Remember the dark ages before 2015? I spent thousands of company dollars buying SSL certificates from Verisign, DigiCert, and other certificate vendors who charged $200-500 per domain annually. Then I had to set calendar reminders to renew them manually before they expired and took down production.
I've been paged at 2am because someone forgot to renew a certificate. I've seen entire ecommerce sites go dark over weekend because the certificate expired on Saturday and nobody was around to fix it. Let's Encrypt ended that nightmare forever.
How Let's Encrypt Killed the Certificate Racket
Let's Encrypt launched in 2015 as a nonprofit run by the Internet Security Research Group with backing from major tech companies who were tired of the certificate tax. Mozilla, Google, Facebook, and others funded it because they knew HTTPS adoption was being held back by greedy certificate authorities.
The business model is simple: make certificates free and force automation. No more manual certificate signing requests. No more waiting 3-5 business days for validation. No more paying hundreds per year for the privilege of not having your site show scary browser warnings.
As of September 2025, Let's Encrypt serves over 650 million websites with 63.4% market share. They became the largest certificate authority in the world by doing the obvious thing: making certificates free.
The ACME Protocol: Automation That Actually Works
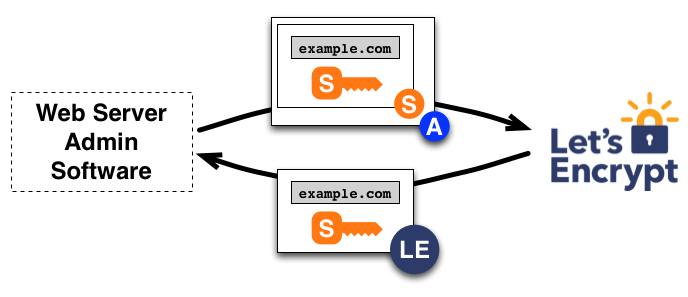
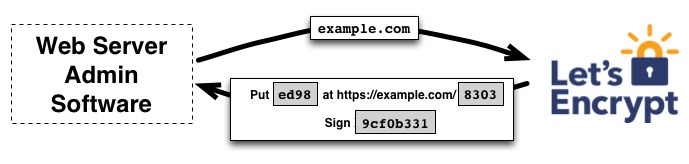
Here's what the ACME protocol does that the old certificate process couldn't:
The Old Way (Certificate Hell):
- Generate a certificate signing request manually
- Submit it to a CA with payment
- Wait 3-5 business days for domain validation
- Download certificate files
- Install them manually on your server
- Set a calendar reminder to do this shit again in 1-2 years
- Inevitably forget and have your site go down
The ACME Way (Set It and Forget It):
- Client requests certificate for domain
- Let's Encrypt challenges domain ownership via HTTP or DNS validation
- Challenge completes in seconds, certificate issued automatically
- Certificate renews itself every 90 days without human intervention
The 90-day renewal sounds scary but it's actually brilliant - forces you to automate renewal, which you should do anyway. Manual certificate management is how production sites die.
Certificate Infrastructure That Doesn't Suck
Let's Encrypt runs a proper certificate infrastructure with multiple roots and intermediates:
Root Certificates:
- ISRG Root X1 (RSA 4096) - trusted by everything until 2030
- ISRG Root X2 (ECDSA P-384) - newer, smaller, faster
Current Intermediate Certificates:
- E7 and E8 (ECDSA P-384) for ECDSA subscriber certificates
- R12 and R13 (RSA 2048) for RSA subscriber certificates
All intermediates valid until March 12, 2027. Unlike commercial CAs that change their intermediate certificates randomly and break your chain of trust, Let's Encrypt publishes their certificate strategy years in advance.
Recent Changes That Actually Matter
IP Address Certificates: July 2025 update - you can now get certificates for IP addresses, not just domains. Useful for internal services and IoT devices that don't have proper DNS.
OCSP is Dead: As of August 6, 2025, Let's Encrypt killed OCSP because it was slow and leaked privacy. Now uses Certificate Revocation Lists (CRL) which are faster and don't tell the CA every site you visit.
No More Expiration Emails: June 4, 2025 - they stopped sending expiration warnings because if you're still relying on email reminders instead of automation, you're doing it wrong.
These aren't just technical updates - they're forcing the industry toward proper certificate automation practices.