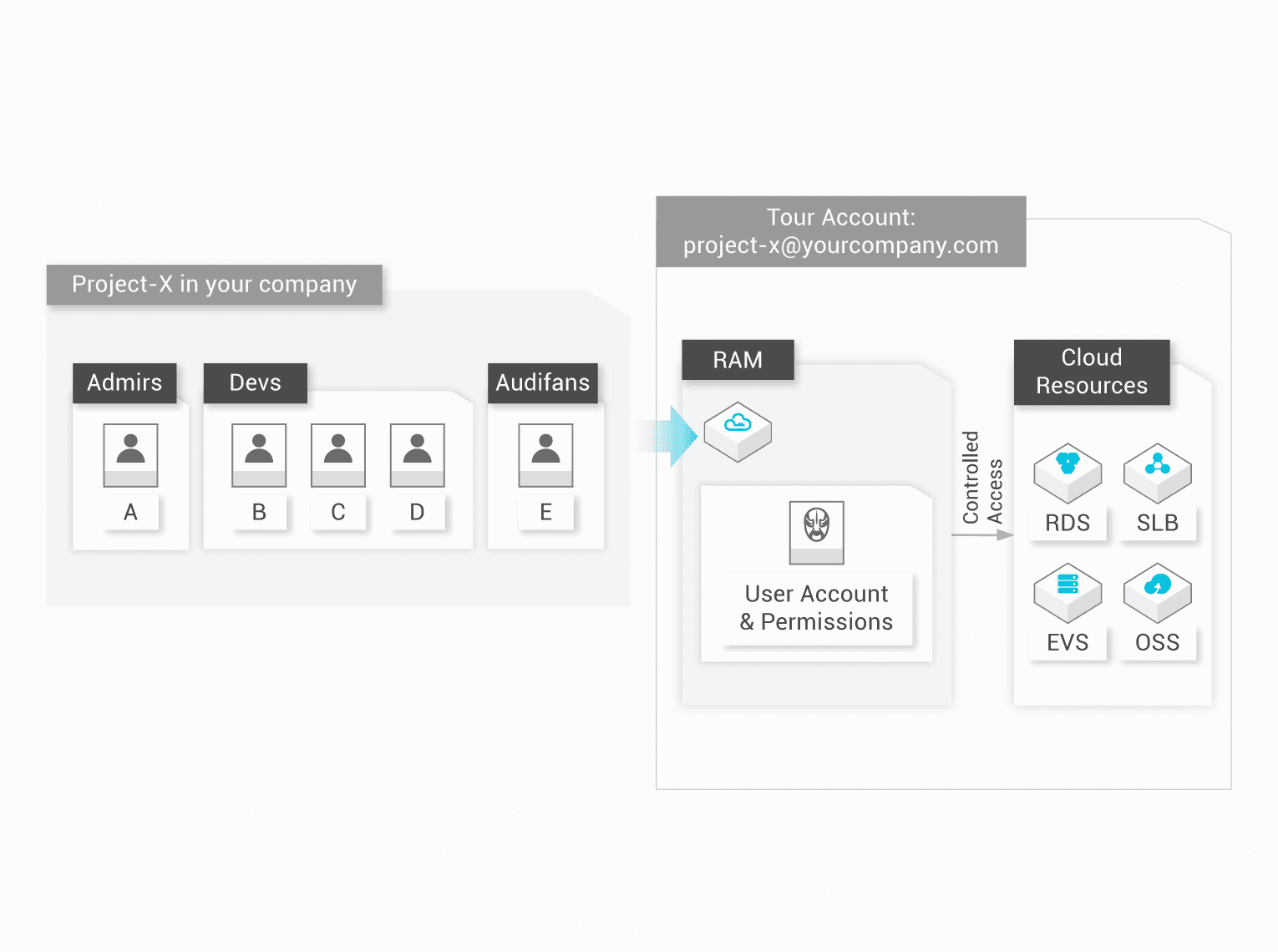
Remember the last time someone accidentally deleted production? Or when your CI/CD pipeline broke because some jackass rotated the service account key without telling anyone? Yeah, RAM exists to prevent that shit.
The Real Problem RAM Solves
Here's what actually happens without proper access control: Your junior dev gets admin access because "it's easier than setting up proper permissions," your marketing team somehow has write access to the database, and your deployment fails every Friday at 4pm because tokens expire at the worst possible moment.
I've seen production go down for... shit, I think it was 3 hours? Maybe 4? because someone gave the wrong person ECS instance termination permissions. Another time, our monthly bill jumped from like two grand to fifteen fucking thousand because a contractor spun up 200+ instances in us-east-1 "testing" auto-scaling. Took us 3 hours to notice because monitoring was configured for our usual 5-instance baseline. Fun times explaining that to the CFO. Access control matters.
What RAM Actually Does (Without the Bullshit)
RAM is Alibaba Cloud's answer to AWS IAM, except it doesn't cost extra. You create users, slap them into groups, write policies that hopefully don't break everything, and pray your STS tokens don't expire during critical deployments.
The policy language is JSON-based, which means you'll spend way too much time figuring out why your carefully crafted permission isn't working. Spoiler: it's usually a typo in the resource ARN like acs:oss:*:*:mybucket/* when you meant acs:oss:*:*:my-bucket/* (yes, that hyphen matters). But once you get it right, it works across all Alibaba Cloud services without requiring you to configure access for each one separately.
Unlike Azure Active Directory pricing which will bankrupt you, or Google Cloud IAM which assumes you love YAML, RAM keeps things simple. Check out the getting started guide for the basics, though it glosses over the parts where things actually break.
Before you commit to this mess, you probably want to know how it stacks up against the other identity nightmares. Trust me, each platform has its own special way of making you regret your career choices.
The STS Token Dance
Here's where things get fun. Need temporary access? Use Security Token Service. These tokens are great... until they expire in the middle of a deployment and you're debugging at 2am wondering why your app can't connect to RDS.
How STS Works: Your app authenticates with permanent credentials, requests a temporary token with specific permissions, uses that token for actual operations, and automatically gets denied when the token expires. Simple, effective, and guaranteed to break at the worst possible moment if you don't plan expiration properly.
Pro tip: Set your token expiration to something reasonable. The defaults changed at some point - I think it used to be longer? Anyway, check your expiration settings. I learned this the hard way when our entire CI/CD completely died because tokens expired during a... I dunno, maybe 2-hour deployment? Felt like forever.
MFA: Because Passwords Are for Amateurs
RAM supports multi-factor authentication using standard TOTP apps like Google Authenticator or Authy. Enable it, especially for production access. Yes, it's annoying when you're trying to fix something at 3am and can't find your phone, but it's less annoying than explaining to your CEO why someone social-engineered their way into your cloud account.
I enable MFA everywhere now after our incident. Yeah, it's annoying when you're debugging at 3am and can't find your phone, but it's way less annoying than explaining to your CEO why someone social-engineered their way into production. The flow is simple: username/password → system demands TOTP code → you fumble for your phone → enter the 6-digit code before it expires → pray you didn't fat-finger it. Takes 10 extra seconds, saves you from being the asshole who got breached.
The RFC 6238 TOTP standard means any authenticator app works, unlike some proprietary MFA systems that lock you into specific vendors. For enterprise setups, check out hardware security keys for the security-paranoid folks.
SAML Integration (AKA Making It Play Nice with Active Directory)
If your company uses Active Directory (and who doesn't?), you can set up SAML-based SSO so your users don't need yet another set of credentials. Fair warning: the SAML setup documentation skips some critical steps, and you'll probably spend a day figuring out why assertion mapping isn't working.
SAML Flow Simplified: User hits RAM → redirected to your AD → AD validates user → sends encrypted assertion to RAM → RAM maps AD groups to roles → user gets temporary access. Works great until attribute mapping breaks and everyone gets locked out.
Policy Language: JSON Hell That Actually Works
The policy syntax is straightforward JSON with the usual suspects: Effect (Allow/Deny), Action (what they can do), Resource (what they can touch), and Condition (when/where they can do it). Simple enough until you're debugging why oss:GetObject works but oss:PutObject doesn't for the same bucket.
Here's what I learned about policy structure after debugging broken permissions for 3 hours: every policy needs Version (always "1"), Statement (the actual rules), Effect (allow or deny), Principal (who gets access), Action (what they can do), Resource (what they can touch), and Condition (when/where it applies). Mess up any one piece and you're either locked out or accidentally gave someone admin access to production. Trust me, I've done both.