AWS Organizations is what saves your ass when you're managing 50+ AWS accounts and losing track of who's spending what and who has access to what. Instead of logging into dozens of accounts individually like some kind of masochist, you get one central place to keep your accounts from going completely rogue.
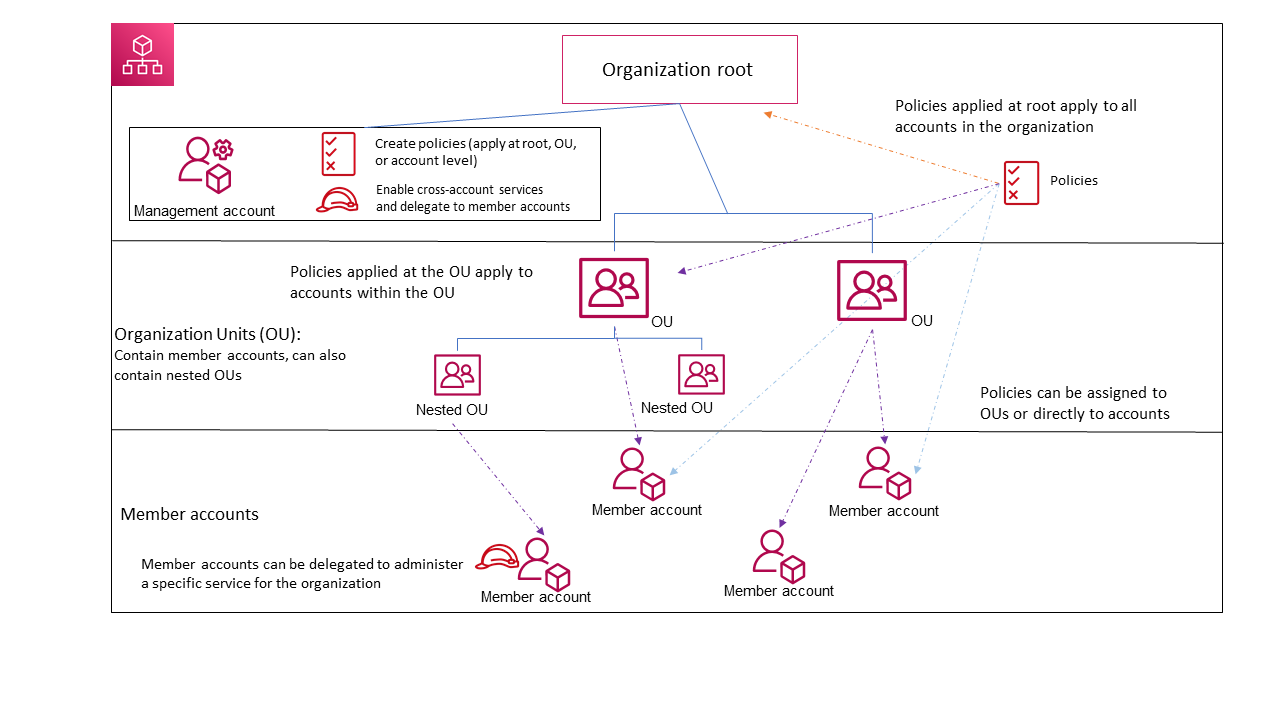
The basic idea: one management account controls everything else. Think of it as the parent account that tells all the other accounts what they can and can't do. The management account gets god-mode permissions over all member accounts and becomes financially responsible for everything - which makes CFOs nervous and backup strategies complicated.
Fair warning: choosing your management account is permanent. Fuck this up and you're rebuilding your entire organization from scratch. We've seen teams do exactly that because they picked the wrong account initially.
Core Architecture and Components
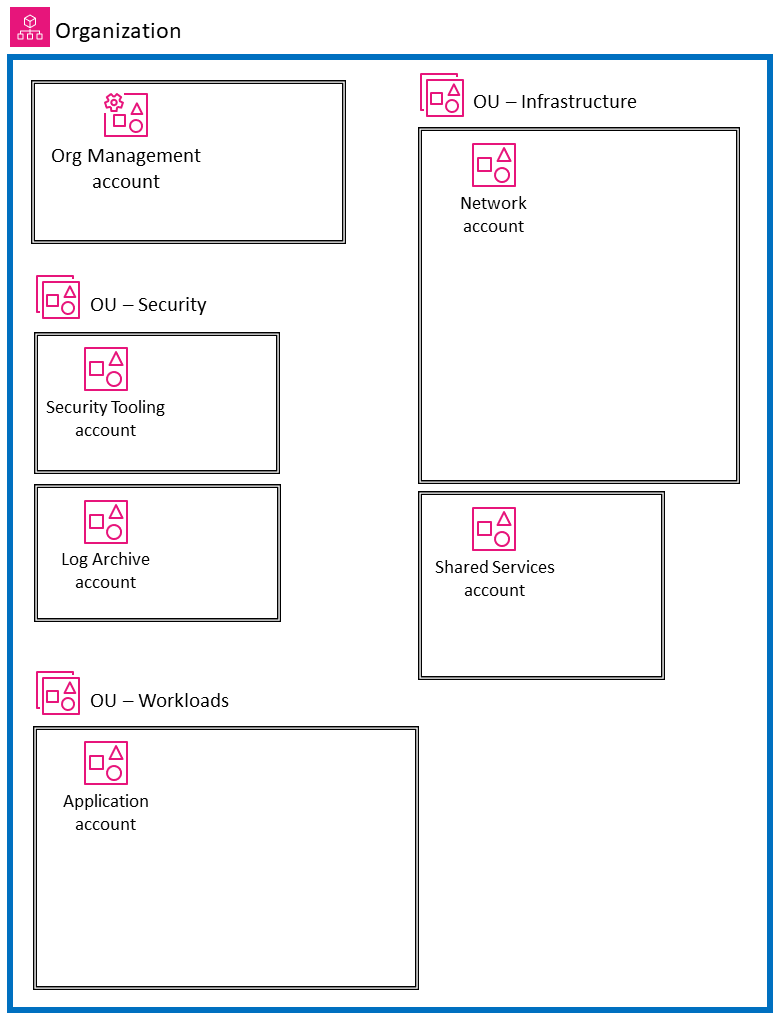
Organizations structures accounts using Organizational Units (OUs) - basically folders for grouping accounts. You can nest these up to 5 levels deep, though most teams find 2-3 levels plenty before the structure becomes more confusing than helpful.
The real power comes from policy management, where you get multiple ways to control what accounts can do:
- Service Control Policies (SCPs) - Set maximum permissions. These will break your deployments in creative ways until you figure out all the exceptions you need. Budget time for debugging why your perfectly valid IAM policy suddenly doesn't work.
- Resource Control Policies (RCPs) - Launched November 13, 2024, so good luck finding Stack Overflow answers when they break your setup. Unlike SCPs that control what principals can do, RCPs control who can access your resources - finally giving you a proper data perimeter. Works with S3, STS, KMS, SQS, and Secrets Manager, assuming you can figure out the policy syntax.
- Backup Policies - Centrally manage backup requirements across accounts
- Tag Policies - Enforce consistent tagging so finance can actually track where money goes
Why You Actually Need This
But here's the reality check: Organizations isn't just a nice-to-have for tidy account structures. It becomes essential when you're dealing with enterprise-scale chaos. AWS Control Tower builds on top of Organizations to give you automated account provisioning and guardrails, which sounds great until you realize that Control Tower also makes assumptions about how you want to organize things that might not match your reality.
The real wins:
- Consolidated billing - One bill instead of 47 separate bills that nobody wants to reconcile
- Cross-account resource sharing via AWS Resource Access Manager - Share VPCs and other resources without duplicating infrastructure
- Centralized audit logs through CloudTrail organization trails that member accounts can't disable or fuck with
- Data perimeters using RCPs to prevent external access (assuming you can get the policies right)
Bottom line: Organizations turns managing accounts from a daily nightmare into something that only hurts when you fuck it up. Which you will, but at least you'll only fuck it up once across your entire setup instead of 50 times in 50 different accounts.
Latest 2024/2025 Security Enhancements

Centralized Root Access Management (November 2024) - AWS finally solved the "member account password nightmare." You can now eliminate passwords from member accounts entirely and manage root access centrally from your management account. No more spreadsheets tracking 500+ root passwords.
Mandatory MFA for Member Accounts (Spring 2025) - AWS will require MFA for Organizations member account root users starting in Spring 2025, unless you enable centralized root access management. Between April and October 2024, over 750,000 AWS root users enabled MFA in preparation.
FIDO2 Passkey Support (June 2024) - You can now use passkeys for MFA, which is both more secure and less annoying than authenticator apps. Customer registration rates for phishing-resistant MFA increased by over 100% after this launched.