace—no more password sharing between random apps and services.
The OAuth 2.0 Authorization Framework (RFC 6749) launched in 2012, but it's been through some shit. The original spec had holes you could drive a truck through. Then RFC 6819 came along with security considerations. Then OAuth 2.1 (still in draft as of September 2025) tried to patch the worst problems by making PKCE mandatory and deprecating the implicit flow entirely.
Here's what changed my perspective on OAuth: it's not really about security—it's about delegation. Instead of giving Spotify your Facebook password, you give Facebook permission to tell Spotify "yeah, this person is cool." The security comes from limiting what apps can do and revoking access when things go sideways.
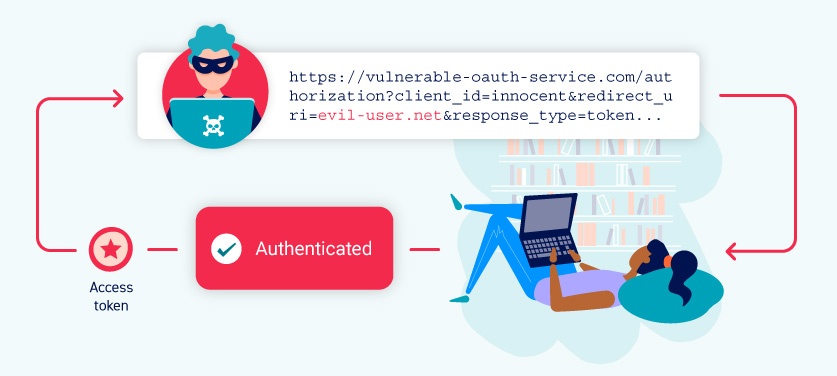
But 2024-2025 proved that OAuth's biggest weakness isn't in the protocol—it's in the humans implementing it. ShinyHunters compromised Google, Qantas, and dozens more using OAuth device flow attacks that bypassed MFA without exploiting a single software bug. They just called people and talked them into authorizing malicious applications. Social engineering beats cryptography every time.
The attack works because OAuth authorization screens look legitimate—they ARE legitimate. When someone calls pretending to be IT support and asks you to visit login.microsoftonline.com and enter a code, you're visiting the real Microsoft login page. The deception happens in the authorization step, not the authentication step. Users see "Security Compliance Tool" requesting access to their Salesforce data and click "Allow" because it sounds official.
What makes this worse is that once attackers get OAuth tokens, they have persistent access that often bypasses conditional access policies. Unlike stolen passwords, these tokens can remain valid for months. They appear as normal API activity, making detection incredibly difficult.
The 2025 reality is that OAuth 2.0 is simultaneously everywhere and nowhere. Every major platform supports it—Google, Microsoft, GitHub, Salesforce, Twitter, Facebook. Your users interact with OAuth dozens of times per day without realizing it. But most organizations have zero visibility into OAuth applications, no governance around OAuth permissions, and no monitoring for OAuth abuse.