Chef automates server configuration, but here's the truth: it's fucking hard to learn.
While competitors push YAML simplicity, Chef demands Ruby expertise that most ops teams don't have. If your team doesn't have Ruby skills, expect a brutal 6-month learning curve before anyone's productive. But if you've got Ruby developers on your ops team, Chef's DSL is elegant until you need to debug it during a weekend outage.
The Ruby Reality Check
Chef Infra uses a Ruby-based domain-specific language, which sounds great until your cookbook fails with a cryptic Ruby stack trace.
You're not just learning Chef
- you're learning Ruby cookbook development, dependency management, and testing frameworks.
Unlike Ansible's YAML (which anyone can read), Chef cookbooks require actual programming skills. Meta uses Chef because they have Ruby developers.
Your 3-person ops team probably doesn't.
What Actually Works (And What Breaks)
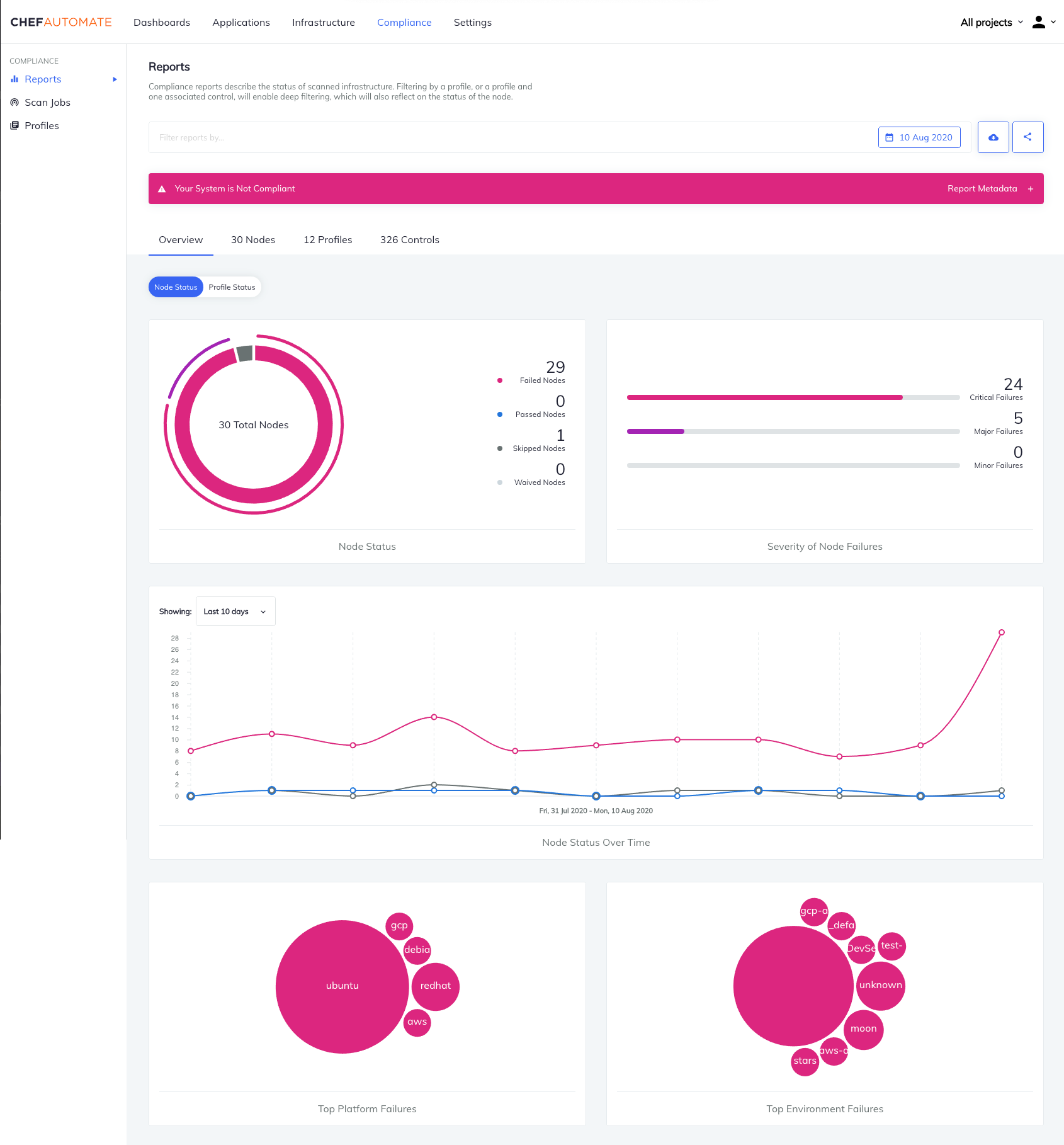
Chef Automate is legitimately good at catching security fuckups before they hit production.
The dashboard shows you which servers are drifting from policy, and InSpec catches misconfigurations automatically.

But here's what the marketing doesn't tell you:
- Chef client runs can take 2-15 minutes depending on cookbook complexity
- Ruby dependency hell during Chef upgrades (major version upgrades break shit in ways you don't expect)
- Cookbook testing requires Chef
Spec, Test Kitchen, and InSpec knowledge
- You'll see errors like `Berkshelf::
DependencyNotFound: Unable to find a solution for dependencies` constantly
LoadError: cannot load such file -- chef/mixin/powershell_outwill ruin your Windows deployments
When Chef Makes Sense (Rare But Real)
Chef works when you need:
- Strict compliance with automated remediation
- In
Spec catches violations and fixes them
- Complex configuration management across 1,000+ servers
- Ruby expertise already on your team
- Enterprise compliance requirements like SOC2, HIPAA, or PCI-DSS
Capital One uses Chef for regulatory compliance because they can afford the learning curve and have dedicated Dev
Ops teams.
Healthcare companies love Chef's compliance features, but the complexity kills small IT teams.
When to Bail vs When to Double Down
Don't use Chef if:
- You have fewer than 3 dedicated DevOps people (use Ansible instead)
- Your team wants quick wins (Chef's 6-month learning curve isn't quick)
- You're managing fewer than 100 servers (simple automation tools work better)
Use Chef when:
- You need automated compliance reporting for audits
- Configuration drift detection and automated remediation are critical
- Your team has Ruby skills or can invest in extensive training
Architecture That Actually Matters
Chef's three-tier architecture means:
- Workstations where developers write cookbooks (your laptop)
- Chef Server that coordinates everything (Erlang-based for scale)
- Nodes running chef-client every 15-30 minutes
The agent-based approach means another daemon to monitor and another service to restart when it crashes.
When chef-client fails at 3am, you're staring at Ruby stack traces trying to figure out if it's a gem version conflict or some cookbook dependency hell.
Not like Ansible where the error is "task failed, here's the command that broke."
Before you decide this complexity is worth it, consider whether your specific situation actually demands Chef's power
- or if you're just making life harder than it needs to be.
Real talk: Chef works brilliantly for regulated industries with Ruby expertise and 6+ month timelines.
Everyone else should seriously consider whether Ansible's 2-week learning curve makes more business sense than Chef's 6-month complexity tax.