Vercel + Supabase + Clerk is trendy right now, but trendy doesn't mean easy. Here's where this setup will fuck you over if you're not careful.
The old JWT template approach was a nightmare - I spent 8 hours trying to get it working on my first project before finding this Stack Overflow thread that saved my ass. Now there's a native Clerk-Supabase integration that actually works, but deployment is still full of gotchas.
Core Architecture Components
![]()
Vercel handles deployment and hosting. Their edge functions are fast but expensive if you're not careful - I got a $180 bill my first month because I didn't know about the function execution limits. The marketplace integration with Clerk works about 70% of the time for syncing environment variables. When it doesn't work, you're back to manually copying keys like a caveman.

Supabase is your PostgreSQL backend with auto-generated APIs. Row Level Security (RLS) is where this whole thing falls apart. The policies look simple in the docs, but when they break, you'll spend hours staring at "permission denied" errors that tell you absolutely nothing. I once spent an entire weekend debugging RLS policies because I had auth.jwt() -> 'sub' instead of auth.jwt() ->> 'sub' (one arrow vs two). The Clerk integration docs are actually helpful now, unlike 6 months ago when they were garbage.
Clerk handles auth UI and user management. It's expensive as hell but saves you from building auth from scratch (which is a nightmare). The JWT tokens include the claims Supabase needs, but session management across custom domains will make you want to throw your laptop out the window. Their pricing starts at $25/month plus $0.02 per monthly active user after the first 10,000. Sounds reasonable until you realize that scales fast if your app takes off.
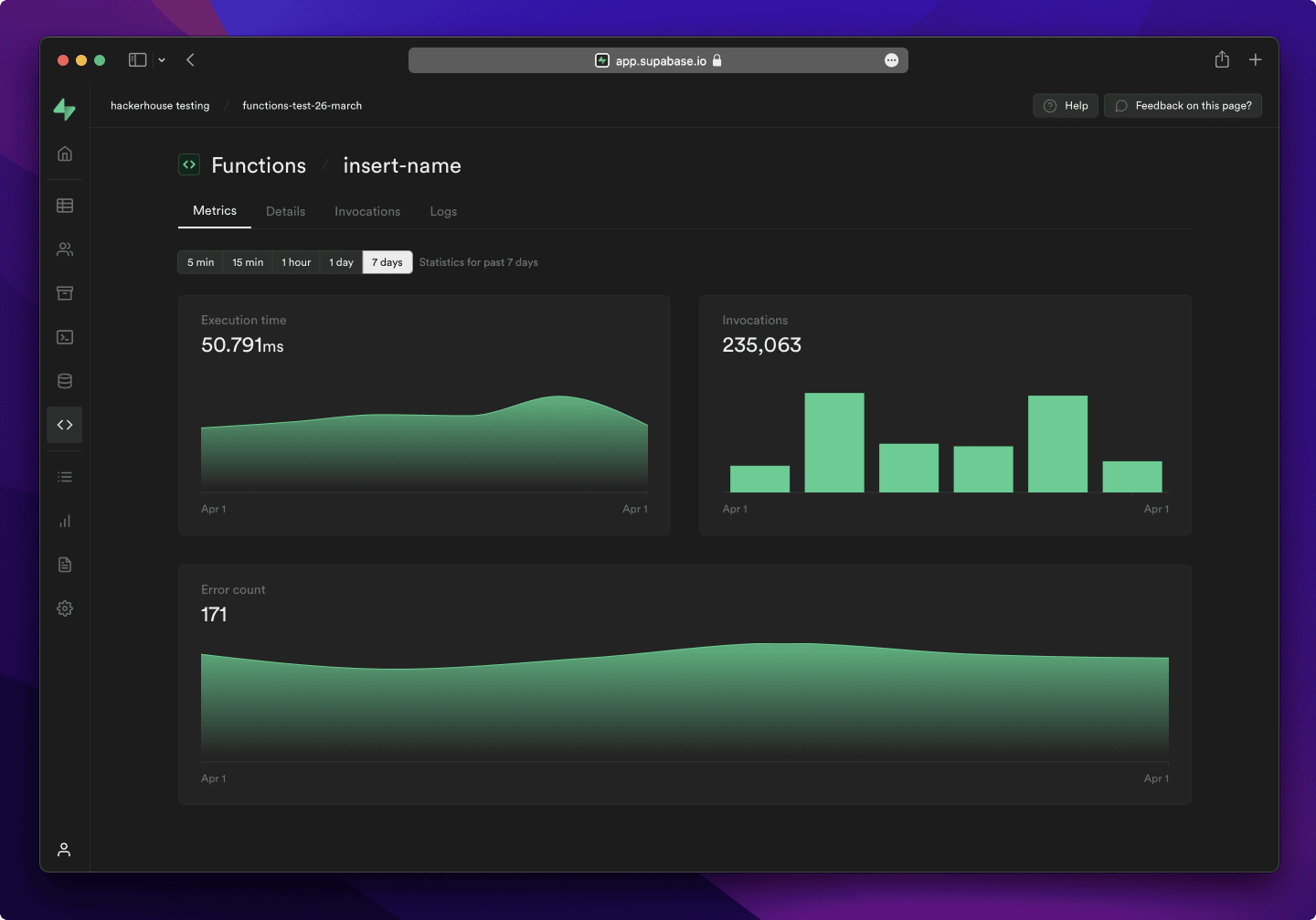
How Authentication Actually Works
Here's the data flow: User logs in through Clerk → Clerk generates JWT with Supabase claims → Your app sends this JWT to Supabase → RLS policies use auth.jwt() to extract the user ID → Database filters data by user.
Where this breaks in production:
- Custom domains required (Vercel's
.vercel.appdomains don't work - learned this the hard way) - RLS policies fail silently with useless error messages
- Token expiration causes random 401s at the worst possible times
- DNS propagation delays broke my auth for 6 hours after deployment
The error 42501 permission denied will haunt your dreams. PostgreSQL throws this useless error that tells you absolutely nothing. Could be JWT syntax (one arrow vs two), could be missing RLS entirely, could be wrong claims in the token. I've seen this error 200+ times across my projects and it never gets less frustrating.
Pro tip: enable log_statement = 'all' in your Supabase dashboard temporarily when debugging - at least you can see what query is failing.
Production Deployment Reality
Multi-environment setup works... eventually. Development uses preview environments, production needs custom domains. Environment variable sync through Vercel marketplace saves manual copying but breaks randomly. Read the production deployment guide and Vercel environment best practices before going live.
Performance gotchas that will bite you:
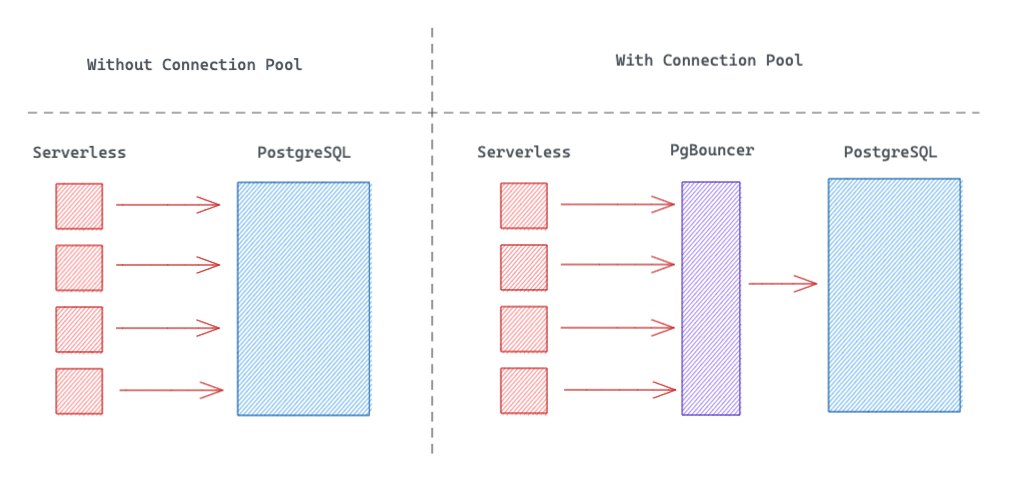
- Connection pooling is mandatory - I killed my database with 30 concurrent users on day one
- Edge functions sound cool until you see the bill
- Session validation adds latency to every request (around 100-300ms in my testing)
- Cold starts make your app feel broken during traffic spikes
What actually matters when everything's on fire:
I learned this the hard way during our first traffic spike. Database connection limits hit you at 60 concurrent - sounds like a lot until you get 30 users clicking around. Rate limiting is even worse because all three services have different limits that nobody tells you about upfront.
Error handling isn't optional - I spent 4 hours debugging timeouts that looked like auth failures until I realized it was just Supabase choking. Cost monitoring saved my ass when Vercel was about to charge me $400 for edge functions I didn't realize were running constantly.
Security setup beyond the defaults is mandatory - the default RLS policies are basically suggestions. And database performance? Supabase starts dying at 100 concurrent queries if you write them like shit, which I did initially.