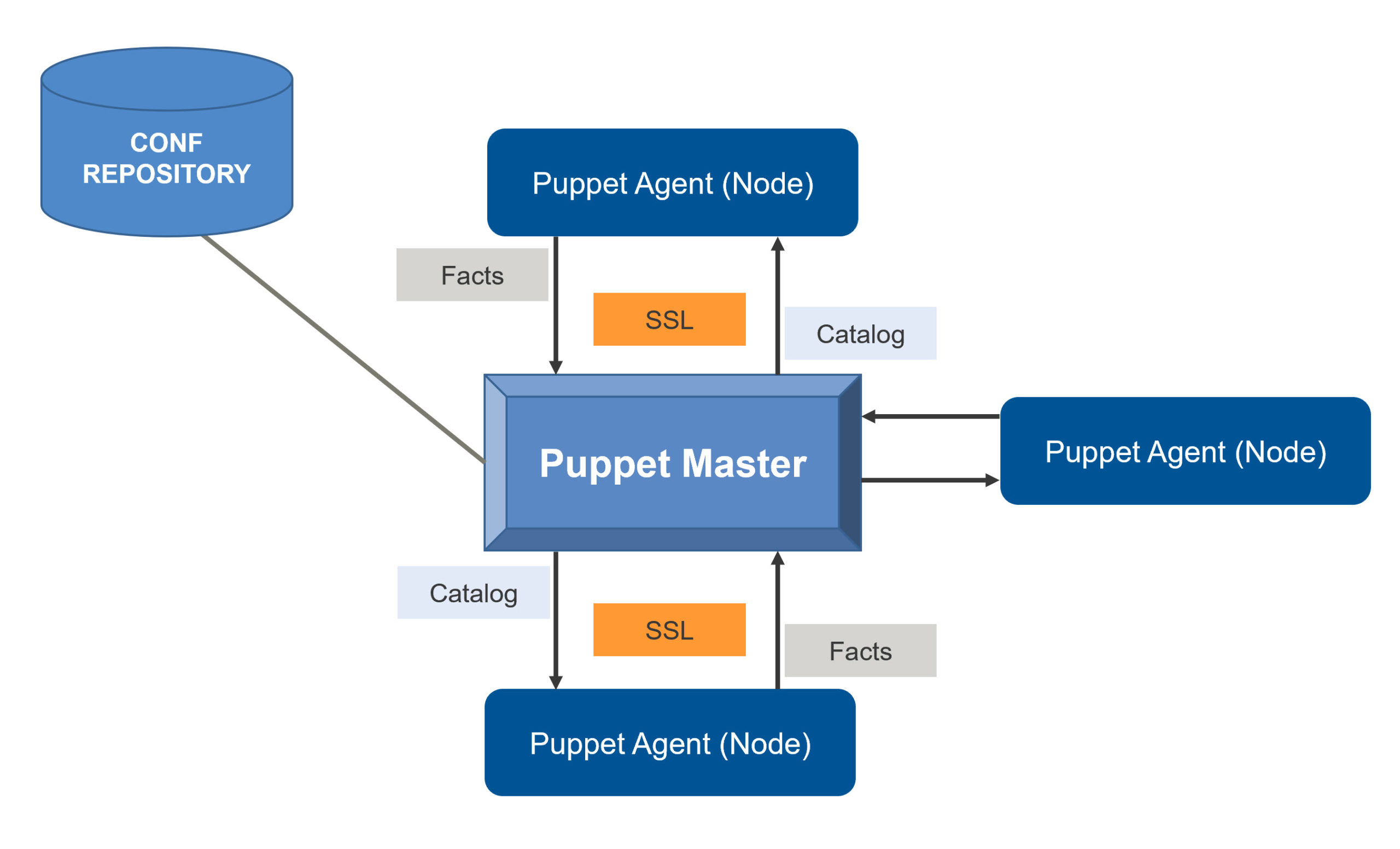
Puppet's a configuration management system that runs agents on your servers. These agents phone home to a central server every 30 minutes asking "what should I be doing?" The server looks at your Ruby-like manifest files and sends back a list of changes to make.
Been around since 2005, survived the DevOps revolution, and now lives under Perforce's corporate umbrella. Current version as of September 2025 is Puppet Enterprise 2025.5 released in August 2025. The community got pissed when they started locking down free access and announced major lifecycle changes dropping the LTS model in August 2026. The original creator Luke Kanies hasn't been involved for years.
Here's What You're Dealing With
Puppet Server sits in the middle and compiles your configs. It'll become your nemesis when SSL certs expire at exactly the worst moment - usually 3am on a Sunday when you're trying to sleep. The performance tuning guide is your bible once you hit scale.
Agents run on every box, phone home every 30 minutes asking "what should I be doing?" You'll spend a lot of time waiting during testing. Pro tip: puppet agent -t runs immediately, which you'll type about 500 times while debugging your first manifest.
Facter scans systems and reports back facts. Gets weird on containers sometimes - learned this debugging why our Docker nodes kept reporting the wrong IP addresses. The custom facts feature is useful once you figure out the Ruby syntax.
PuppetDB stores everything in PostgreSQL. Setup sucks absolute dick but the query API is actually useful once it's running. Want to know which servers have vulnerable Apache versions? PuppetDB can tell you. Want to set it up? Budget a weekend, three energy drinks, and prepare to question your life choices.
What Actually Happens During a Puppet Run
Agent wakes up every 30 minutes, connects via SSL (pray the certs work), and asks "what do you want me to do?" Facter scans the box and reports back system info. Master takes your Ruby-like manifest code and compiles it into a catalog - basically a todo list customized for that specific server.
Then the agent does the actual work: installs packages, edits config files, restarts services. If something breaks, you'll find out in the logs. If everything works, you'll still check the logs because you don't trust it yet.
During development you'll get sick of waiting 30 minutes between tests. That's when you discover puppet agent -t for immediate runs. You'll type this command approximately 1,000 times while learning Puppet, cursing every time it takes 3 minutes to tell you there's a missing comma.
Why People Use Puppet (Despite the Learning Curve)
The CIS benchmarks and compliance modules actually work well. If you need to prove security compliance, Puppet has decent pre-built policies.
Scales better than Ansible's SSH approach once you hit 100+ nodes. Multi-master setups handle thousands of servers without breaking a sweat (if configured correctly).
SSL everywhere by default. Certificate management is built-in but you'll spend more time debugging cert issues than actually configuring servers. Certificate troubleshooting becomes a skill you'll develop whether you want to or not. Welcome to the club.