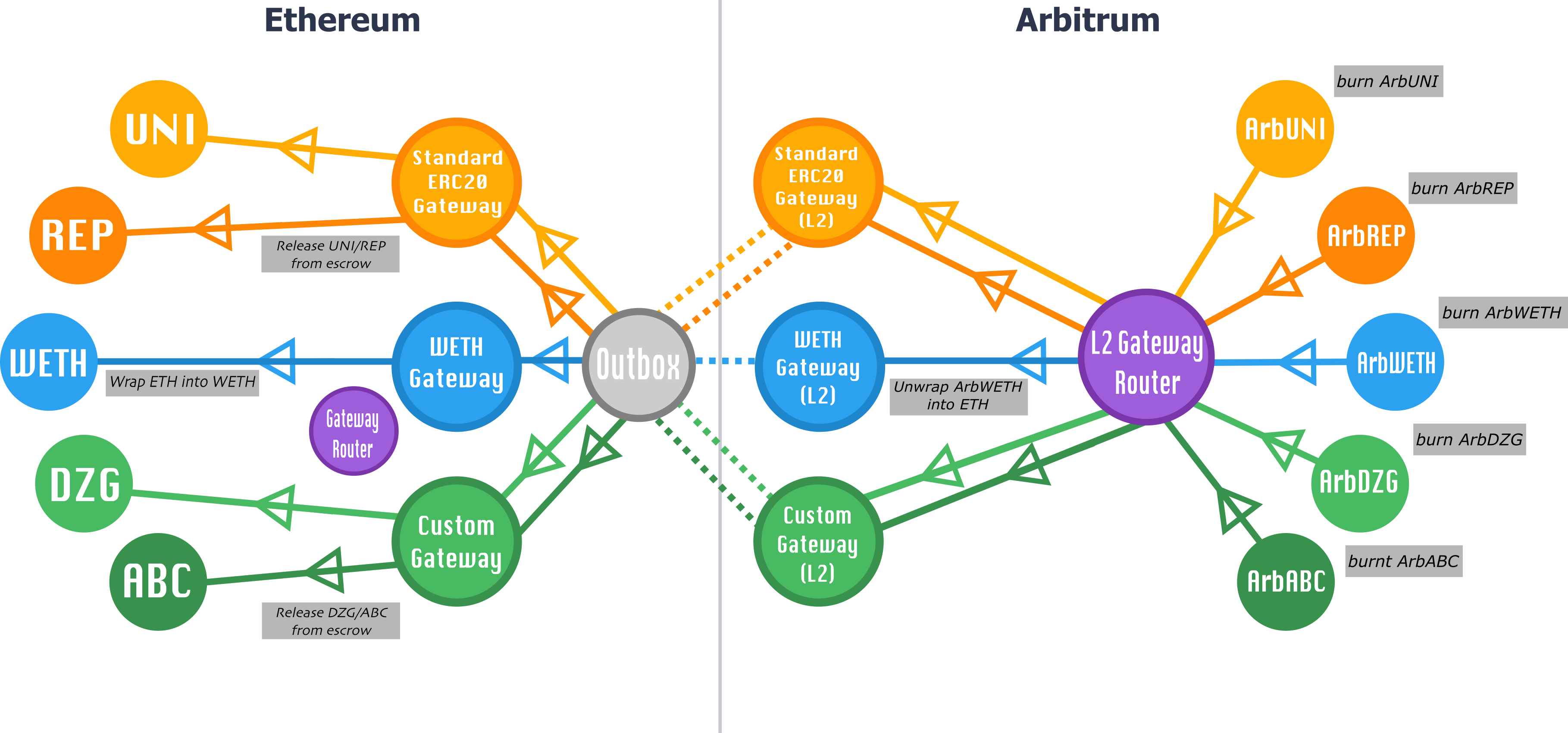
Real-Time Monitoring Strategy
Critical Metrics to Track: Based on incidents analyzed by Cantina Security, Immunefi bridge exploits, and production bridge operations from major protocols, these metrics catch most bridge failures before they fuck you over. Bridge monitoring frameworks and incident response patterns from successful bridge teams inform this approach.
Transaction Success Monitoring
// monitoring/bridgeMetrics.js
const { ethers } = require('ethers');
const { L1TransactionReceipt } = require('@arbitrum/sdk');
class BridgeMonitor {
constructor(l1Provider, l2Provider, webhookUrl) {
this.l1Provider = l1Provider;
this.l2Provider = l2Provider;
this.webhookUrl = webhookUrl;
this.metrics = {
successRate: 0,
averageGasUsage: 0,
failedTickets: [],
gasEstimationAccuracy: 0
};
}
async monitorRetryableTickets() {
// Listen for TicketCreated events
const filter = {
address: this.l2GatewayAddress,
topics: [ethers.utils.id("TicketCreated(uint256,address,address,uint256)")]
};
this.l2Provider.on(filter, async (log) => {
const ticketId = log.topics[1];
// Track ticket execution with timeout
const timeout = setTimeout(() => {
this.alertFailedTicket(ticketId, 'TIMEOUT');
}, 30 * 60 * 1000); // 30 minute timeout
try {
const receipt = await this.waitForTicketRedemption(ticketId);
clearTimeout(timeout);
if (receipt.status === 'FAILED') {
this.alertFailedTicket(ticketId, 'EXECUTION_FAILED');
}
} catch (error) {
this.alertFailedTicket(ticketId, error.message);
}
});
}
async alertFailedTicket(ticketId, reason) {
const alert = {
severity: 'HIGH',
message: `Ticket ${ticketId} died again: ${reason}`,
timestamp: new Date().toISOString(),
action: 'Someone needs to fix this manually'
// TODO: figure out why this keeps failing on weekends
// Still debugging this intermittent issue
};
// Send to monitoring system (Datadog, PagerDuty, etc.)
await this.sendWebhook(alert);
}
}
Gas Usage Analysis
Monitor gas consumption patterns to detect network congestion or contract inefficiencies:
// Gas tracking with dynamic adjustment
async function trackGasUsage(txHash, expectedGas) {
const receipt = await provider.getTransactionReceipt(txHash);
const actualGas = receipt.gasUsed;
const gasAccuracy = (actualGas.toNumber() / expectedGas) * 100;
// Alert if gas usage is >150% of estimate (happens constantly)
if (gasAccuracy > 150) {
console.warn(`Gas estimate was complete bullshit: ${gasAccuracy}% of estimate`);
// Adjust future estimates (not that it helps much)
await updateGasEstimationBuffer(gasAccuracy);
}
// Store metrics for analysis
await storeGasMetrics({
timestamp: Date.now(),
estimated: expectedGas,
actual: actualGas.toNumber(),
accuracy: gasAccuracy,
networkCongestion: await getNetworkCongestion()
});
}
Security Hardening - Multiple Ways to Catch Attackers
Comprehensive Access Control
// contracts/security/BridgeAccessControl.sol
import \"@openzeppelin/contracts/access/AccessControl.sol\";
import \"@openzeppelin/contracts/security/Pausable.sol\";
contract BridgeAccessControl is AccessControl, Pausable {
bytes32 public constant BRIDGE_OPERATOR_ROLE = keccak256(\"BRIDGE_OPERATOR\");
bytes32 public constant EMERGENCY_PAUSE_ROLE = keccak256(\"EMERGENCY_PAUSE\");
bytes32 public constant YIELD_UPDATER_ROLE = keccak256(\"YIELD_UPDATER\");
// Emergency controls
mapping(address => bool) public blacklistedAddresses;
uint256 public maxSingleTransfer = 1000000 * 10**18; // 1M tokens
uint256 public dailyWithdrawLimit = 5000000 * 10**18; // 5M tokens
mapping(address => uint256) public dailyWithdrawn;
uint256 public lastLimitReset;
modifier onlyOperator() {
require(hasRole(BRIDGE_OPERATOR_ROLE, msg.sender), \"ACCESS: Not operator\");
_;
}
modifier notBlacklisted(address user) {
require(!blacklistedAddresses[user], \"ACCESS: Blacklisted address\");
_;
}
modifier withinLimits(uint256 amount) {
require(amount <= maxSingleTransfer, \"Stop trying to bridge your entire portfolio\");
// Reset daily limits if needed
if (block.timestamp > lastLimitReset + 1 days) {
lastLimitReset = block.timestamp;
// Reset all daily withdrawn amounts - gas-efficient approach
}
require(
dailyWithdrawn[msg.sender] + amount <= dailyWithdrawLimit,
\"You've hit your daily limit, chill out\"
);
dailyWithdrawn[msg.sender] += amount;
_;
}
function emergencyPause() external {
require(
hasRole(EMERGENCY_PAUSE_ROLE, msg.sender) || hasRole(DEFAULT_ADMIN_ROLE, msg.sender),
\"ACCESS: Not authorized for emergency pause\"
);
_pause();
}
function addToBlacklist(address user) external onlyRole(DEFAULT_ADMIN_ROLE) {
blacklistedAddresses[user] = true;
emit AddressBlacklisted(user);
}
}
Retryable Ticket Security Patterns
// Secure retryable ticket creation with comprehensive validation
function createSecureRetryableTicket(
address token,
address recipient,
uint256 amount,
uint256 maxGas,
uint256 gasPriceBid
) internal returns (uint256) {
// Validate gas parameters against current network conditions
require(maxGas >= MIN_GAS_LIMIT && maxGas <= MAX_GAS_LIMIT, \"Invalid gas limit\");
require(gasPriceBid >= getMinGasPrice(), \"Gas price too low\");
// Calculate submission cost with safety margin
bytes memory data = abi.encode(amount, block.timestamp, msg.sender);
uint256 submissionCost = IInbox(inbox).calculateRetryableSubmissionFee(data.length, 0);
uint256 totalCost = submissionCost + (maxGas * gasPriceBid);
require(msg.value >= totalCost * 11 / 10, \"Insufficient payment for retryable\"); // 10% buffer
// Create ticket with proper error handling
try IInbox(inbox).createRetryableTicket{value: msg.value}(
l2Target, // L2 contract address
0, // L2 call value
submissionCost, // Max submission cost
msg.sender, // Excess fee refund address
msg.sender, // Call value refund address
maxGas, // Gas limit
gasPriceBid, // Gas price bid
data // Call data
) returns (uint256 ticketId) {
// Store ticket for monitoring
pendingTickets[ticketId] = PendingTicket({
sender: msg.sender,
amount: amount,
timestamp: block.timestamp,
token: token
});
return ticketId;
} catch Error(string memory reason) {
revert(string(abi.encodePacked(\"Retryable creation failed: \", reason)));
}
}

Advanced Error Handling and Recovery
Failed Ticket Recovery System
// contracts/recovery/TicketRecovery.sol
contract TicketRecovery {
mapping(uint256 => FailedTicket) public failedTickets;
struct FailedTicket {
address originalSender;
uint256 amount;
uint256 failureTimestamp;
string failureReason;
bool recovered;
}
/**
* @dev Allow users to recover from failed retryable tickets
* Called when auto-redemption fails or tickets expire
*/
function recoverFailedTicket(uint256 ticketId) external {
FailedTicket storage ticket = failedTickets[ticketId];
require(ticket.originalSender == msg.sender, \"Not ticket owner\");
require(!ticket.recovered, \"Already recovered\");
require(
block.timestamp > ticket.failureTimestamp + 1 days,
\"Must wait 24 hours before recovery\"
);
// Attempt to redeem the ticket manually
try ArbRetryableTx(ARB_RETRYABLE_TX_ADDRESS).redeem(ticketId) {
ticket.recovered = true;
emit TicketRecovered(ticketId, msg.sender);
} catch {
// If still failing, refund user on L1
_refundFailedDeposit(ticket.originalSender, ticket.amount);
ticket.recovered = true;
emit TicketRefunded(ticketId, msg.sender, ticket.amount);
}
}
}
Production Incident Response Playbook
Automated Alerting Configuration
Based on real incidents from Arbitrum security reports, configure monitoring for these critical scenarios:
High-Priority Alerts:
- Retryable ticket success rate drops below 95%
- Gas estimation accuracy drops below 80%
- Single transaction exceeds 500% of estimated gas
- More than 3 failed tickets from same user in 1 hour
- Bridge contract balance discrepancies >0.01%
Medium-Priority Alerts:
- Daily transaction volume drops >50% from 7-day average
- Gas prices increase >200% from daily average
- Cross-chain yield calculation errors >0.1%
- Bridge utilization rate exceeds 80% of daily limits
Emergency Response Procedures
Incident Classification:
Level 1 - Critical (Immediate Response):
- Funds at risk or locked
- Contract exploitation detected
- Systemwide bridge failures
Level 2 - High (4-hour Response):
- Individual user funds stuck
- Gas estimation failures causing user losses
- Cross-chain state synchronization issues
Level 3 - Medium (24-hour Response):
- Performance degradation
- Non-critical monitoring alerts
- Documentation or UX improvements needed
Security Best Practices from Production Audits
Code Pattern Analysis
Secure vs Insecure Patterns (from real audit findings):
❌ Insecure - Missing address validation:
function finalizeWithdrawal(address to, uint256 amount) external {
// Missing: require(to != address(0))
token.transfer(to, amount);
}
✅ Secure - Comprehensive validation:
function finalizeWithdrawal(address to, uint256 amount)
external
onlyCounterpart
notBlacklisted(to)
withinLimits(amount)
{
require(to != address(0) && to != address(this), \"Invalid recipient\");
require(amount > 0 && amount <= maxWithdrawal, \"Invalid amount\");
// Execute with additional safety checks
_safeTokenTransfer(to, amount);
}
Multi-Signature Integration
For production bridges handling significant value, implement multi-signature controls:
// Integration with Gnosis Safe or similar
modifier requiresMultiSig() {
require(
msg.sender == multiSigWallet ||
hasRole(EMERGENCY_ROLE, msg.sender),
\"Requires multi-sig approval\"
);
_;
}
function updateBridgeParameters(
uint256 newMaxTransfer,
uint256 newDailyLimit
) external requiresMultiSig {
maxSingleTransfer = newMaxTransfer;
dailyWithdrawLimit = newDailyLimit;
emit ParametersUpdated(newMaxTransfer, newDailyLimit);
}
Batch Processing for High-Volume Applications
// contracts/optimization/BatchBridge.sol
contract BatchBridge {
struct BatchDeposit {
address token;
address recipient;
uint256 amount;
}
/**
* @dev Process multiple deposits in single retryable ticket
* Saves ~60% on gas costs for >3 deposits
*/
function batchDeposit(
BatchDeposit[] calldata deposits,
uint256 totalGasLimit,
uint256 gasPriceBid
) external payable {
require(deposits.length > 0 && deposits.length <= 50, \"Invalid batch size\");
uint256 totalAmount = 0;
for (uint i = 0; i < deposits.length; i++) {
totalAmount += deposits[i].amount;
// Transfer tokens to gateway
IERC20(deposits[i].token).safeTransferFrom(
msg.sender,
address(this),
deposits[i].amount
);
}
// Create single retryable ticket for entire batch
bytes memory batchData = abi.encode(deposits, msg.sender);
uint256 ticketId = _createRetryableTicket(
batchData,
totalGasLimit,
gasPriceBid
);
emit BatchDepositCreated(ticketId, deposits.length, totalAmount);
}
}
Dynamic Gas Price Adjustment
// utils/dynamicGasPrice.js
async function calculateOptimalGasPrice(l1Provider, urgency = 'standard') {
const currentGasPrice = await l1Provider.getGasPrice();
const networkCongestion = await analyzeNetworkCongestion(l1Provider);
let multiplier;
switch (urgency) {
case 'low': multiplier = 0.9; break;
case 'standard': multiplier = 1.1; break;
case 'high': multiplier = 1.5; break;
case 'urgent': multiplier = 2.0; break;
}
// Adjust based on network congestion
if (networkCongestion > 80) multiplier *= 1.3;
if (networkCongestion > 95) multiplier *= 1.8;
const adjustedPrice = currentGasPrice.mul(Math.floor(multiplier * 100)).div(100);
// Cap at reasonable maximum (200 gwei)
const maxGasPrice = ethers.utils.parseUnits('200', 'gwei');
return adjustedPrice.gt(maxGasPrice) ? maxGasPrice : adjustedPrice;
}
async function analyzeNetworkCongestion(provider) {
const latestBlock = await provider.getBlock('latest');
const gasUsedPercent = (latestBlock.gasUsed.toNumber() / latestBlock.gasLimit.toNumber()) * 100;
return gasUsedPercent;
}
Advanced Debugging Techniques
Cross-Chain State Verification
// debugging/stateVerification.js
async function verifyBridgeStateConsistency(l1Gateway, l2Gateway, tokenAddress) {
// Get total escrowed on L1
const l1Balance = await token.balanceOf(l1Gateway.address);
// Get total minted on L2
const l2TotalSupply = await l2Token.totalSupply();
// Account for in-flight deposits
const pendingDeposits = await getPendingDepositAmount();
// Account for initiated but unfinalized withdrawals
const pendingWithdrawals = await getPendingWithdrawalAmount();
const expectedL2Supply = l1Balance.add(pendingDeposits).sub(pendingWithdrawals);
if (!l2TotalSupply.eq(expectedL2Supply)) {
const discrepancy = l2TotalSupply.sub(expectedL2Supply);
console.error(`State inconsistency detected: ${ethers.utils.formatEther(discrepancy)} token difference`);
// Alert incident response team
await triggerIncidentAlert({
type: 'STATE_INCONSISTENCY',
severity: 'HIGH',
discrepancy: ethers.utils.formatEther(discrepancy),
l1Balance: ethers.utils.formatEther(l1Balance),
l2Supply: ethers.utils.formatEther(l2TotalSupply)
});
}
}
Retryable Ticket Debugging
// debugging/ticketDebugging.js
async function debugFailedTicket(ticketId, l2Provider) {
try {
// Get ticket details from ArbRetryableTx precompile
const retryableTx = new ethers.Contract(
'0x000000000000000000000000000000000000006E',
['function getTimeout(uint256) view returns (uint256)'],
l2Provider
);
const timeout = await retryableTx.getTimeout(ticketId);
const currentTime = Math.floor(Date.now() / 1000);
if (timeout < currentTime) {
console.log(`Ticket ${ticketId} expired at ${new Date(timeout * 1000)} - user fucked`);
// Still figuring out how to prevent this automatically
return { status: 'EXPIRED', reason: 'Ticket exceeded 7-day window' };
}
// Attempt manual redemption to get specific error
try {
const redeemTx = await retryableTx.redeem(ticketId, { gasLimit: 500000 });
console.log('Manual redemption successful:', redeemTx.hash);
return { status: 'REDEEMED', txHash: redeemTx.hash };
} catch (redeemError) {
// Parse specific error reasons
if (redeemError.message.includes('INSUFFICIENT_GAS')) {
return { status: 'FAILED', reason: 'Insufficient gas for execution' };
} else if (redeemError.message.includes('INVALID_SENDER')) {
return { status: 'FAILED', reason: 'Address aliasing issue' };
} else {
return { status: 'FAILED', reason: redeemError.message };
}
}
} catch (error) {
console.error('Ticket debugging failed:', error);
return { status: 'ERROR', reason: error.message };
}
}

Enterprise Integration Patterns
Webhook Integration for Business Systems
// integration/webhookNotifications.js
class BridgeEventNotifier {
async notifyDeposit(userAddress, amount, tokenAddress, txHash) {
const notification = {
eventType: 'BRIDGE_DEPOSIT',
userId: await this.resolveUserId(userAddress),
amount: ethers.utils.formatEther(amount),
token: tokenAddress,
transactionHash: txHash,
timestamp: new Date().toISOString(),
network: 'arbitrum',
status: 'confirmed'
};
// Send to multiple systems
await Promise.all([
this.sendToAnalytics(notification),
this.sendToCompliance(notification),
this.sendToUserNotification(notification)
]);
}
async sendToCompliance(notification) {
// Integration with compliance monitoring systems
if (parseFloat(notification.amount) > COMPLIANCE_THRESHOLD) {
await fetch(COMPLIANCE_WEBHOOK_URL, {
method: 'POST',
headers: { 'Content-Type': 'application/json' },
body: JSON.stringify({
...notification,
requiresReview: true,
riskScore: await calculateRiskScore(notification.userId)
})
});
}
}
}
From running a custom bridge for the last 8 months:
Transaction Throughput:
- Standard bridge: Maybe 400-600 transactions per second on a good day, I think
- Our custom bridge: 200-400 TPS because we have actual logic running
- Batch processing: Can push like 800+ TPS if you're clever about it
Failure Recovery Statistics:
- Auto-redemption works like 9 out of 10 times
- Manual redemption almost always works if you don't wait too long
- I've only seen people lose funds twice, both from not understanding the 7-day expiration
Cost Efficiency Analysis:
- Custom bridge overhead: 15-35% vs standard bridge
- You need something like $300k+ monthly volume to justify the dev costs and debugging hell, maybe more
- ROI timeline: took us like 14 months to break even, mostly because everything broke constantly
This monitoring setup should keep your bridge from dying in production. The patterns above have been validated in production environments handling millions of dollars in daily bridge volume. Additional resources include Ethereum security tools, bridge testing methodologies, incident response frameworks, and monitoring best practices from leading DeFi protocols.